On March 29, 2023, a number of security companies were warned about harmful activity that was traced back to a legitimate binary file from the communication technology firm 3CX. The file, called 3CXDesktopApp, is a popular video-conferencing software that can be downloaded on different platforms. Several analyses have attributed the threat campaign to state-sponsored threat actors, and security firms have observed malicious activity in both Windows and Mac environments.
On Thursday, March 30th, 3CX confirmed that multiple versions of its desktop app for Windows and macOS were affected by a supply chain attack. The version numbers include 18.12.407 and 18.12.416 for Windows and 18.11.1213, 18.12.402, 18.12.407, and 18.12.416 for macOS.
This post will describe how to use Netskope to identify possible indicators of use (IOUs) of the 3CX desktop app, indicators of compromise (IOCs), and how to mitigate any further malicious activity.
Indicators of Use
If you are uncertain about the usage of the 3CX desktop app within your organization, this section shows how to identify possible usage of the app.
1. Open Cloud Confidence Index (CCI) and search for 3CX.
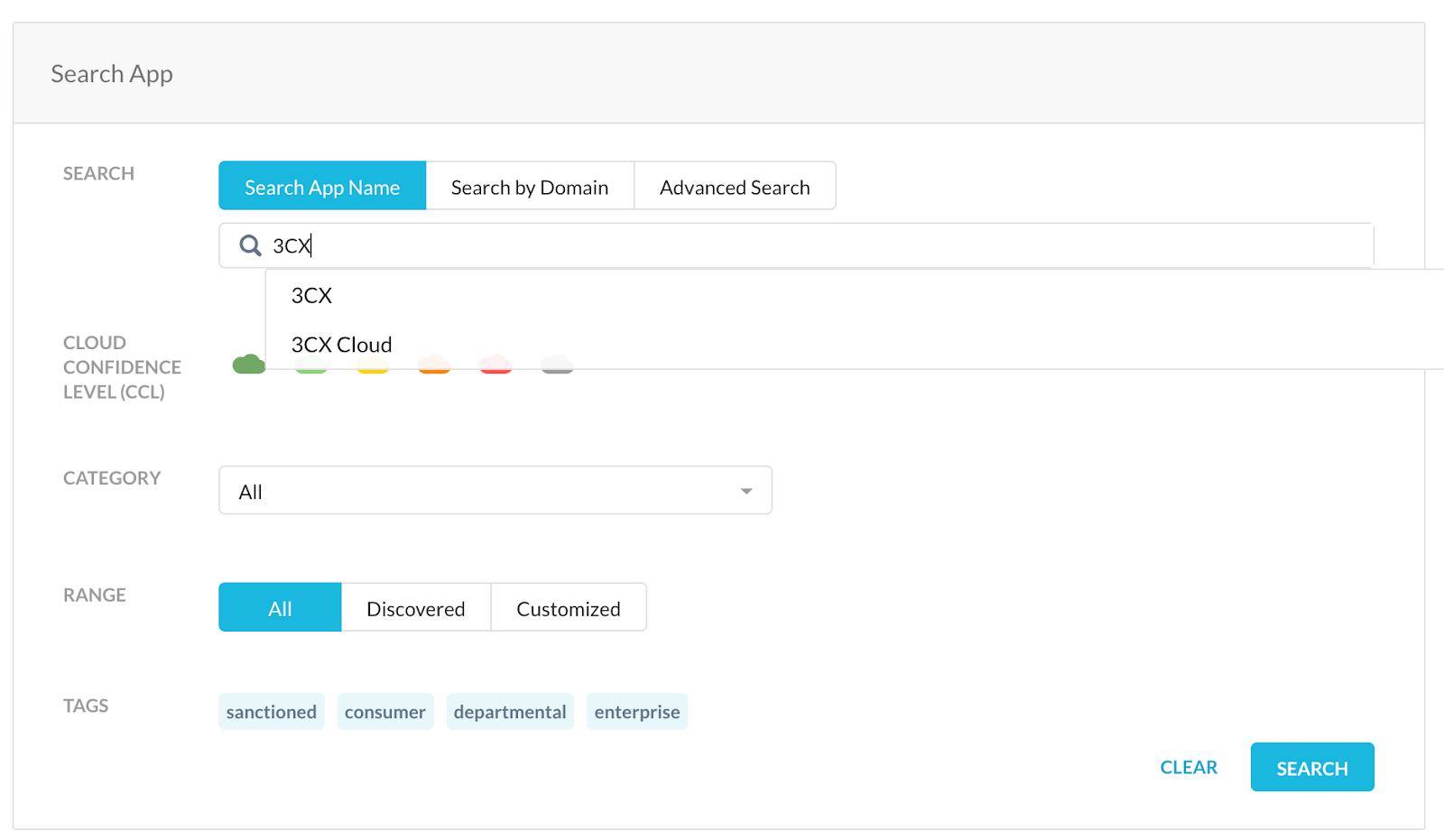
2. Select the 3CX app.
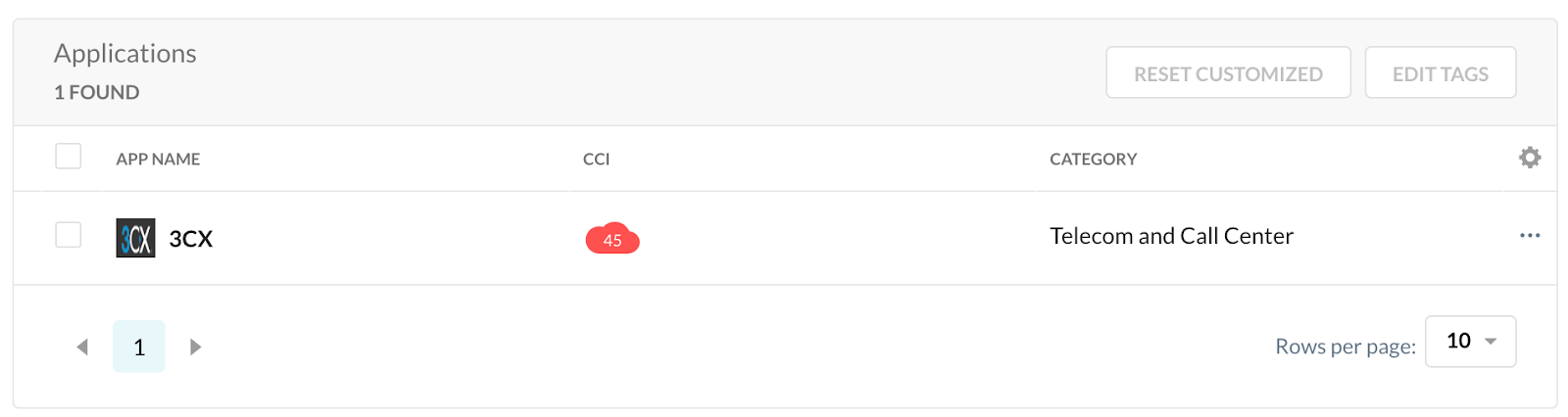
3. Click “Usage and Risk”
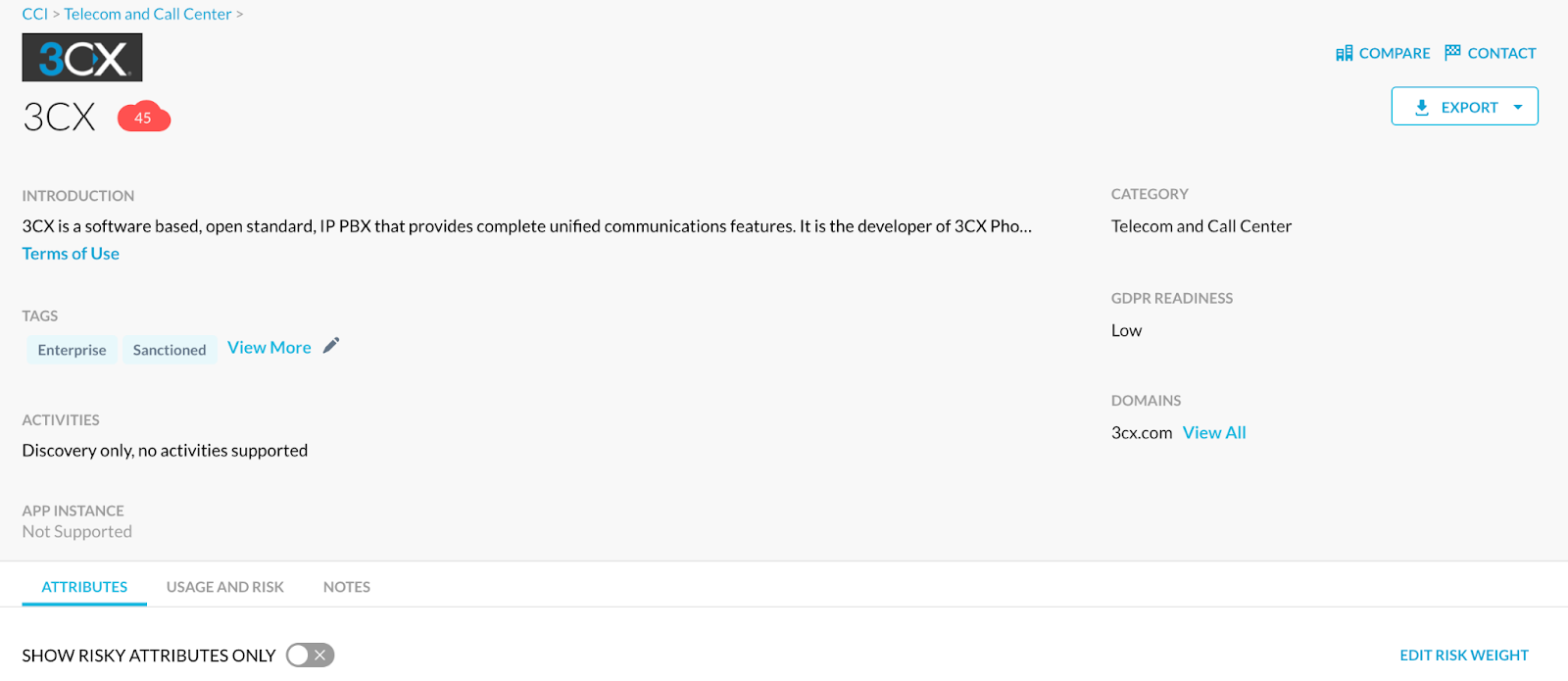
4. Shown below is some example data from the query.
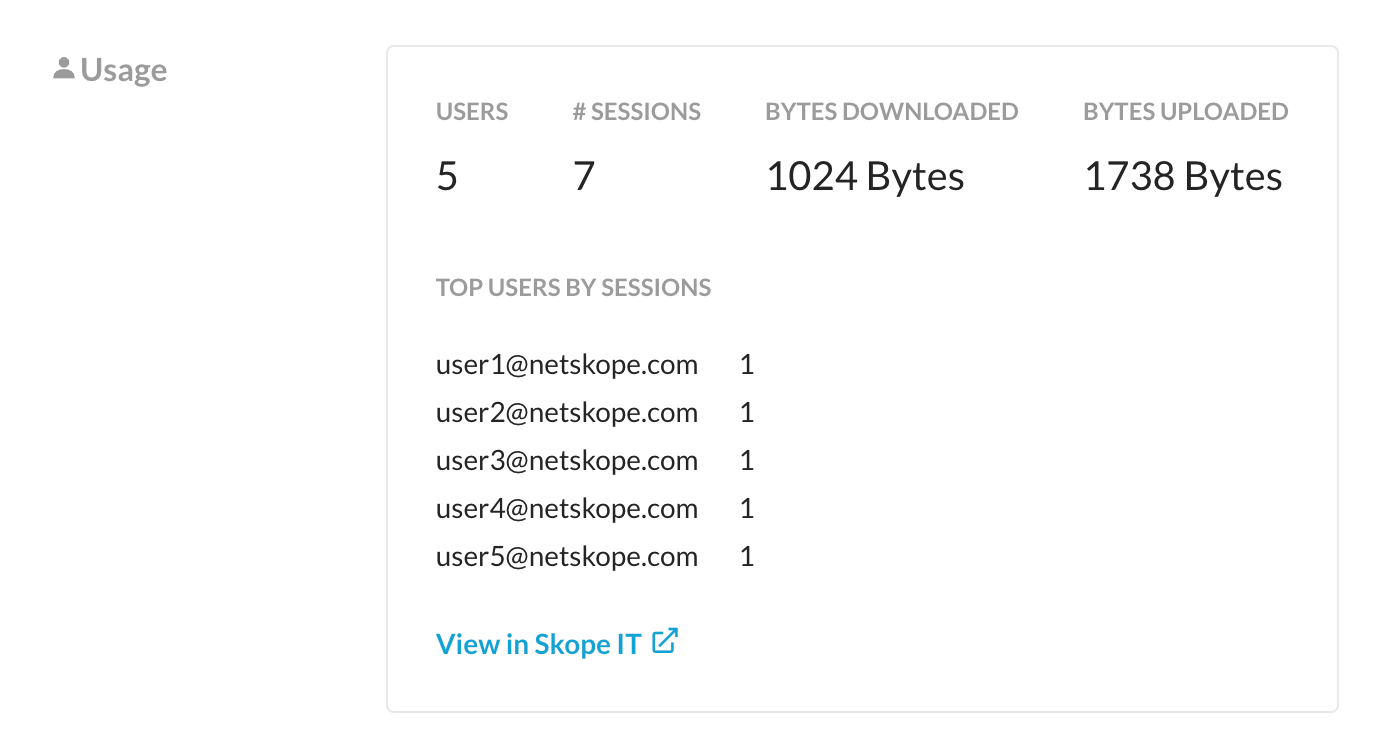
5. To investigate the findings further, click “View in SkopeIT”. Once in SkopeIT, change the view to Page Events in the top right.
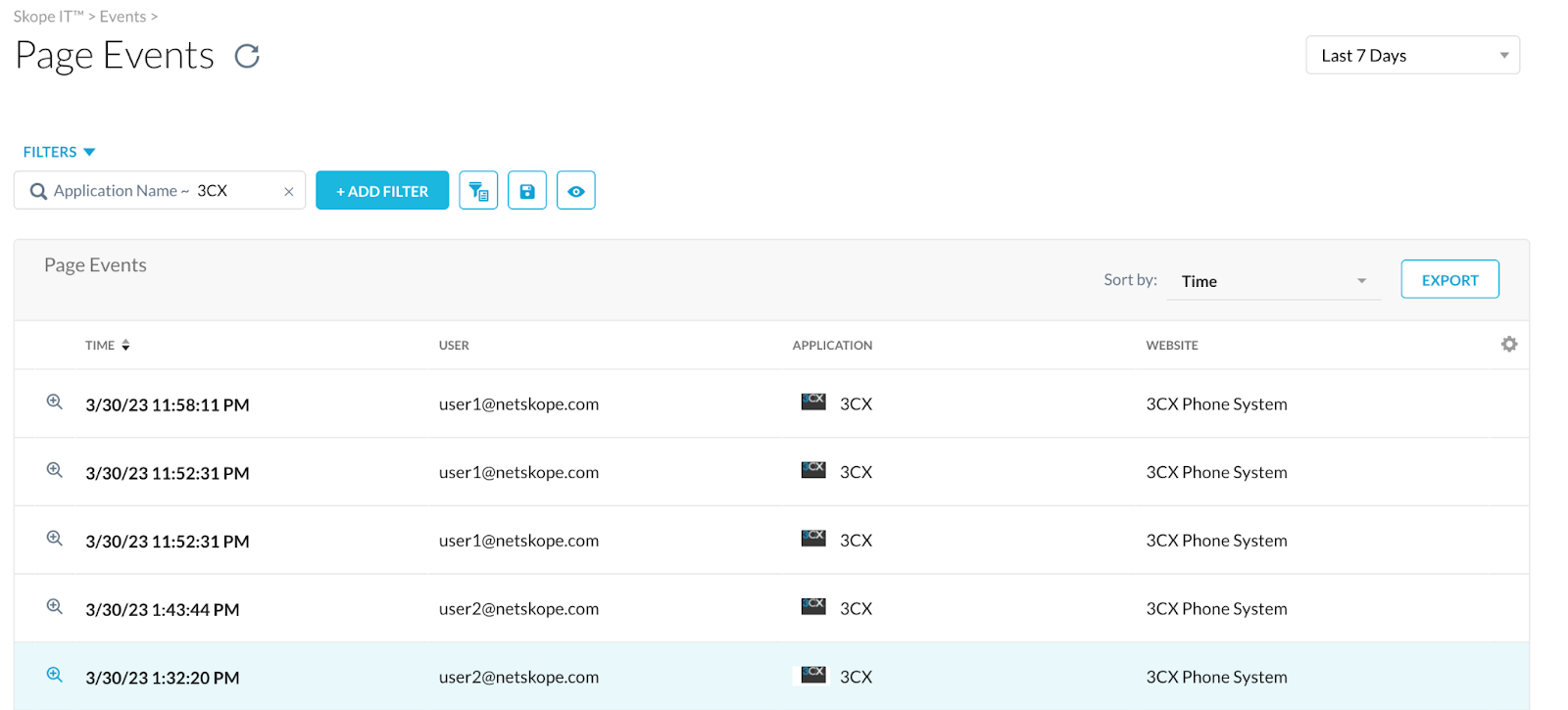
Netskope Page Events can be used to further determine if the application is in use based on login activity and basic web traffic such as visiting the site. In the screenshot below we can see the user visiting the login portal for the application. With this information teams should further investigate to confirm applications usage using their endpoint solution.

Indicators of Compromise
If you would like to look for indicators of compromise from the malicious 3CX desktop app, this section will walk through performing that hunt.
A non-comprehensive list of IOCs for the malicious 3CX desktop app versions can be found below:
Domains:
- akamaicontainer[.]com
- akamaitechcloudservices[.]com
- azuredeploystore[.]com
- azureonlinecloud[.]com
- azureonlinestorage[.]com
- convieneonline[.]com
- dunamistrd[.]com
- glcloudservice[.]com
- journalide[.]org
- msedgepackageinfo[.]com
- msstorageazure[.]com
- msstorageboxes[.]com
- officeaddons[.]com
- officestoragebox[.]com
- pbxcloudeservices[.]com
- pbxphonenetwork[.]com
- pbxsources[.]com
- qwepoi123098[.]com
- sbmsa[.]wiki
- sourceslabs[.]com
- Soyoungjun[.]com
- visualstudiofactory[.]com
- Zacharryblogs[.]com
File Hashses:
- Compromised MSI: aa124a4b4df12b34e74ee7f6c683b2ebec4ce9a8edcf9be345823b4fdcf5d868
- 3CXDesktopApp.exe: fad482ded2e25ce9e1dd3d3ecc3227af714bdfbbde04347dbc1b21d6a3670405
- ffmpeg.dll: 7986bbaee8940da11ce089383521ab420c443ab7b15ed42aed91fd31ce833896
- d3dcompiler_47.dll: 11be1803e2e307b647a8a7e02d128335c448ff741bf06bf52b332e0bbf423b03
1. Open Netskope’s Advanced Analytics and navigate to the Explore tab.
2. On the top right, choose which data collection you would like to search from. 
3. Now we can start crafting our query. For this example we will add the domain, user, user IP, event date, and event URI to our query. Search for each of these attributes and click on them to add them to the query.
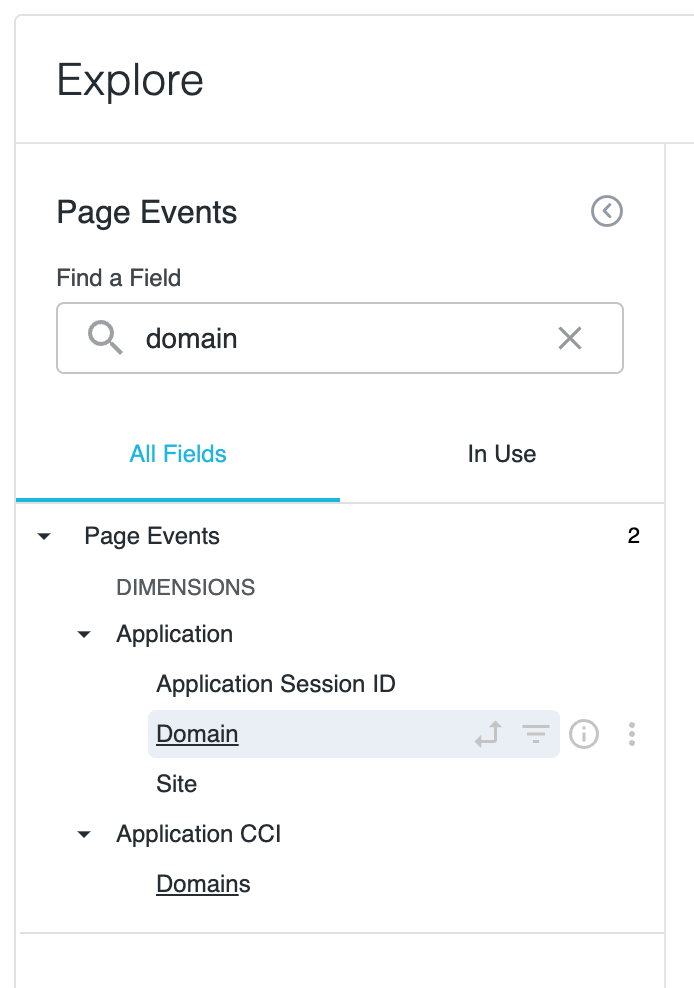
4. Search for domain and click “Filter by field”. This will allow us to search for findings given a domain.
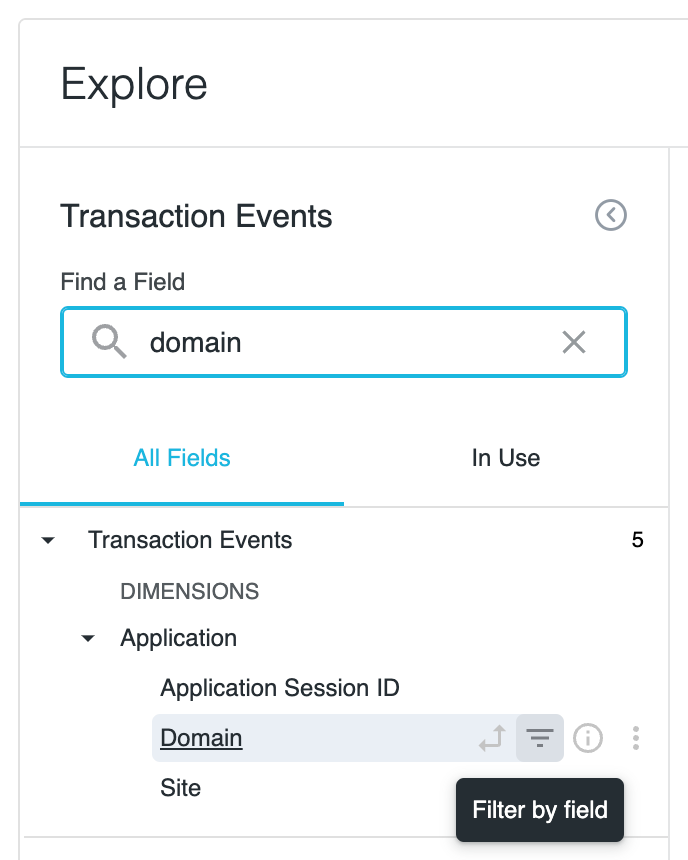
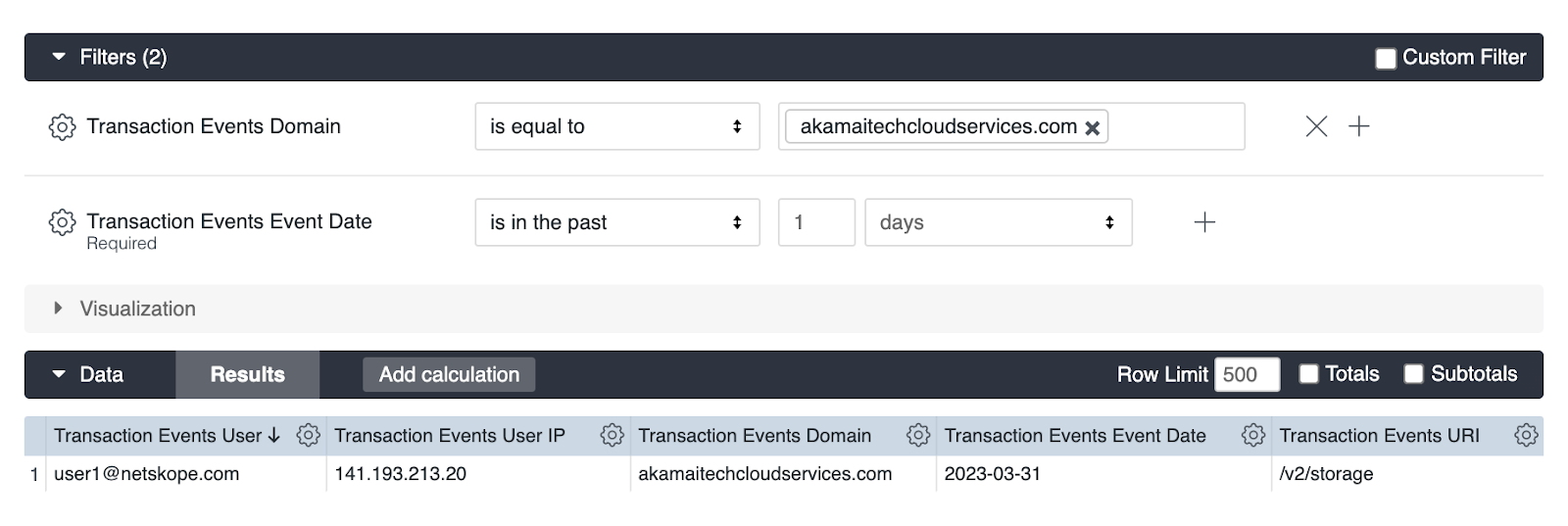
5. Enter the IOC domains you would like to search for and click run. If you see any events involving the IOC domains, that likely means there is malicious activity occurring. Below is an example finding given a legitimate IOC:
Mitigation Actions
The appropriate mitigation strategy would be to uninstall 3CXDesktopApp on all platforms and remove any artifacts left behind. Users should retroactively hunt for indicators of compromise and block known-bad domains along with the known-bad file hashes.
To block known-bad domains, follow the instructions on this article: https://docs.netskope.com/en/filtering-top-level-domains.html
To block known-bad file hashes, follow the instructions on these articles:
https://docs.netskope.com/en/creating-a-file-hash-list.html
https://docs.netskope.com/en/creating-a-malware-detection-profile.html







