Hi all,
because of privacy reasons, we don’t want Netskope to pass along the X-Forwarded-For-Header containing the public IP address of our users to the Internet..
The following website tests can be used to prove that Netskope always provides this information.
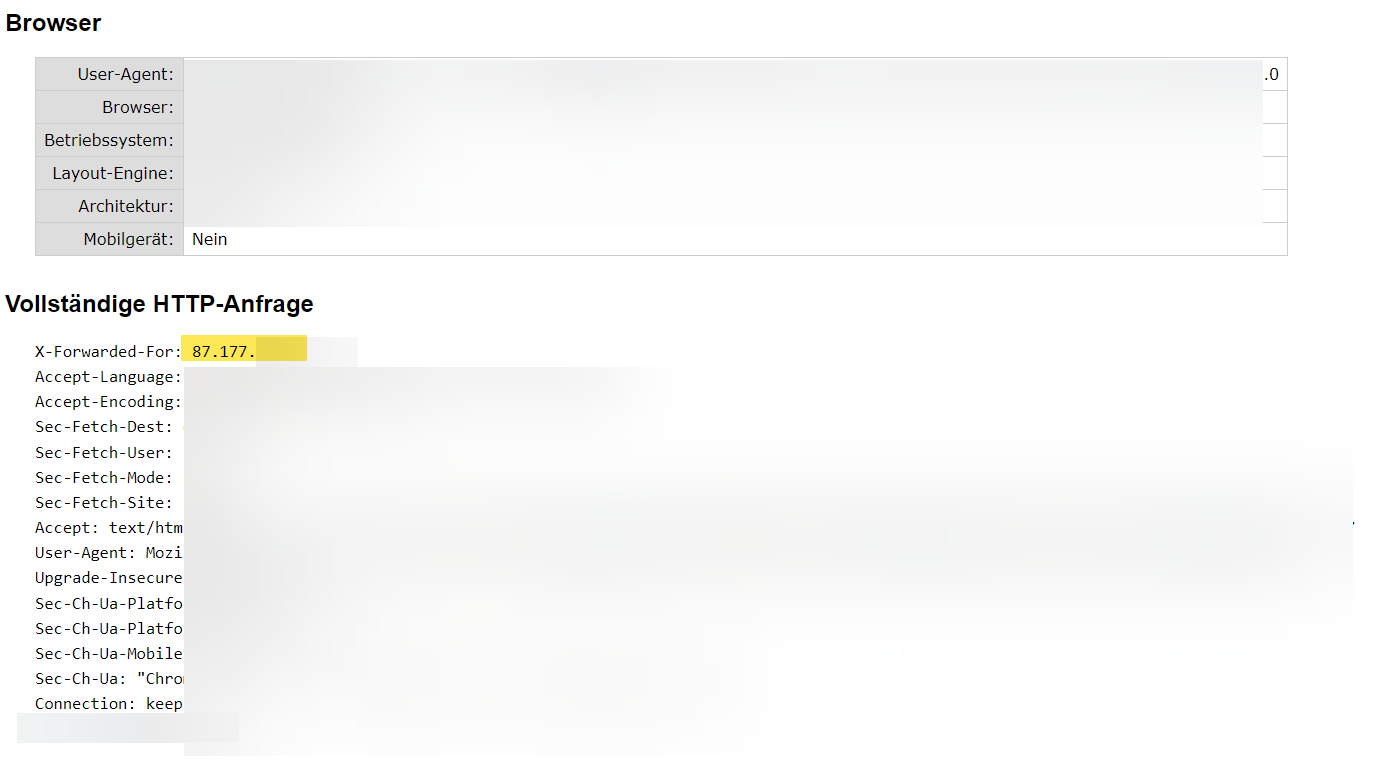
How can we disable this Feature of Netskope? We don’t want Netskope to pass along the original public IP of our users ...
The setting for the XFF Header unser Settings → Security CLoud Plattform is set to “Do not trust” but it has obviously nothing todo with our problem:
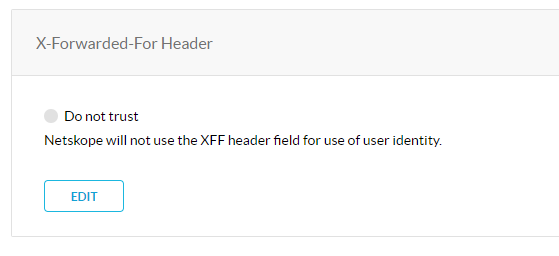
In our current on-premise proxy we had the option to remove theXFF Information:










