Certificate pinned applications by definition are not susceptible to ssl interception and without ssl interception we are blind to what is going on. Unfortunately most native applications, those that are running as an executable, are certificate pinned. If you try to intercept ssl traffic from these applications you will break the application. As a result you are forced to bypass traffic from these applications. the problem then arises as to which sites is the application trying to get too. Idealy you just ask the developer, but sometimes this is not an option so as an alternative you can run this simple script to identify the sites that we see the process trying to access
for example in Windows using Powershell:
get-content c:userspublic
etskope
sdebuglog.log -tail 5 -wait | Select-String "slack.exe"
this basically will parse the nsdebuglog.log and pull out whatever matches the process, in this case slack.exe
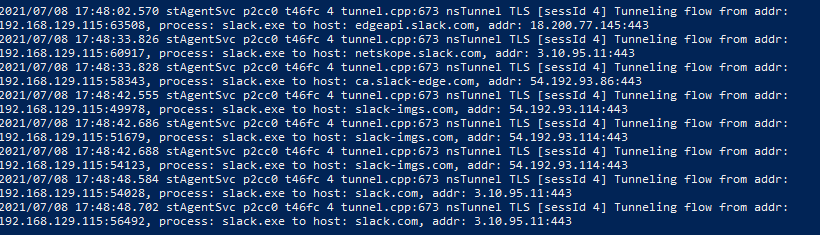
Once you've identified the sites you can then plug them into your sterring bypass exception.
Hope this is helpful.







