Hello All,
The following articles have come out re: Evasive Phishing that domain front-ends Google to protect potentially malicious or unintended traffic from being picked up by filtering or threat.
The following articles address how this works:
https://cofense.com/blog/google-amp-the-newest-of-evasive-phishing-tactic/
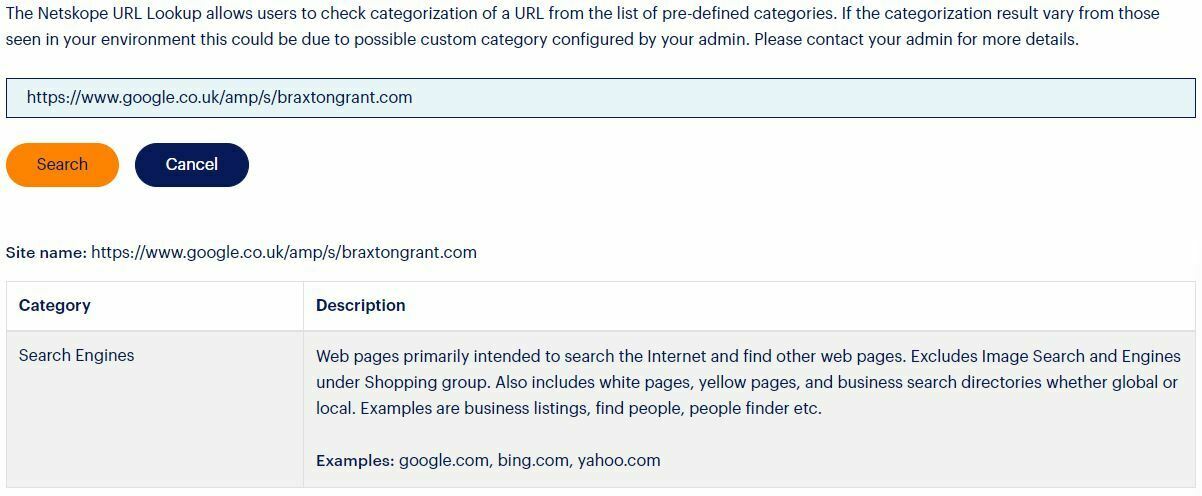
This means if NGSWG can't categorize the URL is hiding in AMP then it will treat the site as categorized as safe (or likely safe) based on that it is hosted at google, not the real site of xxx.xxx (or whatever malicious site and path is included there).
Examples:
https://www.google.com/amp/s/xxxxx.xxxx/somesite.html or https://www.google.co.uk/amp/s/xxxx.xxx/badimage.img
From a position of making sure this product is competitive in the market, there are some other vendor tools that can granularly expose this hidden URL and site and evaluate it piecemeal from the original request, but I have not found a way to address this w/ NGSWG.
It is not appropriate to assume all material hosted via AMP is bad, but there is the potential legitimate traffic is fronted via AMP but on the same hand is also bad traffic. We simply don't know, and taking too strict of a security posture will impact business inappropriately, so one cannot create traffic to block anything with "google(.*)/amp/s/" (regex likely not accurate but given to make a point).
Looking for feedback from Netskope support, or other customers, in how they have addressed this concern with Netskope policy. I would prefer to have a way to solve this with Netskope NGSWG, and not have to solve it with a competitor product.
Alternatively, if someone tells me there is awareness for Google AMP as a product (app) and we have some options in there, I'd also be interested in that.
Ultimately I would like:
- Evaluate the hidden URL and identify it's risk separate from the Google AMP URL as a whole
- Make policy decision based on the AMP fronted (protected) site (ALLOW, DENY, Isolate? :))
Thank you,
AKH_BGT