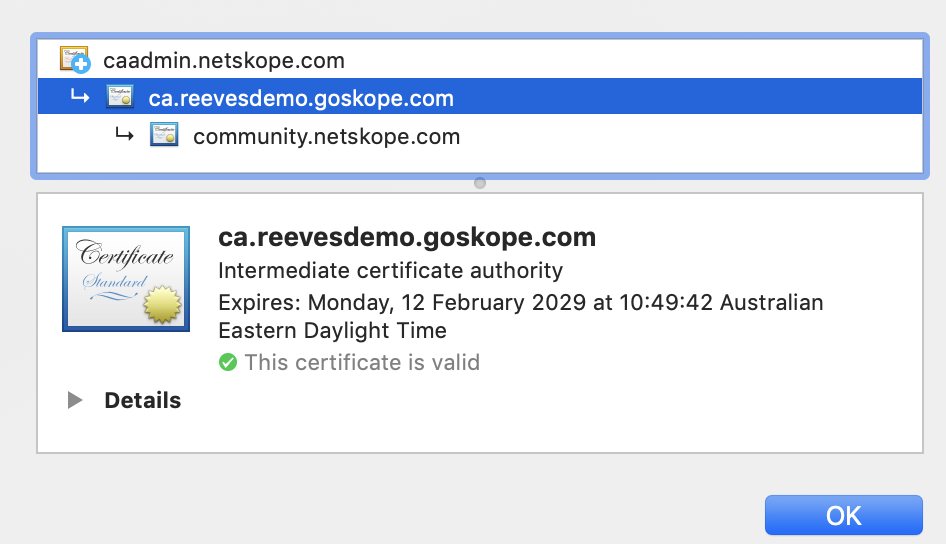
Question: How can I tell if my traffic is being intercepted by Netskope from a browser?
Solved
Is Netskope intercepting my browser traffic?
 +13
+13Best answer by btokuyoshi
Just to clarify, checking SSL certs is a way to identify if SSL decryption is happening. Depending on how you define interception, esp from an end user's perspective, interception could also mean any inspection of traffic, including plaintext http. In which case the above method would not apply and end users would need to run a tracert. Intentionally causing a policy violation (like downloading the eicar file) might be another way for end users to see, but this won't work if policy isn't enabled for the violation that the user is attempting.
This topic has been closed for replies.
Sign up
Already have an account? Login
Sign in or register securely using Single Sign-On (SSO)
Employee Continue as Customer / Partner (Login or Create Account)Login to the community
Sign in or register securely using Single Sign-On (SSO)
Employee Continue as Customer / Partner (Login or Create Account)Enter your E-mail address. We'll send you an e-mail with instructions to reset your password.