Punycode is a standard for mapping characters using the ASCII standard and one of its functions is to provide support for Internationalized Domains Names (IDNs) to the internet. This is used when you see non-ascii characters like Cyrillic, Latin, Chinese and others on a domain name to make sure the DNS and subsequent HTTP requests are all completed successfully.
Punycode becomes a security risk in connection with homographic phishing – cyber-attacks in which criminals use the similar appearance of different characters to lure their unsuspecting victims to fake websites.
Example:
netskоpe.com looks identical to netskope.com but the letter “o” used in the first example is in Cyrillic giving an attacker the ability to send the user to a completely different domain.
The way browsers deal with the difference above is by converting punycode into ascii characters so by clicking on the first link would actually get you to xn--netskpe-ejg.com. You can play with this by finding a punycode converter on the internet like this one. The converted domain is what a proxy sees so if you want to setup a policy to block it you must use the ASCII domain and not the internationalized one.
Punycode can even be used with emojis which are also supported by ASCII, translating the domain i❤netskope.com into xn--inetskope-vj5f.com.
A few more examples:
| IDN domain | converted ASCII domain |
| 短.com | xn--s7y.com |
| münchen.com | xn--mnchen-3ya.com |
Netskope supports the categorization of IDN domains so if an IDN domain was recently registered it should be at least placed into the Newly observed domain category, allowing customers to setup a policy to block them or isolate them with RBI.
If a customer wants to completely block IDN domains on their Netskope tenant, they can do it by setting up a regular expression to match the beginning of the mapped domain, which is called ACE (short for ASCII-compatible encoding) that looks like “xn--”. Follow the steps below to setup a real-time policy to block these domains.
Configuring the Web Profile
Create a new URL list on the Web Profiles configuration and setup a Regex match like the one below:
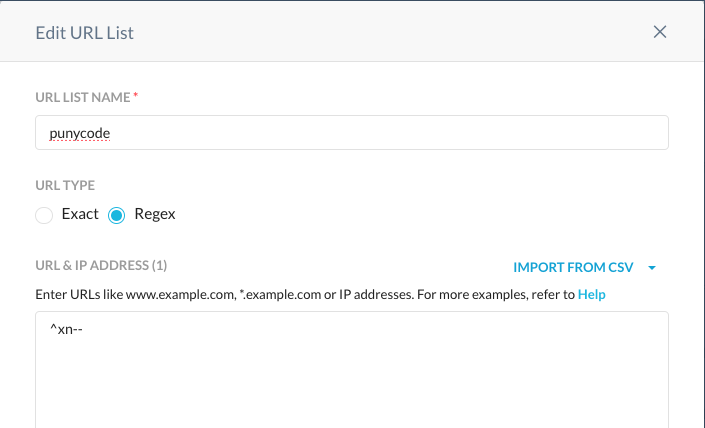
Add this URL List to a custom category so it can be later used in policy.
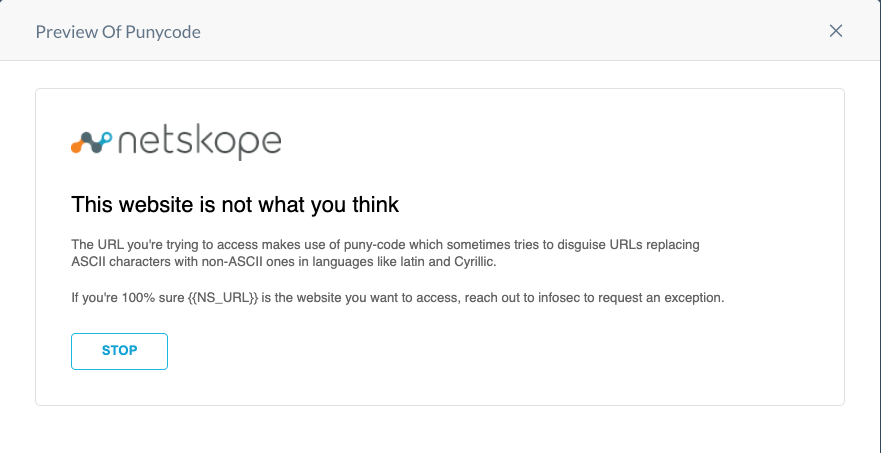
Configure a User Notification Template
Create a new user notification template to coach users on the risks presented by international domains. Here is a suggested text for it:
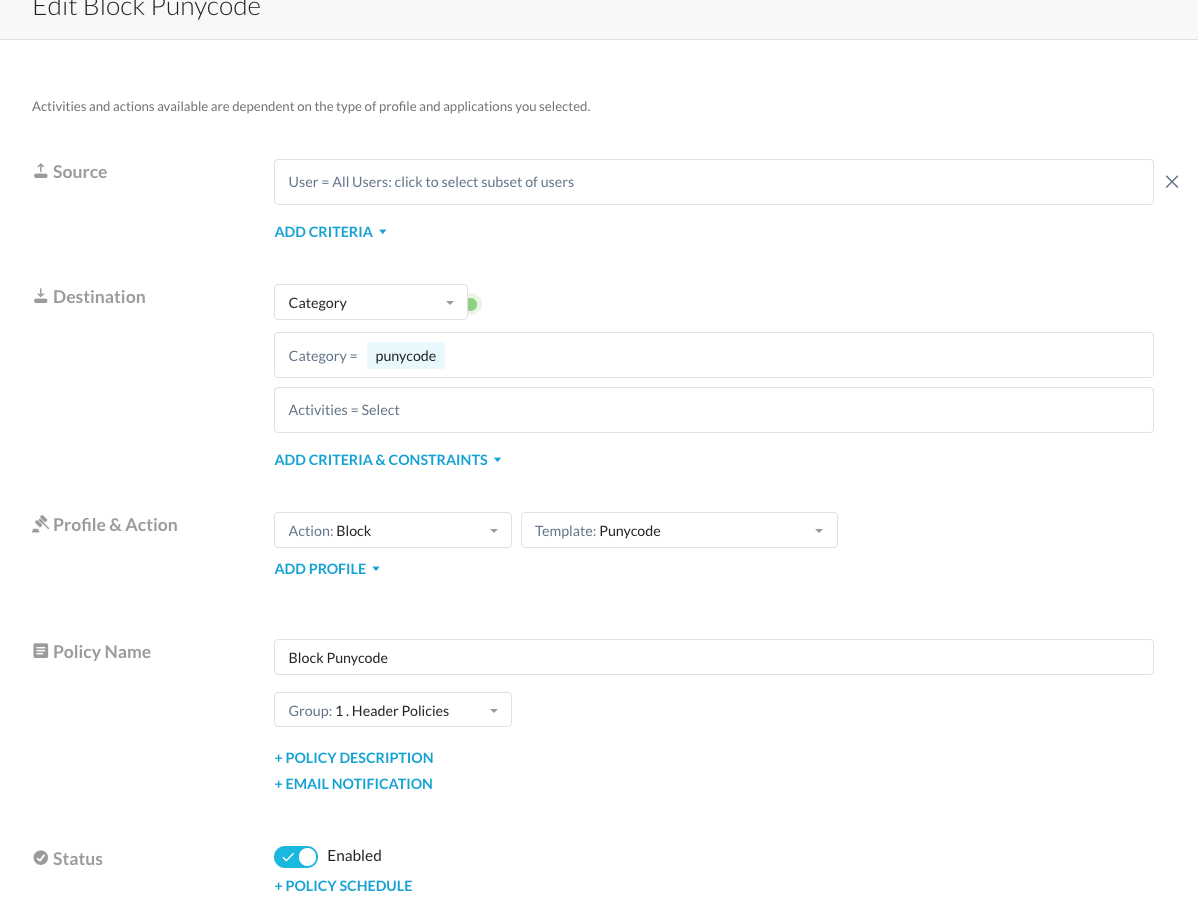
Setup a Real-Time policy
Configure a real-time policy and use the custom category you created as a destination criteria and with an action set to block that presents the notification template above.
And with this, you will be able to successfully log or block access to any domains that make use of punycode. you can also match the custom category with other categories like NOD, NRD or Uncategorized to make it more flexible in case you have seen legitimate use of IDNs in your organization.









