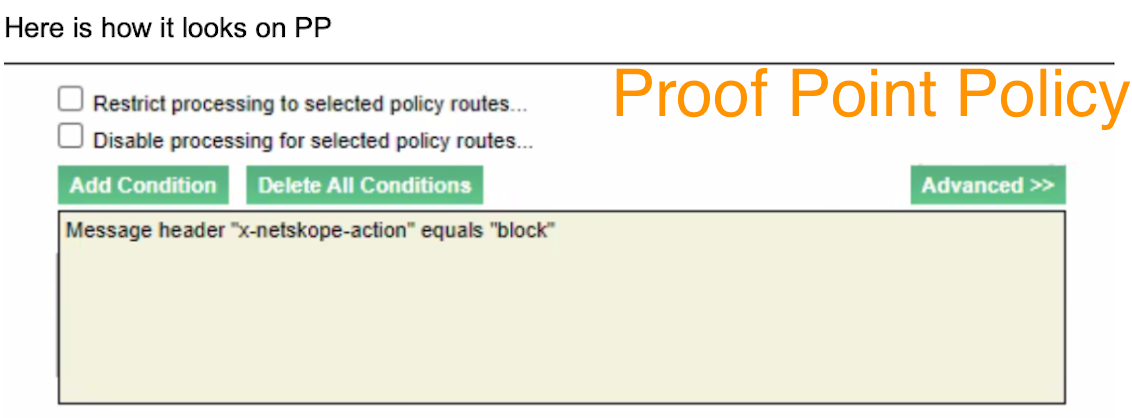
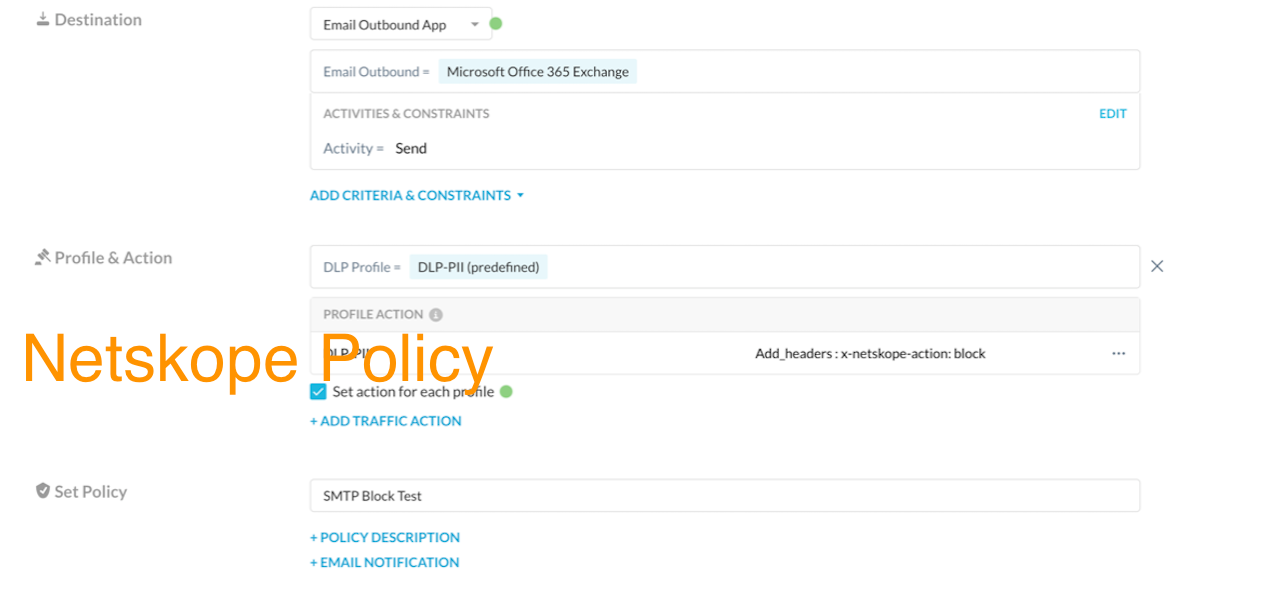
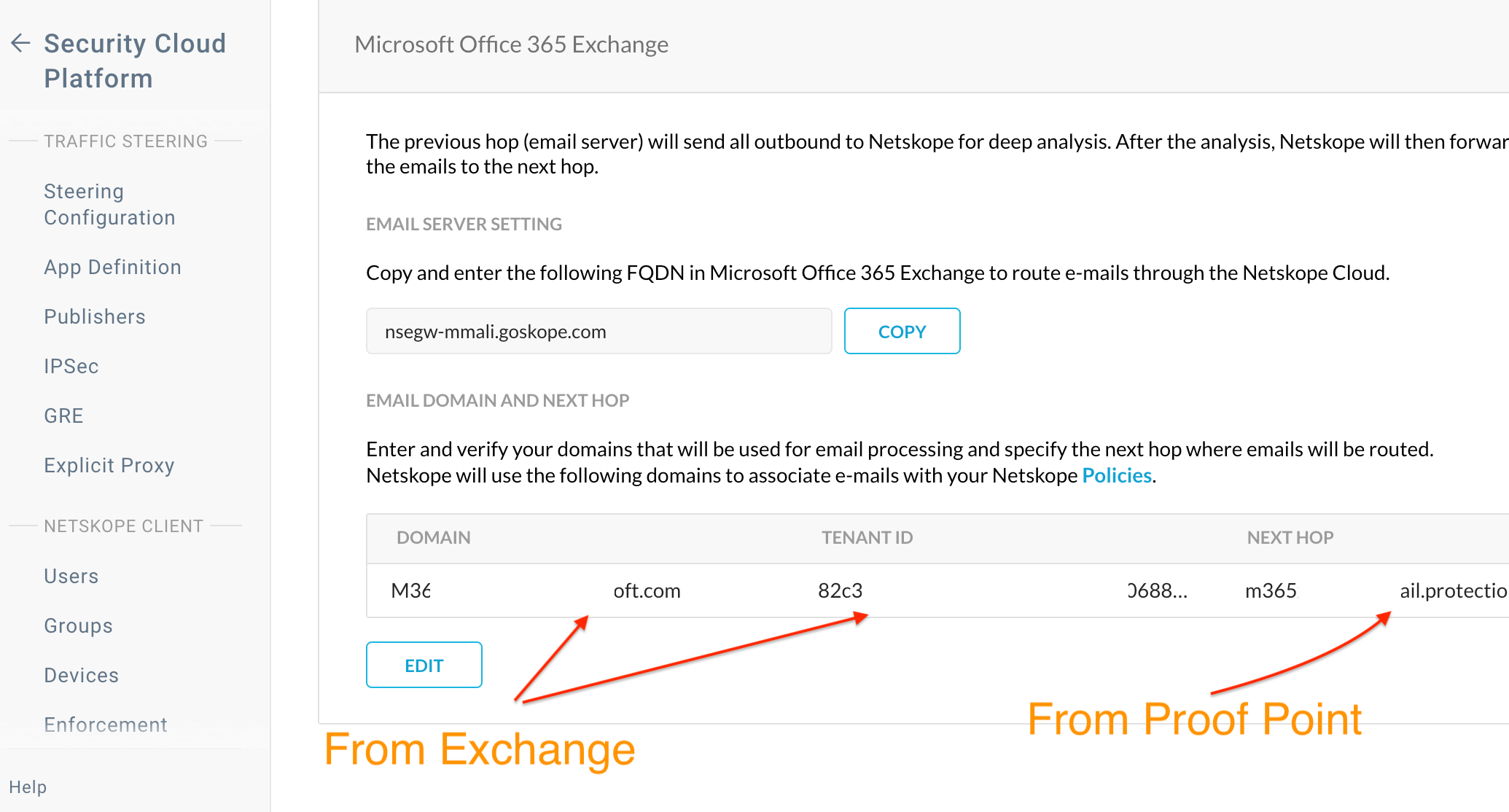
If you are deploying Netskope SMTP Proxy few notes of interest. (Various screenshots of interest attached).
1. If your upstream has SPF check ensure to add following record to your DNS server so that the SPF check does not fail
_spf.goskope.com
2. To allow Netskope IP's refer to the following list
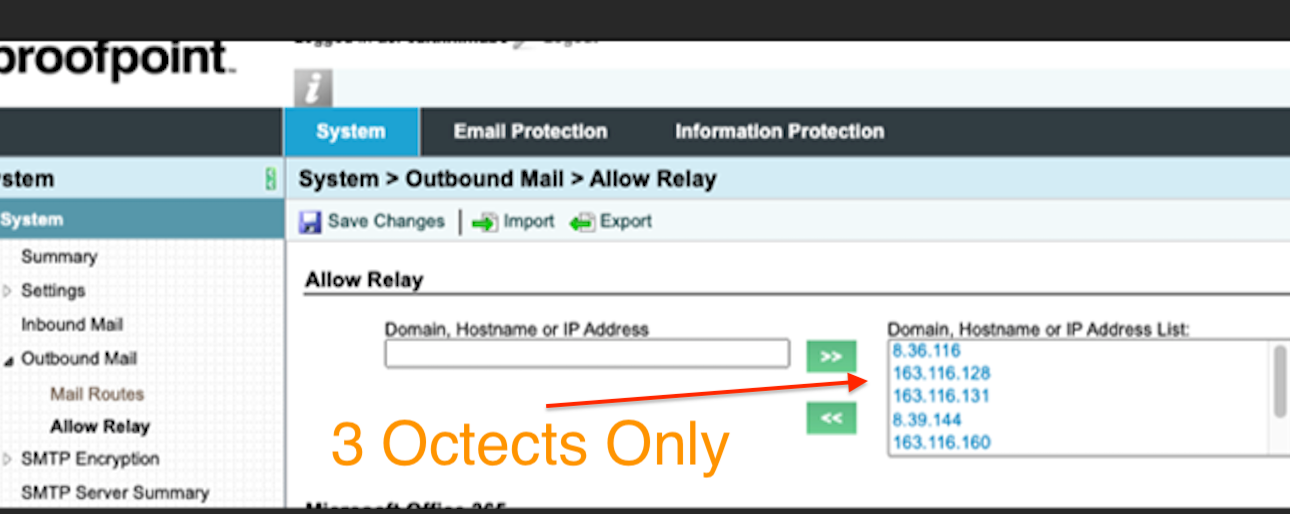
2.a If you are using Proofpoint as the upstream MTA there is a tweak to allow these IP's.
Proofpoint does not accept CIDR ranges. Also adding in CIDR notation e.g. /24 did not help in my case.
Use the following format (first 3 octets only) (screenshot attached)
163.116.128
8.36.116
NOTE: for complete list of IP's subscribe to this article. There is a table for SMTP Proxy "
Netskope Email DLP (SMTP) List for Allowlisting
The following list of IP ranges represents where SMTP traffic may egress from Netskope's NewEdge Security Cloud, and should be used for permitting traffic with upstream email providers. Netskope's recommendation is that customers' add all IP ranges when configuring allowlisting with email providers. If a tenant is assigned to a specific region (other than the global region), then only the relevant range(s) in the table below require allowlisting.
| Global (default) | All DCs below | All prefixes below | All ranges below |
| North America | San Jose, CA, USA (SV5) | 8.36.116.0/24 163.116.128.0/24 | 8.36.116.0 - 8.36.116.255 163.116.128.0 - 163.116.128.255 |
| North America | San Jose, CA, USA (SJC1) | 163.116.131.0/24 | 163.116.131.0 - 163.116.131.255 |
| Europe | Frankfurt, Germany (FR4) | 8.39.144.0/24 163.116.160.0/24 | 8.39.144.0 - 8.39.144.255 163.116.160.0 - 163.116.160.255 |
| Europe | Amsterdam, Netherlands (AM2) | 31.186.239.0/24 | 31.186.239.0 - 31.186.239.255 |
| Oceania | Melbourne, Australia (MEL2) | 163.116.206.0/24 | 163.116.206.0 - 163.116.206.255 |