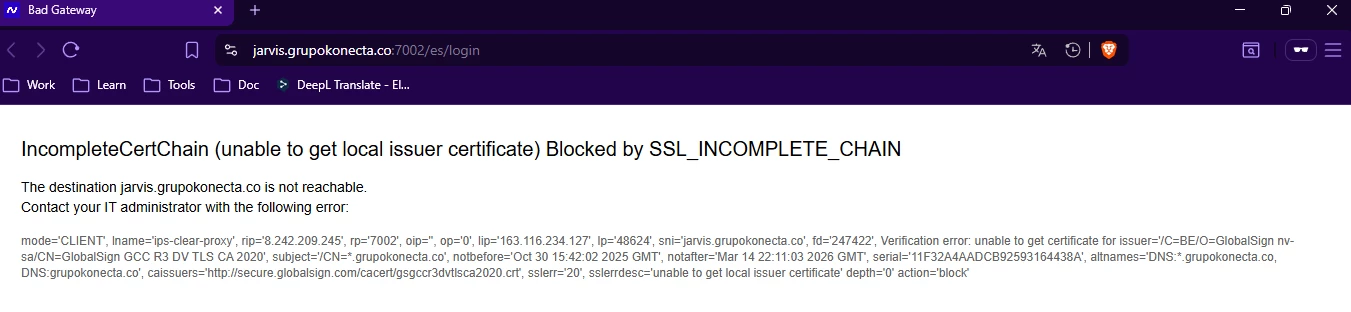
Hello Team,
I am working on SSL inspection with Netskope in our organization (Bogotá, Colombia) and encountered the following issue when accessing a specific domain:
-
Domain:
jarvis.grupokonecta.co -
Netskope error message excerpt:
IncompleteCertChain (unable to get local issuer certificate) … Blocked by SSL_INCOMPLETE_CHAIN
Verification error: unable to get certificate for issuer = ‘/C=BE/O=GlobalSign nv-sa/CN=GlobalSign GCC R3 DV TLS CA 2020’, subject = ‘/CN=.grupokonecta.co’, altnames = DNS:.grupokonecta.co, DNS:grupokonecta.co’, caissuers = ‘http://secure.globalsign.com/cacert/gsgccr3dvtlsca2020.crt’, sslerrdesc = ‘unable to get local issuer certificate’ -
I have verified via
openssl s_client -connect jarvis.grupokonecta.co:443 -servername jarvis.grupokonecta.co -showcertsand online tools such as SSL Labs, and indeed the certificate chain appears incomplete (missing or not served correctly by the server).
What we have reviewed so far:
-
The server certificate for *.grupokonecta.co is issued by GlobalSign and appears valid (dates okay).
-
The “caissuers” URL points to an intermediate certificate from GlobalSign (“GSGCCR3DVTL SCA2020”) but it seems not being served.
-
On the Netskope side, SSL inspection policy is fully active for this domain — no exclusion or “Do Not Decrypt” rule yet.
-
We are considering two paths: (a) ask the server admin to properly configure and serve the full certificate chain, or (b) temporarily mark the domain as “Do Not Decrypt” in Netskope so users can access it.
Questions to the community:
-
Has anyone experienced this exact “unable to get local issuer certificate” error when using Netskope SSL inspection? What was the root cause (server misconfiguration, missing intermediate, Netskope settings, etc.)?
-
If the server is not serving the intermediate certificate, what is the best practice for handling this in a Netskope-managed environment? Are there mitigations within Netskope (policy, client trust chain tweaks) without waiting for the external server admin?
-
From a security perspective, is it acceptable/practical to mark the domain as “Do Not Decrypt” temporarily? What risks or side-effects should we consider (for example visibility loss, audit gaps)?
-
Are there specific logs or trace details in the Netskope console that help pinpoint exactly which certificate link in the chain is failing (client→Netskope inspection, or inspection→server side)? Any recommendations for which log files / macros to examine?
Any shared experiences, step-by-step guidance, or relevant knowledge base articles would be highly appreciated. Thank you in advance!
Best regards,