Browsers with Zero-Day Vulnerabilities ? What am I talking about you might think -
Well, it happened with Chrome recently - for the third time this year - CVE-2023-3079 released earlier this month affects Google Chrome prior to 114.0.5735.110 by allowing a remote attacker to potentially exploit heap corruption via a crafted HTML page. (Chromium security severity: High)
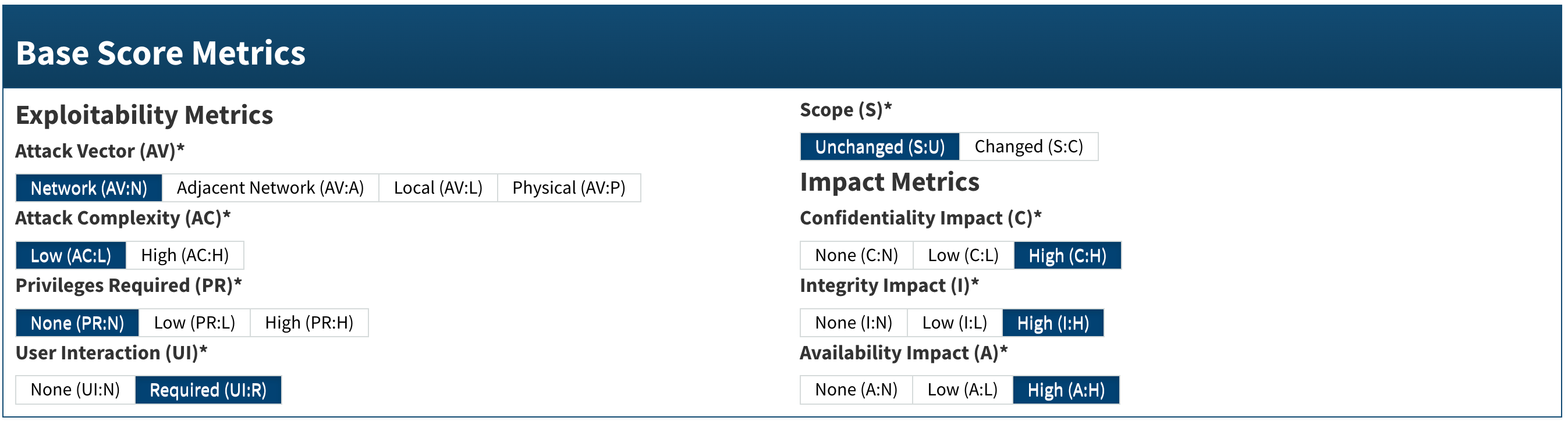
Sounds serious? Oh you bet - a CVSS Base Score: 8.8 HIGH is not something I'd want to ignore - NIST metrics below indicating a low level attack complexity is all you need to know here to ensure your fleet gets updated ASAP.
Where I'm getting at is that monitoring versions of critical pieces of software like your users browsers is very important. The question becomes, how?
Of course, most admins may rely on a software deployment tool to track this - JAMF, SCCM etc. But did you know that Netskope, since it is widely used as a NG-SWG/CASB 'inline' traffic steering mechanism, can determine browser versions too?
To obtain this information, all you need to do is steer web traffic 'inline' - and by just looking at this steered traffic, we can determine, the browser, and its associated versions in use.
(Spoofing browser versions by manipulating headers is indeed possible, but I'd guess that may not be a common occurrence nor performed by your 'standard' user - to prevent such mischief, hardening your devices by not allowing browser plugins may be appropriate)
The icing on the cake is the fact that Netskope Advanced Analytics (NAA) can be utilized to view this info, in an easily consumable way. Don't trust me? Take a look at this screenshot for yourself 🙂 (Advanced analytics report template attached to this post)
By the way, this user agent string i.e. browser version can also be viewed within SkopeIT > PageEvents for any non NAA users but then it's cumbersome to 'summarize' (if at all possible), hence I'm exploring this NAA route.
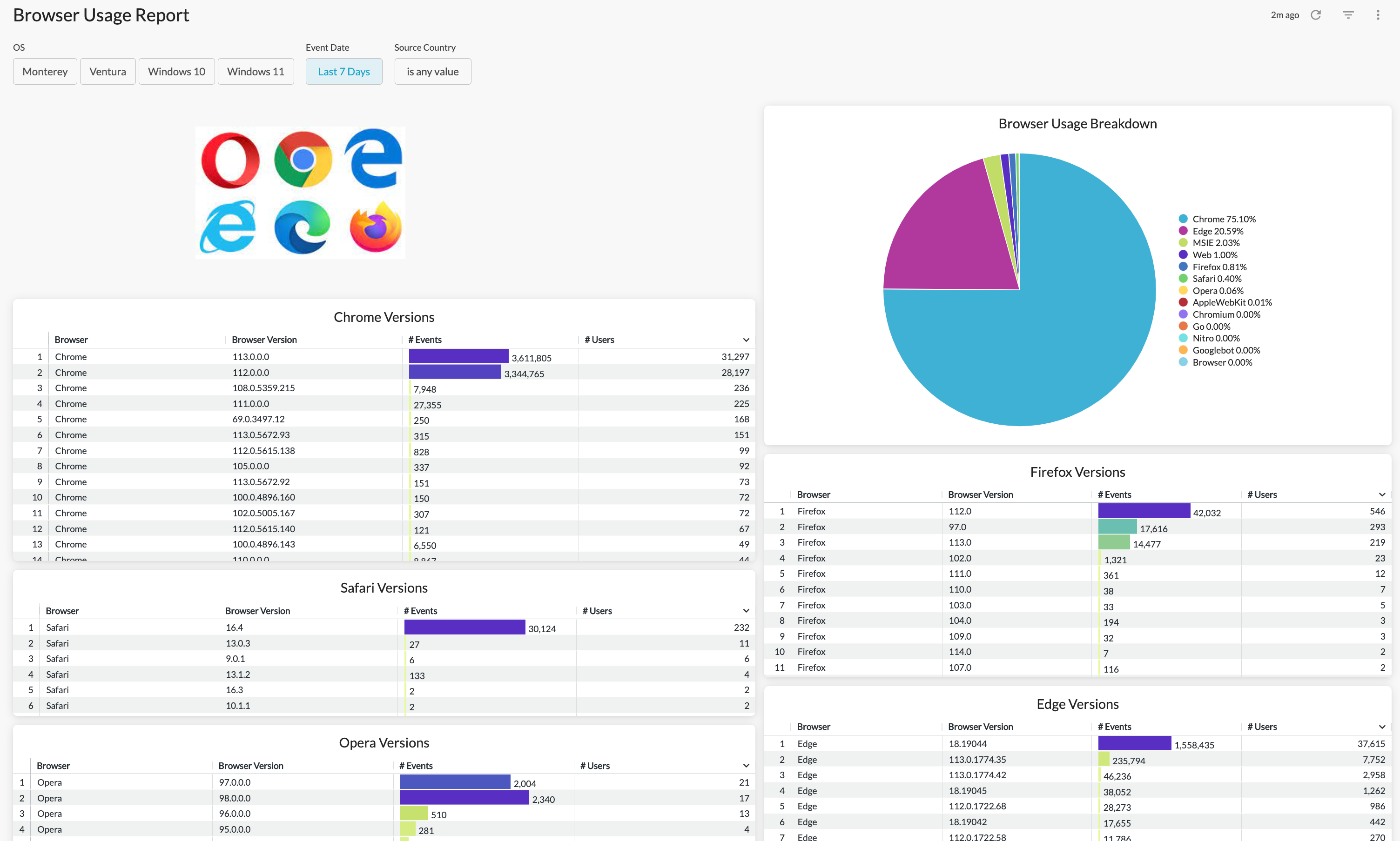
Using this report, I'm able to understand the browser usage pattern within my user base.
What I recommend my customers to do is to also 'schedule' these reports to my device/software management teams - This way they are aware of changes in usage patterns and can take appropriate decisions
Looking at the report screenshot above, I can see that we have quite a few users on older versions of Chrome and there seems to be a few dozen users utilizing a non-sanctioned browser - Opera <YIKES>
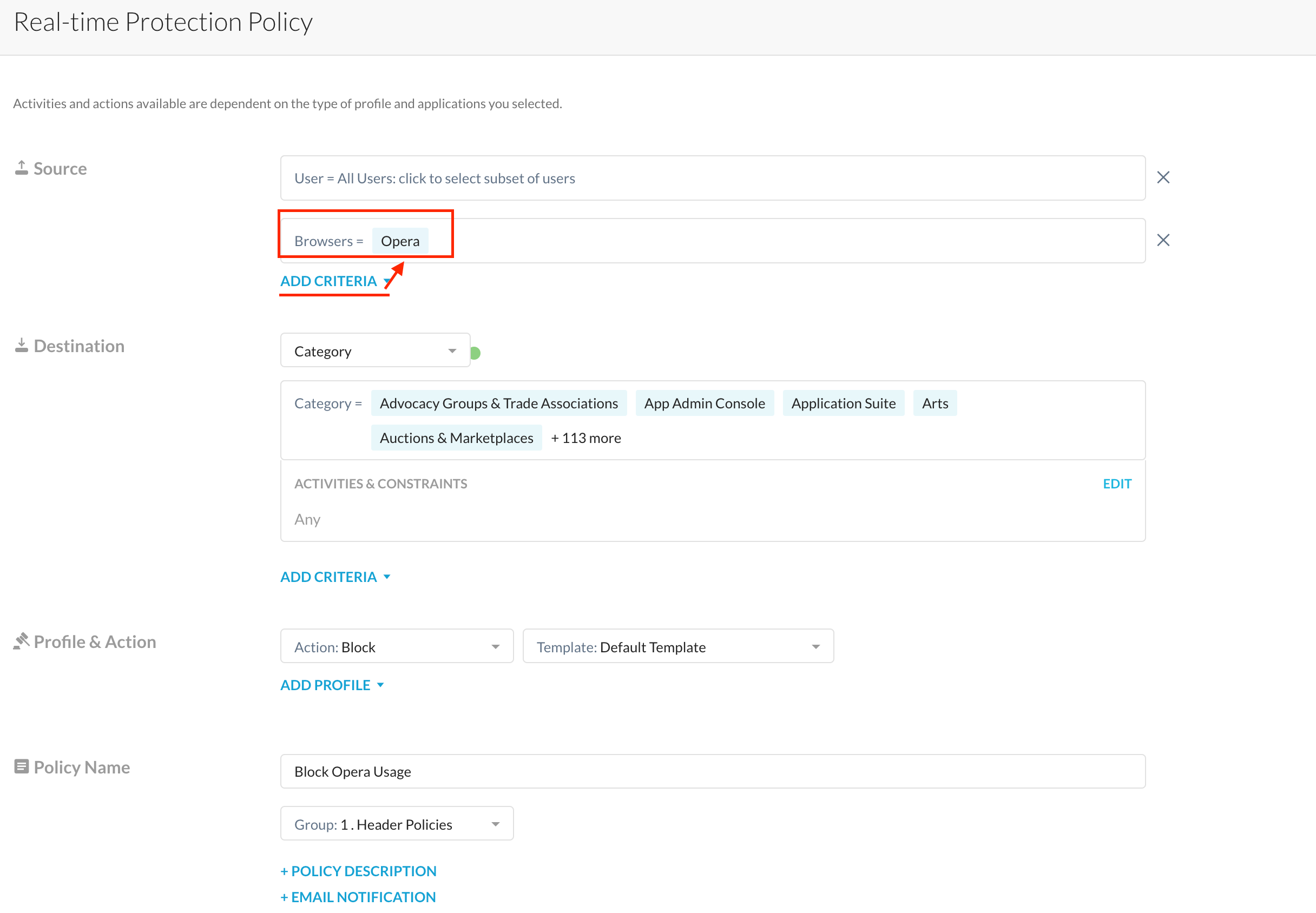
What do I do if I want to block the usage of such unsanctioned browsers like Opera using Netskope? Simple, just specify the browser within a real-time protection policy and place it high up in your stack so that users don't get to use the unsanctioned browser in question.
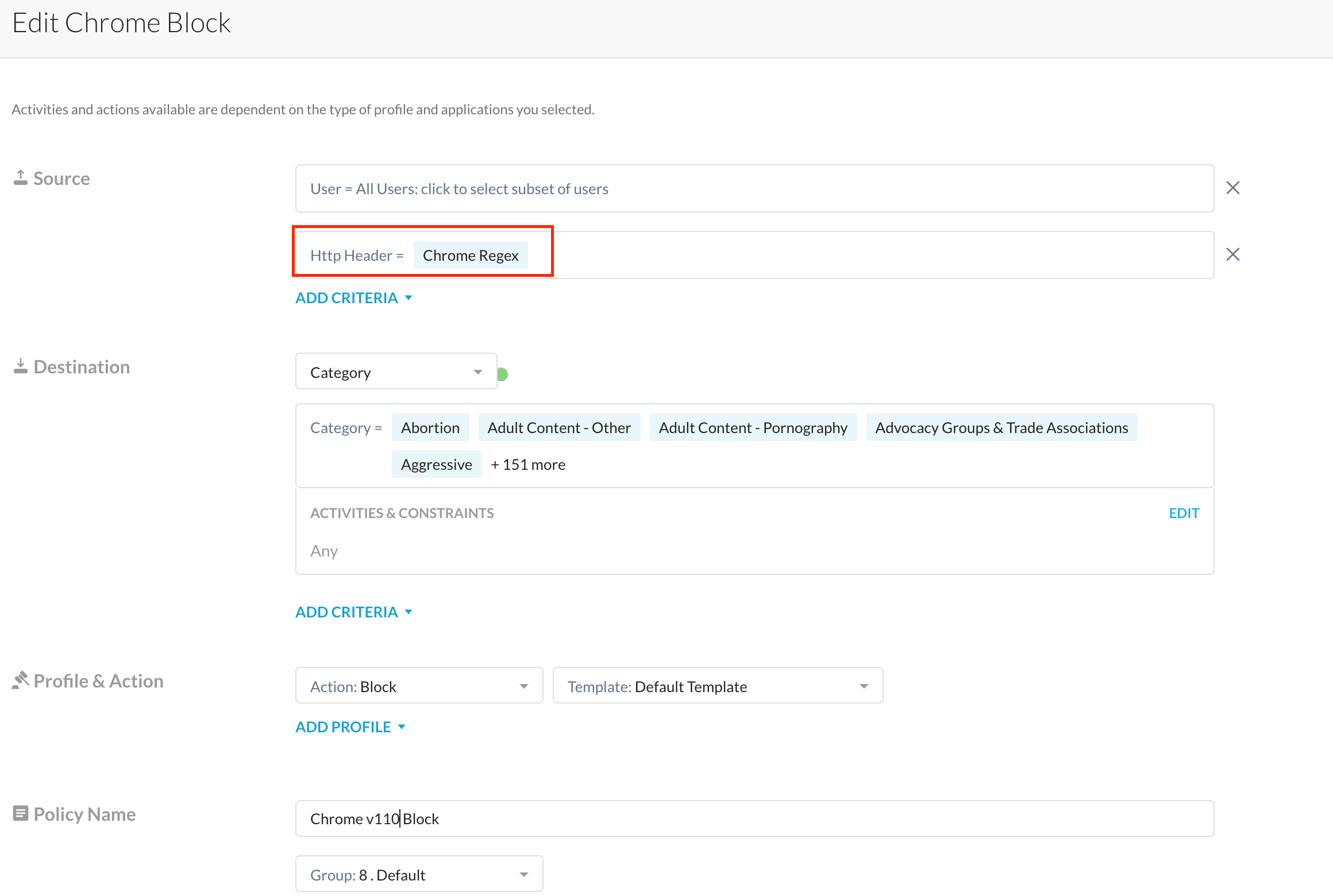
Now how do I block a specific version of a browser (let's say a vulnerable version v113.x of chrome).
3 words - HTTP Header Profiles
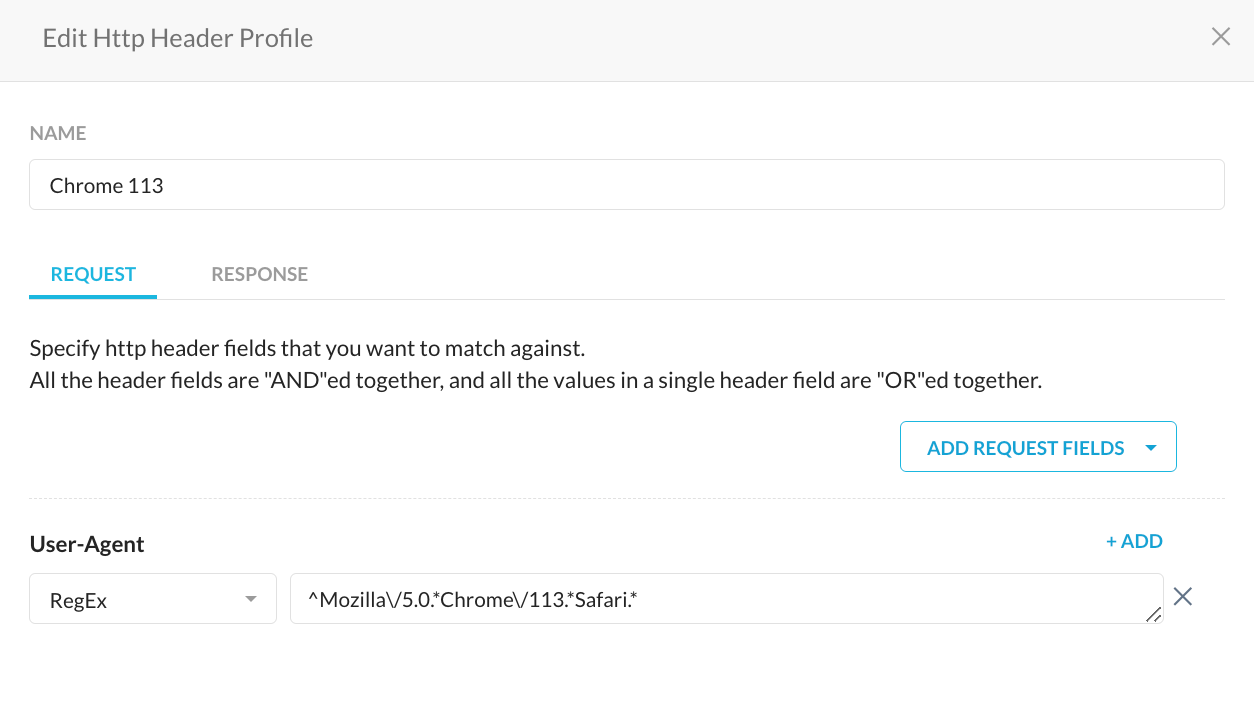
Using HTTP Header Profiles chosen within a policy, admins can block browsers wherein the user agent string matches specific 'strings' defined within the HTTP Header Profile.
Example, Chrome v113 on my Mac can be detected using a regular expression like ^Mozilla/5.0.*Chrome/113.*Safari.*
Subsequently selecting this HTTP Header Profile within your real-time protection policy is what needs to be done to block the necessary (I meant, outdated) versions of Chrome.
I hope this helps you keep your environment safe - any questions or comments, please let me know








