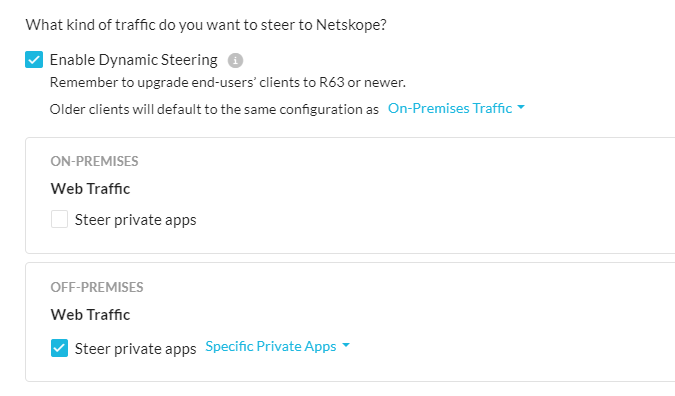
how to automatically disable agent npa tunnel, when endpoints are in company internal network?.
It is necessary that when the endpoints are in the internal network of the company, and the endpoint needs to connect to the internal web applications, these are not encapsulated and the traffic is not sent to the netskope cloud. If not, the traffic must go directly through the internal network.
How does netskope manage to do this, because it has been tested and found that the netskope agent for https always tunnels traffic to the cloud, so for intra-enterprise web applications you will never be able to access it directly.