Hi
I have been able to configure the NPA periodic reauth and the flexible dynamic steering in my netskope settings, but I’d like to “combine” both of them and I’m not sure if that’s possible.
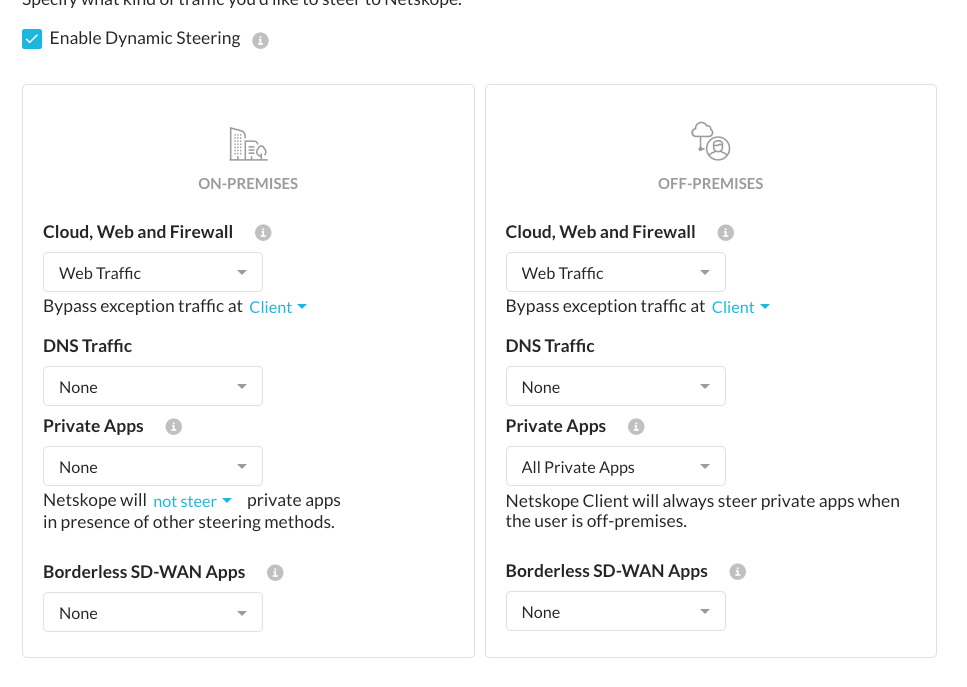
I mean, I have configured the dynamic steering so the users Netskope Client will steer traffic to private apps only whten they are off-premise, and the client will disable for private apps when they are on-premise.
I have also configured the Periodic Reauth for NPA in my client configuration settings, so it asks for reauthentication after a period of time, but I see that this Periodic Reauth asks for the reauthentication no matter if the user is on-premise or off-premise.
As I want the client only to steer traffic to private apps when off-premise, I’d like also that the Periodic Reauth triggers only when the user is off-premise, and not on-premise no matter how many time has passed since last authentication.
could this be done? It seems that the Periodic Reauth is a “global” setting and don’t take into account the dynamic steering, is that right?
Thanks in advance for your comments and suggestions!