In this article we’ll demonstrate how you can implement automatic remediation for security posture violation findings discovered by Netskope Cloud Security Posture Management (CSPM).
Netskope CSPM continuously assesses public cloud deployments to mitigate risk, detect threats, scan and protect sensitive data and monitor for regulatory compliance. Netskope simplifies the discovery of security misconfigurations across your clouds. Netskope Auto-Remediation framework for GCP enables you to automatically mitigate the risk associated with these misconfigurations in your GCP cloud environment.
Netskope CSPM security assessment results for such security benchmark standards as NIST, CIS, PCI DSS, as well as for your custom rules are available via the View Security Assessment Violations Netskope API.
Netskope auto-Remediation solution for GCP deploys the set of GCP Cloud functions that query the above Netskope API on the scheduled intervals and mitigates supported violations automatically.
You can deploy the framework as is or customize it to mitigate other security violations and to meet your specific organization’s security requirements.
See Netskope's Github page for more details - https://github.com/netskopeoss/CSPM-GCP-AutoRemediation
Auto-remediation Workflow
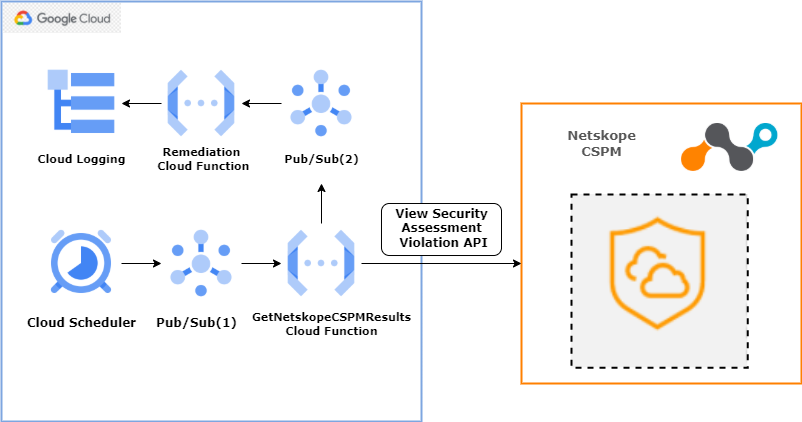
Workflow Overview:
- Cloud scheduler will trigger Pub/Sub(1) topic with payload/message after every interval.
- Payload/message will have two parameters:
- rule_name: Name of the Rule for which remediation is required.
- rule_short_name: This will be the Pub/Sub(2) topic name that will be used by GetNetskopeCSPMResults Cloud Function to push alert details to Remediation Cloud Function.
- Pub/Sub(1) will trigger the GetNetskopeCSPMResults cloud function which will perform the below steps:
- Pull payload/message from pub/sub(1) topic.
- Call Netskope Security Assessment Violation API for given rule_name. If the rule is violated then, extract parameters GCP ProjectID, Resource ID, and Region Name from the alert.
- Trigger Pub/Sub(2) topic and push extracted parameters. Pub/Sub(2) topic will pass these parameters to the Remediation cloud function of specified rule_name.
- The remediation cloud function will pull information from Pub/Sub(2) and perform remediation.
- Check logs of remediation functions in cloud logging.
Currently Supported GCP Auto-remediation Rules
|
No. |
Profile |
Service |
Rule Name |
Action |
|
1 |
CIS-GCPFND-1.0.0 |
Compute Engine |
Ensure the default network does not exist in a project |
The auto-remediation cloud function deletes the default VPC network. |
|
2 |
CIS-GCPFND-1.0.0 |
Compute Engine |
Ensure "Block Project-wide SSH keys" enabled for VM instances |
The auto-remediation cloud function set “block-project-ssh-keys” meta-data value of VM instance to True. |
|
3 |
CIS-GCPFND-1.0.0 |
IAM |
Identities and credentials: Ensure user-managed/external keys for service accounts are rotated every 90 days or less |
The auto-remediation cloud function disables the Service Account keys that are created before 90 days |
|
4 |
CIS-GCPFND-1.0.0 |
IAMPolicy |
Identities and credentials: Ensure that ServiceAccount has no Admin privileges. |
The auto-remediation cloud function removes Service Account entries from members for owner/editor/*Admin role |
|
5 |
CIS-GCPFND-1.2.0 |
Identity |
Ensure that IAM users are not assigned the Service Account User or Service Account Token Creator roles at project level |
The auto-remediation cloud function removes role binding from policy having role as “Service Account User” or “Service Account Token Creator” |
|
6 |
CIS-GCPFND-1.0.0 |
Kubernetes |
Ensure Stackdriver Logging is set to Enabled on Kubernetes Engine Clusters |
The auto-remediation cloud function set the logging service as “logging.googleapis.com/kubernetes” if not set |
|
7 |
CIS-GCPFND-1.0.0 |
Logging |
Ensure that Cloud Audit Logging is configured properly across all services and all users from a project |
The auto-remediation cloud function removes exempted members from audit logging service configurations and enable audit logging for all services with log types: DATA_READ, DATA_WRITE, ADMIN_READ, ADMIN_WRITE |
|
8 |
CIS-GCPFND-1.0.0 |
SQL |
Ensure that Cloud SQL database Instances are not open to the world |
The auto-remediation cloud function removes a network which has an IP value of “0.0.0.0/0“ from Cloud SQL Instance. |
|
9 |
CIS-GCPFND-1.0.0 |
SQL |
Ensure that Cloud SQL database instance requires all incoming connections to use SSL |
The auto-remediation cloud function set “requireSsl” property of cloud SQL instance to True. |
|
10 |
CIS-GCPFND-1.0.0 |
Storage |
Identities and credentials: Ensure that Cloud Storage bucket is not anonymously or publicly accessible |
The auto-remediation cloud function removes “allUsers” and “allAuthenticatedUsers” principles from the bindings of bucket policy. |
|
11 |
CIS-GCPFND-1.0.0 |
VPCnetwork |
Ensure that SSH access is restricted from the internet |
The auto-remediation cloud function removes the entry for source “0.0.0.0/0” from firewall rule source ranges if present |
|
12 |
CIS-GCPFND-1.0.0 |
VPCnetwork |
Ensure VPC Flow logs is enabled for every subnet in VPC Network |
The auto-remediation cloud function enables flow logging for each subnet region-wise |







