Good Afternoon folks
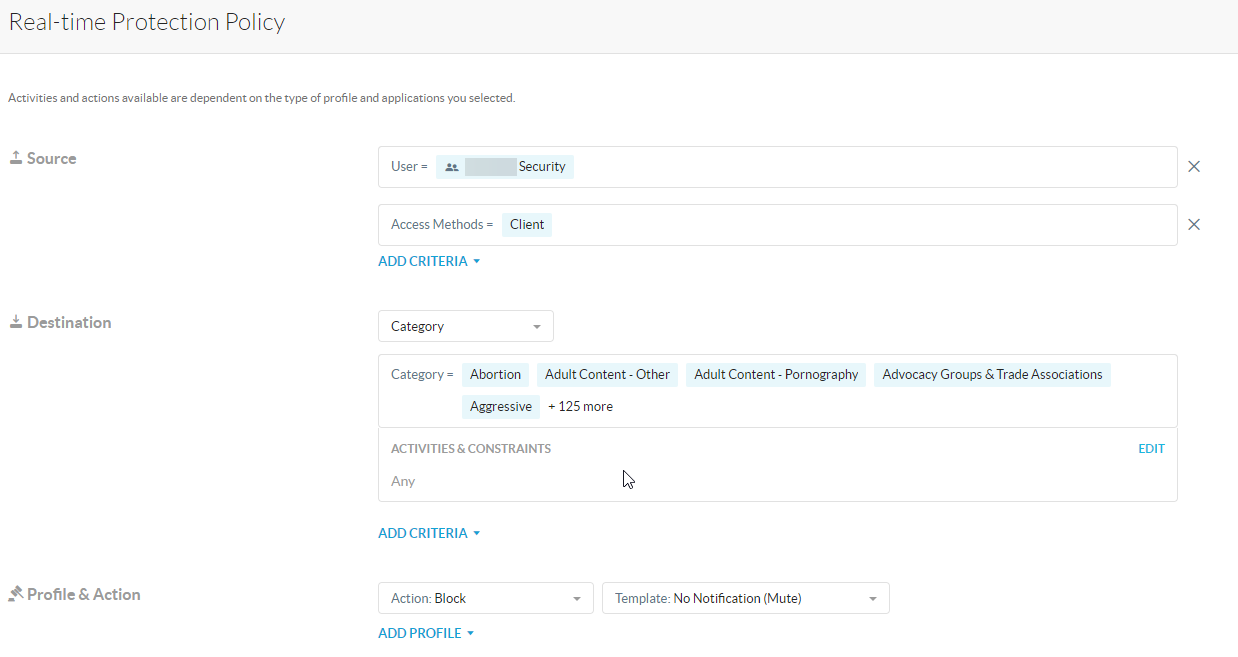
We're pretty new to Netskope, so please excuse me if this is the wrong place for this question or if it's a particularly basic question, and we're going through the Eseential 8 security process at the moment. To that end, we're looking to prevent Admin accounts from being able to access the internet when logged into machines with Netskope installed.
Is this something that Netskope is capable of? I'm assuming it's a policy that we can roll out to a created group of users?
Thanks very much