Netskope Global Technical Success (GTS)
Limitations with Signal Application
Netskope Cloud Version - 130
Objective
Signal is a chat and instant messaging platform accessible via its native application only. This document is intended to discuss in detail the limitations limitations associated with Signal concerning its use with Netskope
Prerequisite
Netskope SWG or Next-Gen SWG license
Context
End-users at customers' end may be utilizing Signal on their machines. This document outlines the types of controls that can be implemented for Signal through Netskope
Do you know?
- Signal does not offer a web version for accessing messages directly through a web browser like WhatsApp
- As of Oct 03, 2025, Netskope recognizes Signal as a cloud application. However, there is currently no predefined cloud app connector available for Signal within the Netskope platform.
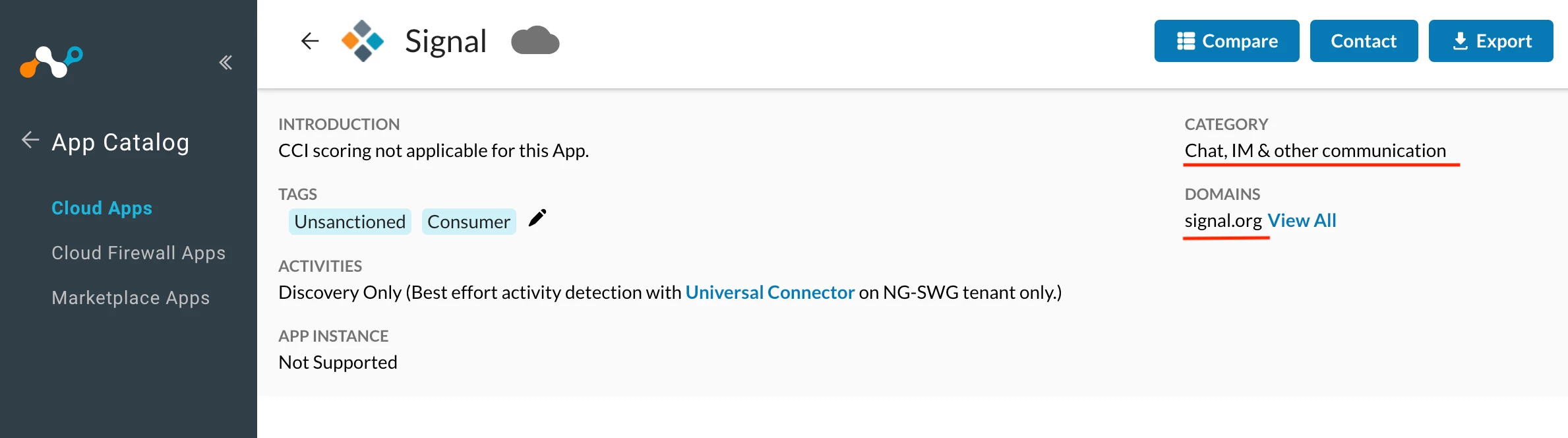
Details
- Signal can be accessed through its native application, which is available for the following platforms:
- Windows
- macOS
- Android
- iOS
- Linux (Debian)
- Signal native application uses Certificate pinning.
- What is Certificate pinning?
Certificate pinning is a security technique used to enhance the protection of network communications by ensuring that an application only trusts a specific SSL/TLS certificate or a set of certificates.
- Because the Signal native application employs certificate pinning, Netskope cannot perform SSL decryption on traffic generated by Signal.
- Without SSL decryption, the following controls cannot be applied:
- Netskope Data Loss Prevention (DLP)
- Netskope Threat Prevention
- Netskope Real-time Policy Controls for Post, Upload and Download activities
- In short, visibility on traffic generated by Signal is very limited
Netskope's default behaviour for Signal
- By default, Netskope has included Signal in the steering exceptions for both Windows and macOS platforms.
- All Signal traffic will bypass Netskope and be sent directly to its destination.
Sample
Note - Signal transaction logs will be stored locally on the end-user machine and cannot be routed to the Netskope Tenant.
Conclusion
- Visibility and Control: Netskope cannot perform SSL decryption on traffic generated by Signal. This limits the visibility into the content of Signal's communications.
- Data Protection: Due to Certificate pinning, Netskope lacks the ability to inspect and apply data loss prevention (DLP) policies to Signal communications, compromising data protection measures.
- Compliance: Ensuring compliance with regulations and industry standards becomes challenging when using Signal through Netskope. The platform's limited monitoring and control capabilities may lead to compliance violations.
- Threat Detection: Netskope cannot detect and respond to security threats originating from or targeting Signal usage, such as malware distribution or phishing attacks. Limited visibility and analysis capabilities contribute to this difficulty.
Terms and Conditions
- All documented information undergoes testing and verification to ensure accuracy.
- Netskope Engineering is continuously working on product enhancements. In the future, additional controls may become available to address some of the limitations mentioned earlier. If any such changes are brought to our attention, we will promptly update the documentation to reflect them.
Notes
- This article is authored by Netskope Global Technical Success (GTS).
- For any further inquiries related to this article, please contact Netskope GTS by submitting a support case with 'Case Type – How To Questions'.
What to Read Next? | |
|---|---|
| All about - ‘WhatsApp’ | Link |
| Use Cases: Generative AI | Link |
| Limitations with Telegram (Web Access & Native App) | Link |







