
 Netskope Global Technical Success (GTS)
Netskope Global Technical Success (GTS)
SMTP DLP - How to Block Sensitive Content Shared Over Gmail
Netskope Cloud Version - 129
Objective
How to Block Sensitive Content Shared Over Gmail Using Netskope SMTP DLP
Prerequisite
Netskope Email DLP for Gmail License is required
Context
Configuration required for blocking the sensitive data shared over Gmail
Configuration
When you configure Netskope SMTP Proxy with Google Gmail. All outgoing emails from Google Gmail are sent to Netskope SMTP Proxy for policy evaluation and will be sent back to Gmail for mail delivery.
Step1:
Please ensure that the upstream MTA in the Netskope tenant, as well as Content Control and traffic flow from Gmail to Netskope are configured correctly.
For detailed instructions, kindly refer to the documents below:
- Configure the Gmail server and the upstream MTA in the Netskope tenant
- Configure Netskope SMTP Proxy in Google admin center
- Configure content compliance to send traffic from Gmail to Netskope
Note: The above configuration will enable normal traffic flow through Netskope.
Step 2:
To block sensitive emails, you will need to add an additional content compliance rule similar to the previous one. The required change is to update the expressions as shown below:
“Location: Full Headers
Contains text: X-Netskope-Action:Block”
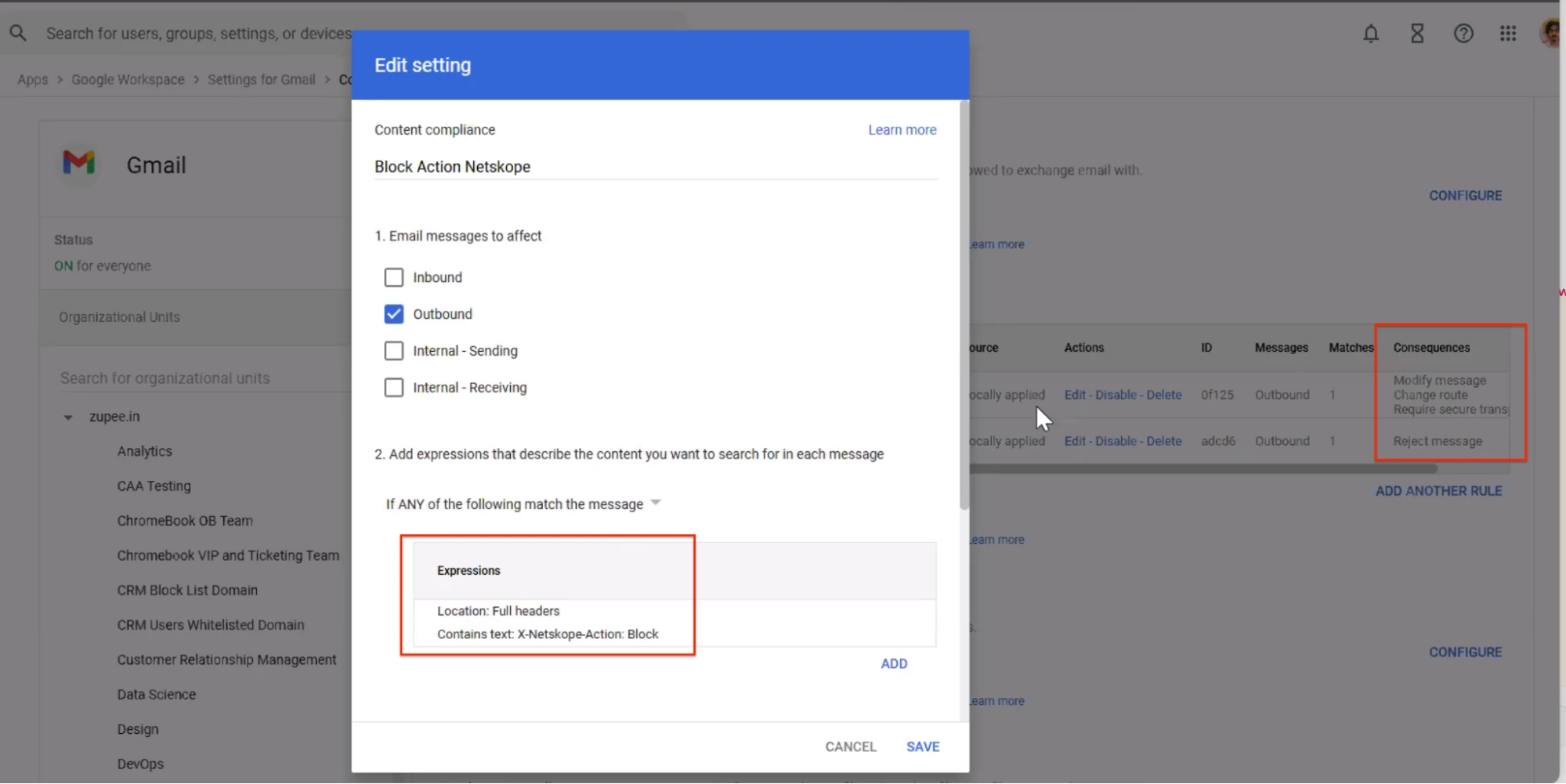
Note: Point number three is the key step in this content compliance rule: If the above expressions match, do the following.
Instead of selecting Modify the message, choose Reject message.
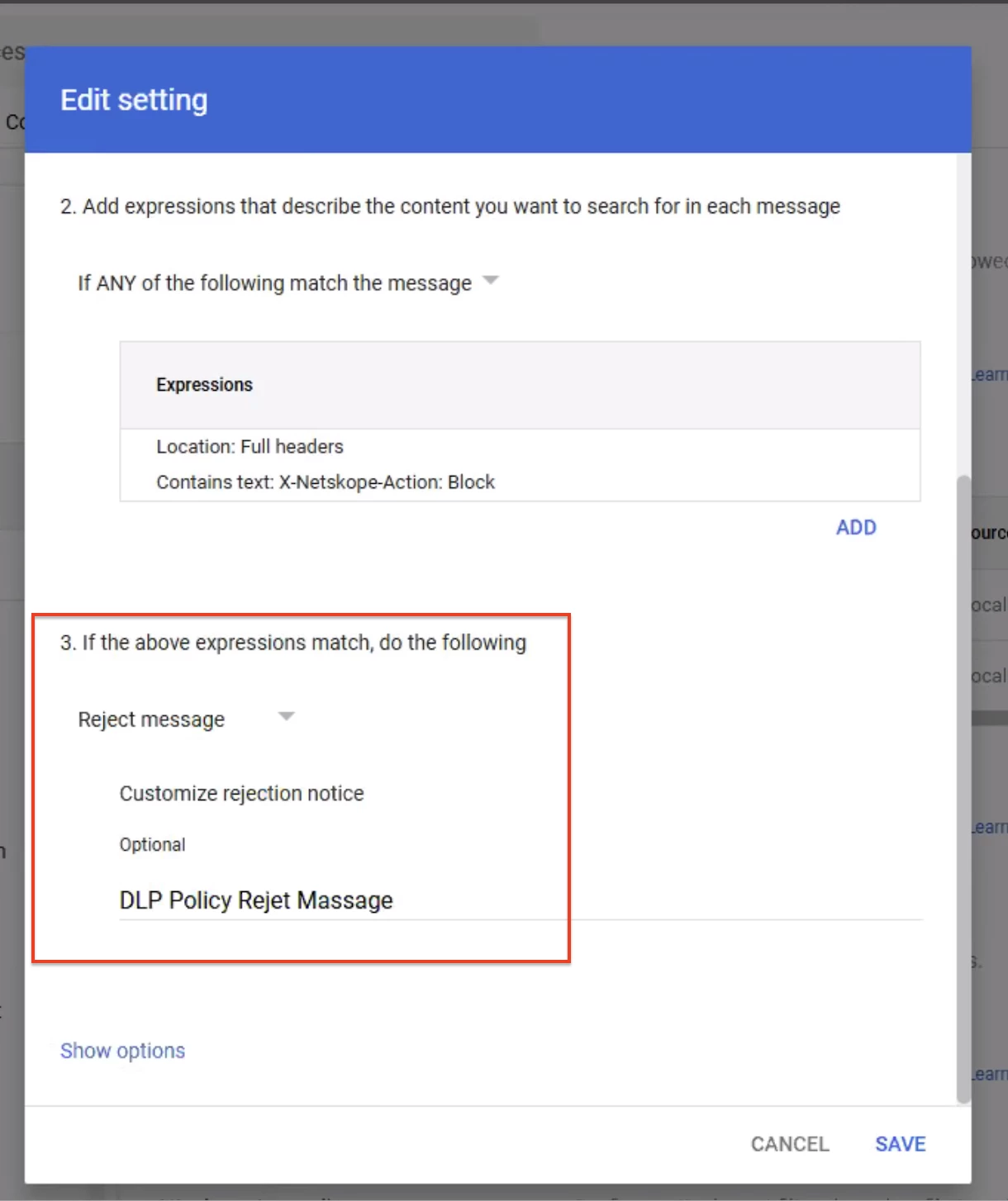
You can add a customized rejection notice.
Step 3:
Either create a new Real-Time Protection (RTP) policy or update the headers in the existing RTP policy.
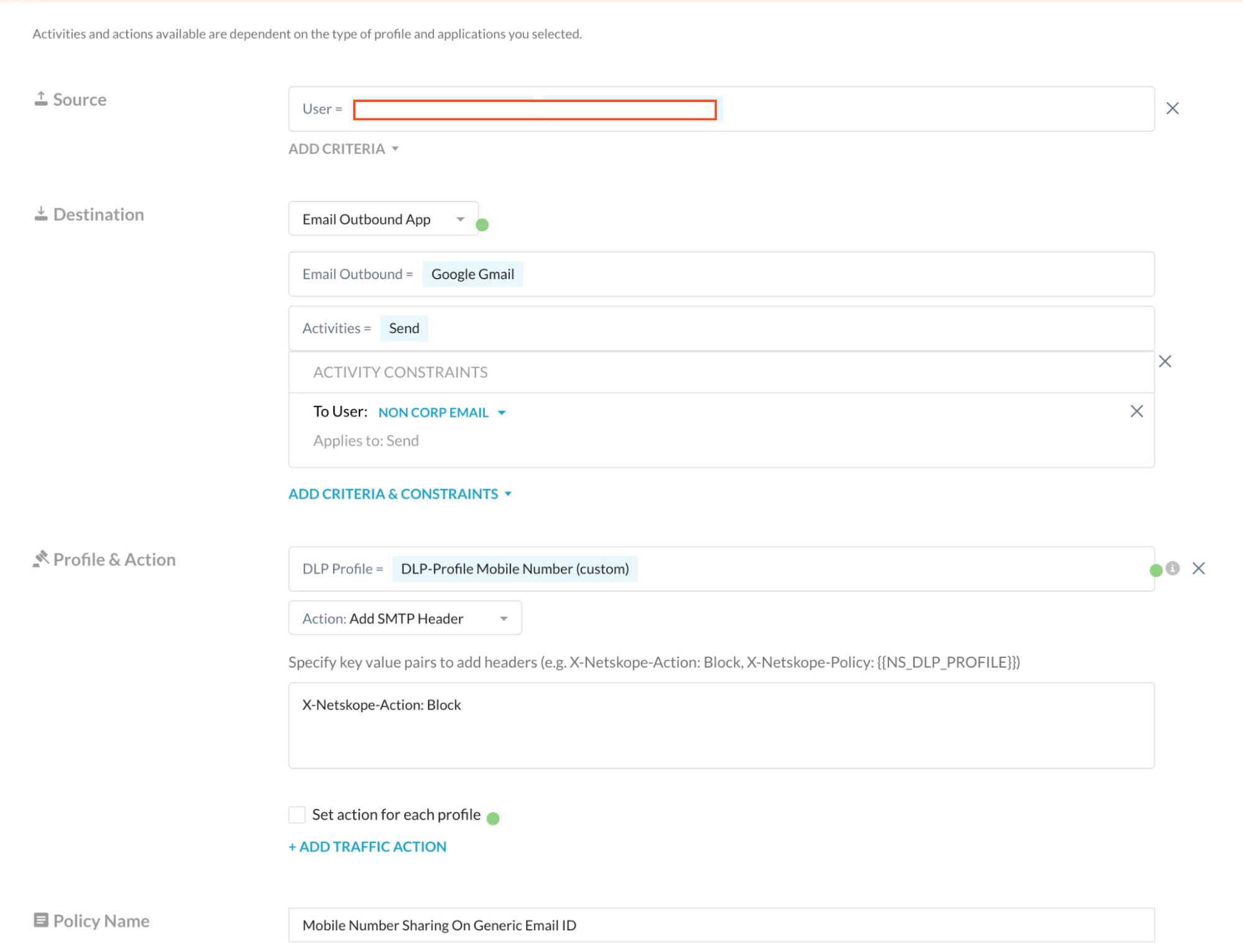
Verrification
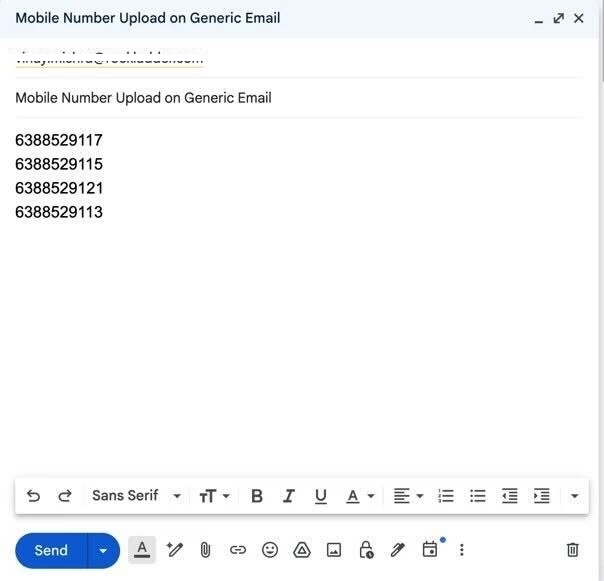
Attempt to send an email containing mobile numbers data to an external domain recipient. The email should be blocked by Gmail based on the injected SMTP header, and the user should receive a notification email with the reason.

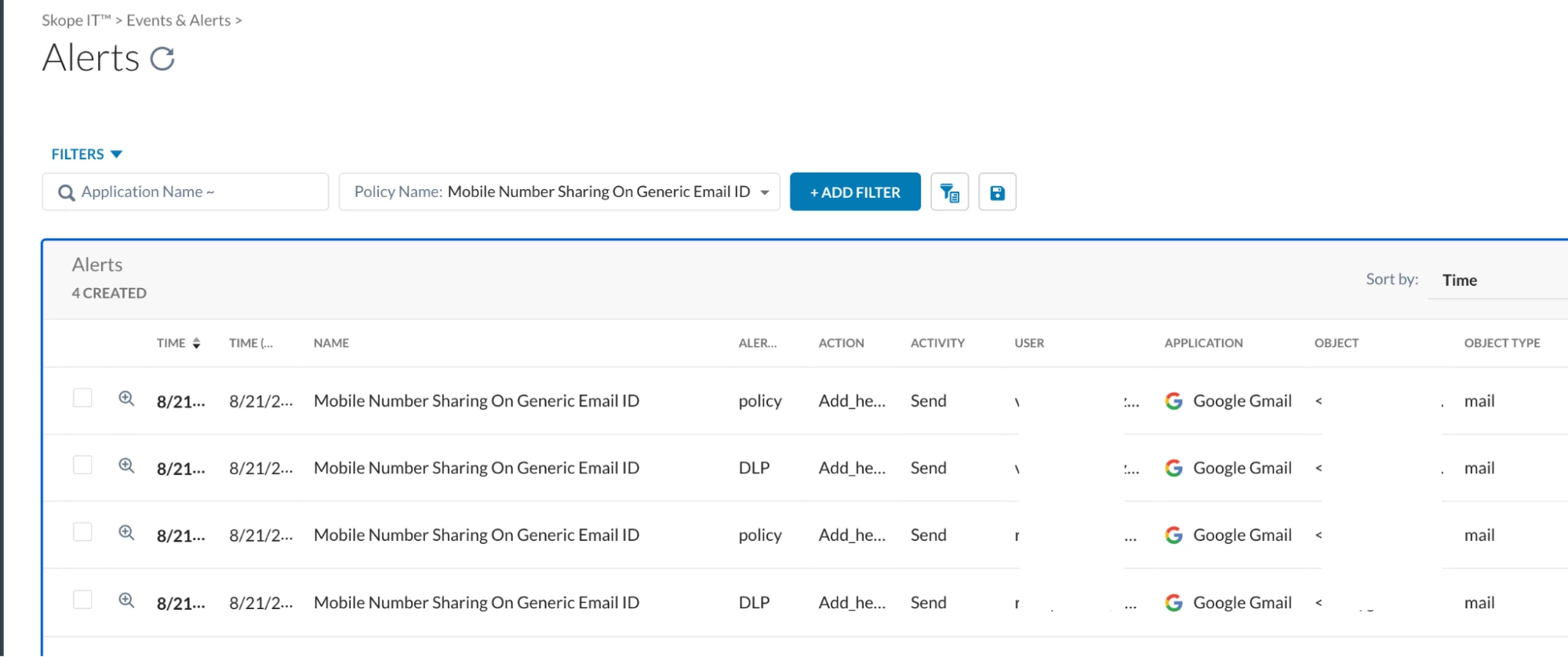
Always test the above policy on a subset of users before rolling out in production.
Terms and Conditions
- All documented information undergoes testing and verification to ensure accuracy.
- In the future, it is possible that the application's functionality may be altered by the vendor. If any such changes are brought to our attention, we will promptly update the documentation to reflect them.
Notes
- This article is authored by Netskope Global Technical Success (GTS).
- For any further inquiries related to this article, please contact Netskope GTS by submitting a support case with 'Case Type – How To Questions'.






