

 Netskope Global Technical Success (GTS)
Netskope Global Technical Success (GTS)
Netskope Socks5 Proxy for FTP Clients
Netskope Cloud Version - 132
Objective
Applying Inline controls on FTP Clients to block access to unwanted FTP Servers
Prerequisite
Netskope Cloud Firewall License with Socks5 Proxy Feature enabled
Context
This article explains how a SOCKS Proxy can be used to route traffic from FTP clients to enforce inline controls such as blocking access to unauthorized FTP servers or restricting file uploads.
Do You Know?
- The need for SOCKS5 Proxy support is driven by a critical security gap in Non-Web traffic. By forcing all users through the SOCKS5 proxy, companies can gain granular control to restrict access to only approved protocols and destinations.
- Netskope already has an explicit proxy for Web traffic but not for Non-Web traffic and this is what the SOCKS5 Proxy is for.
- It provides connectivity to applications/traffic coming from airgap environments.
- Non-web traffic like FTP, SFTP, SSH, etc on TCP over IPSec, GRE, or Netskope Client can be routed through SOCKS5 proxies. This forced routing immediately eliminates a key attack vector by preventing direct external DNS queries from end clients.
- If you are entitled to Cloud Firewall License, Raise a support case to enable ‘Socks5 Proxy’ feature for your tenant.
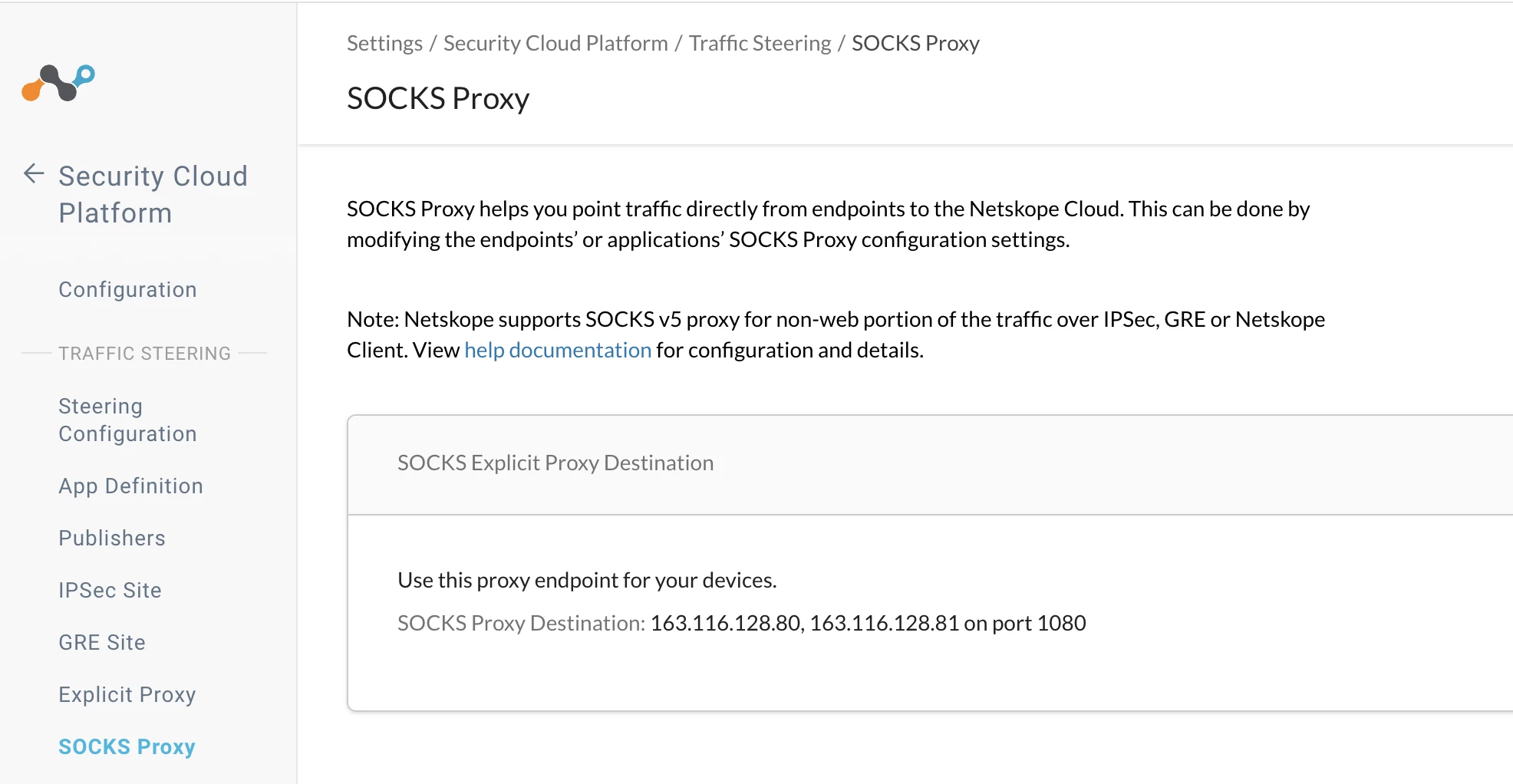
- Once the Socks5 Proxy feature is enabled, You will find the SOCKS Proxy setting under Settings > Security Cloud Platform > SOCKS Proxy Page.

Author Notes
To learn more about Netskope Socks5 Proxy, Please review the following KB article
Let’s begin
We will be covering 2 FTP related use-cases in this article:
- Blocking Access to Unauthorized FTP Servers
- Restrict Upload Activity to FTP Server
Use-Case 1: Blocking Access to Unauthorized FTP Servers:
Configuration
For this article, I will be using 2 FTP Server Setup.
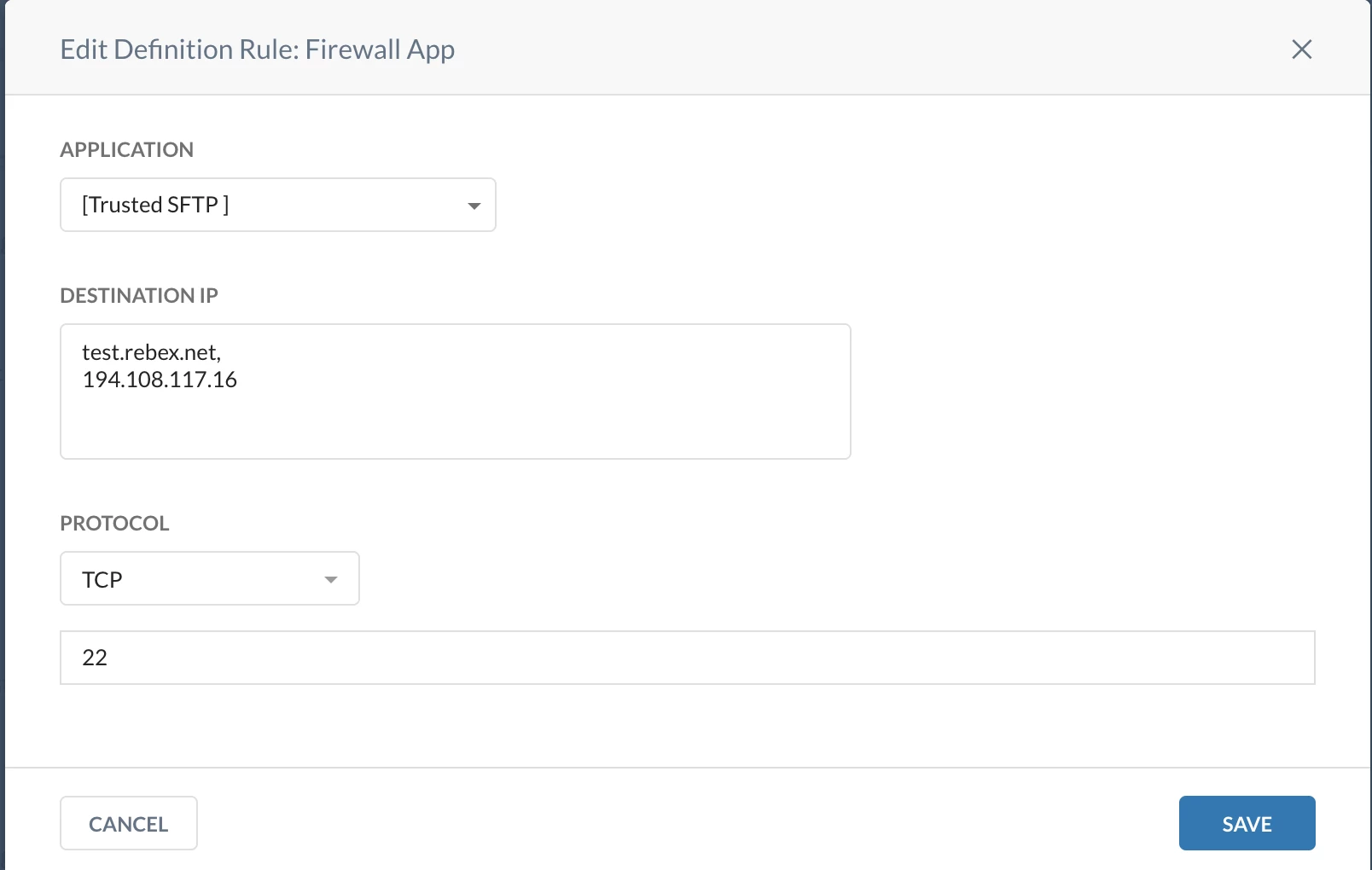
Server - 1 : Allow: test.rebex.net
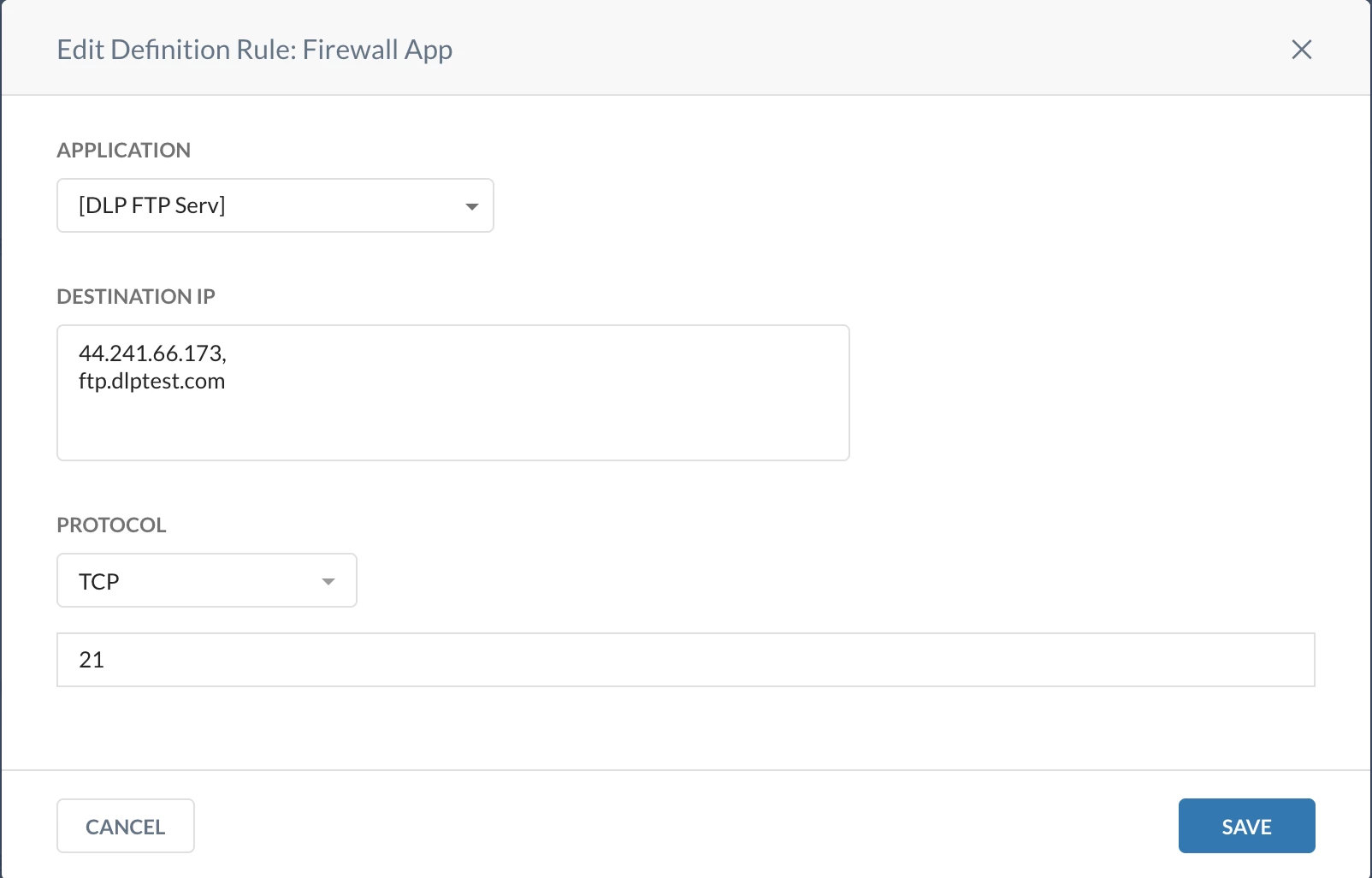
Server - 2 : Block: ftp.dlptest.com
Step 1: Create a Firewall App definition for Server - 1 and Server - 2
Path: Netskope Tenant UI >>> Settings >>> Security Cloud Platform >>> App definition - - - Cloud & Firewall Apps
Server - 1 Firewall App:

Server - 2 Firewall App:

Step 2: Create a Real Time Policy to allow access to Server-1 and block access to Server-2
Path: Netskope Tenant UI >>> Policies >>> Real-time Protection >>> New Policy
Allow access to Server - 1:

Block access to Server - 2:


Verification
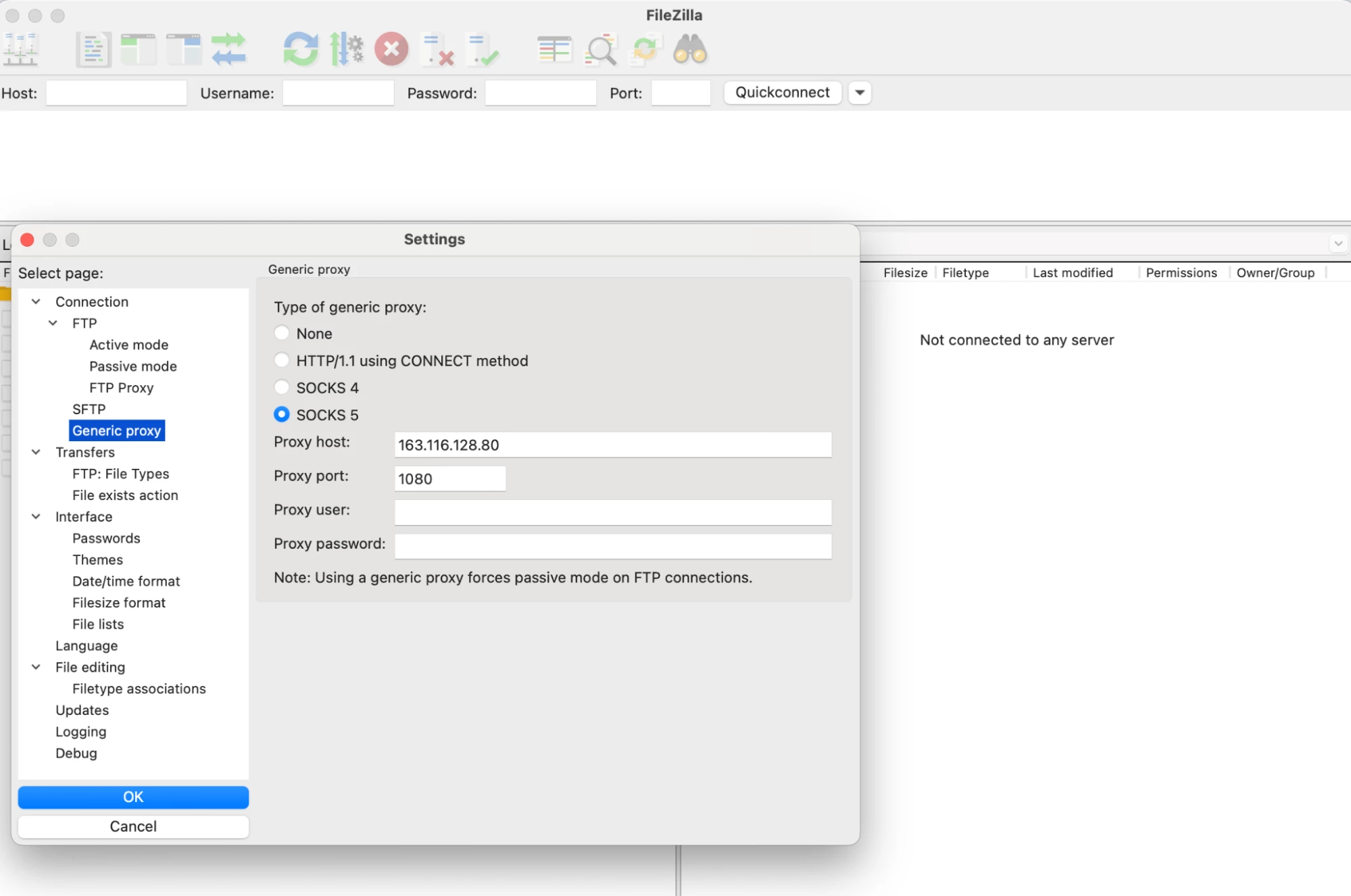
In this test scenario, FileZilla application traffic will be routed through a SOCKS5 proxy.
Socks Proxy setting in Filezilla: SOCKS5 Proxy can be configured using any of the destination given on the SOCKS5 Proxy Page along with the port 1080

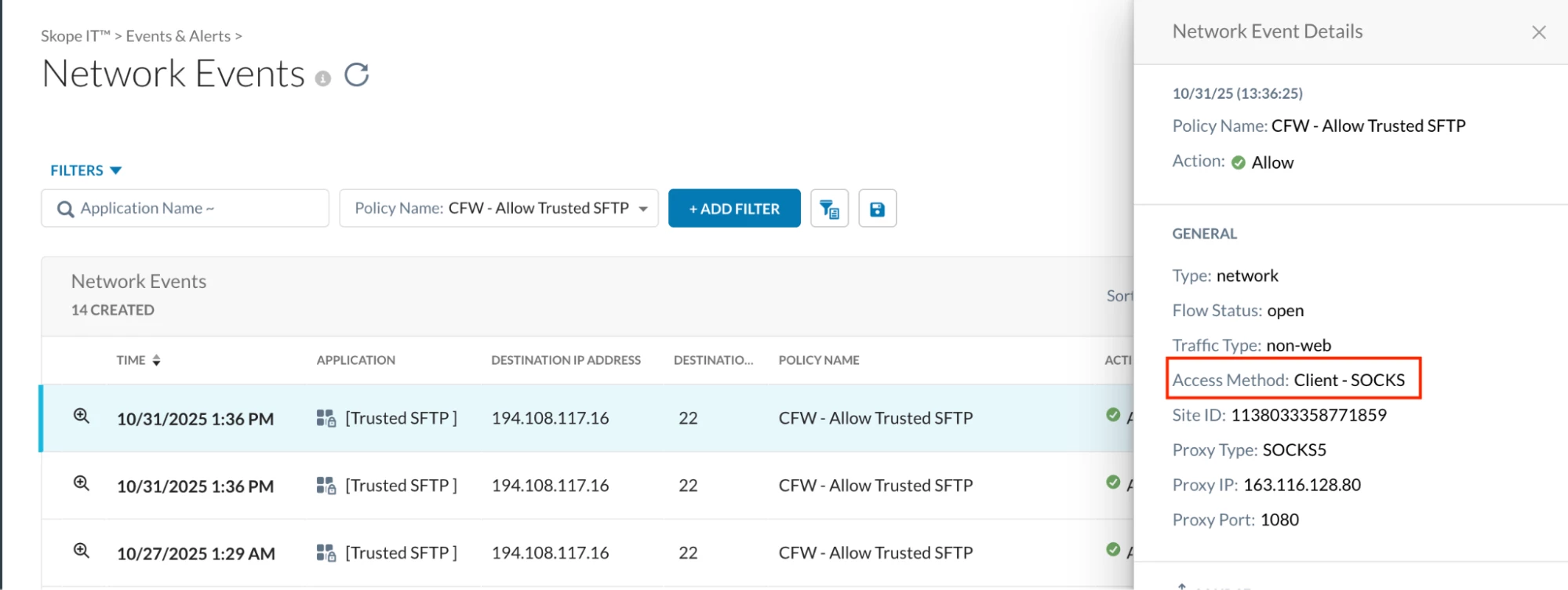
Trying to connect to blocked FTP Server:
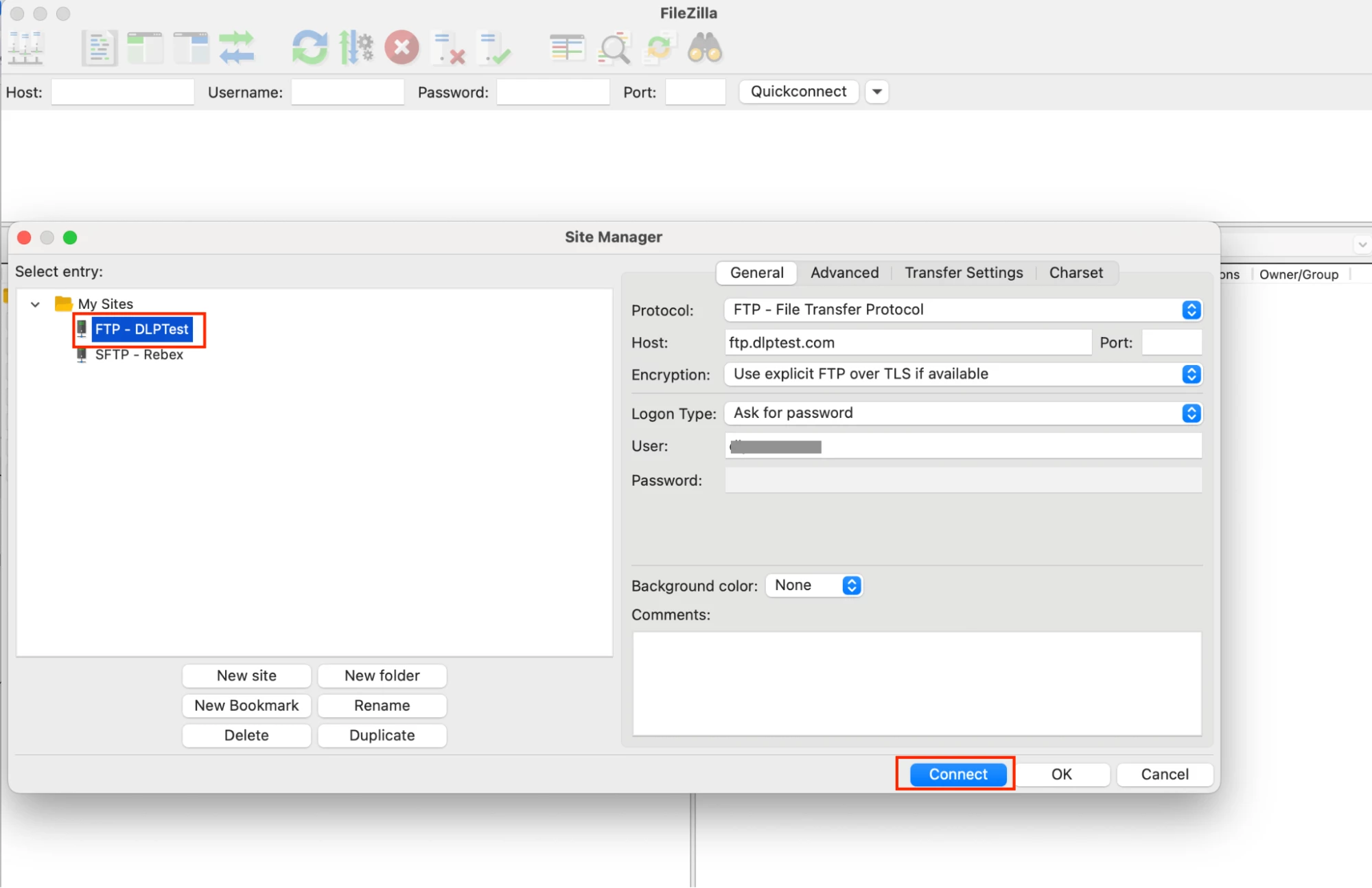

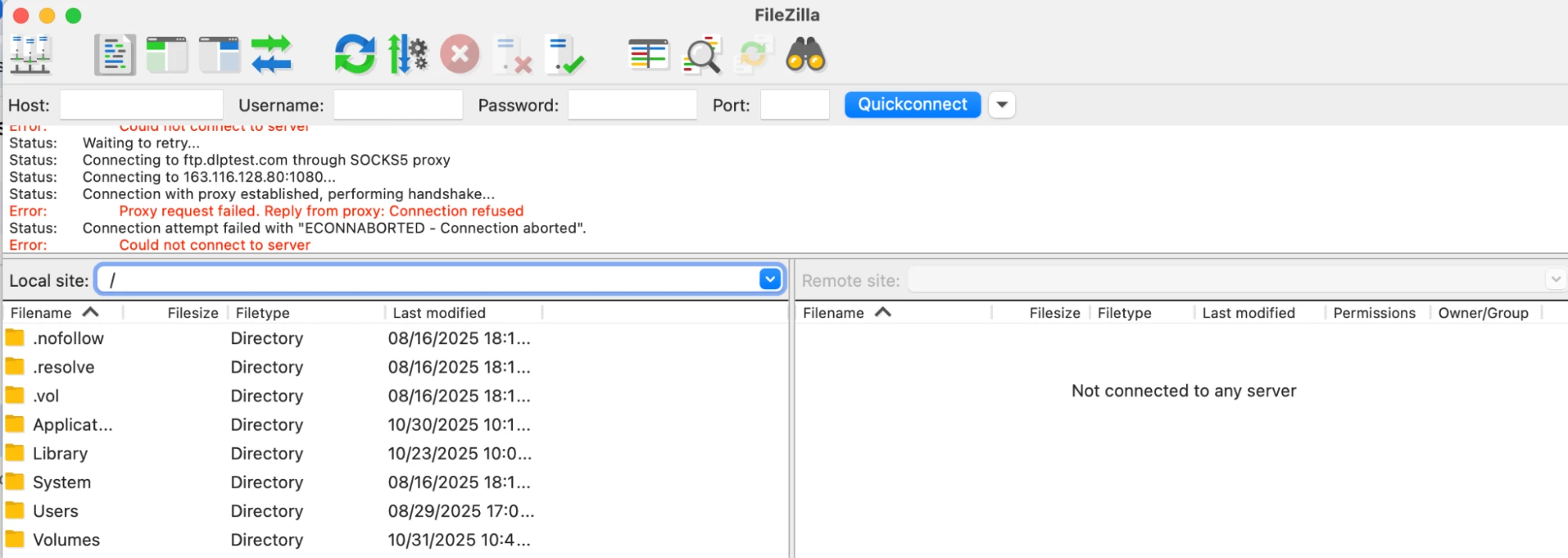

You will see that Filezilla is trying to connect ftp.dlptest.com through SOCKS5 Proxy but the connection is refused

Path: Netskope Tenant UI >>> Skope IT >>> Alerts


Try to connect to authorized FTP Server:


The connection to authorized FTP Server is allowed:

Path: Netskope Tenant UI >>> Skope IT >>> Alerts

Use-Case 2: Restrict Upload to FTP Server using Socks proxy:
Configuration
You can choose to block upload to complete FTP Application or only to specific FTP Server. For this article, I will be blocking the upload to the entire FTP Server and only allow download
Path: Netskope Tenant UI >>> Policies >>> Real-time Protection >>> New Policy
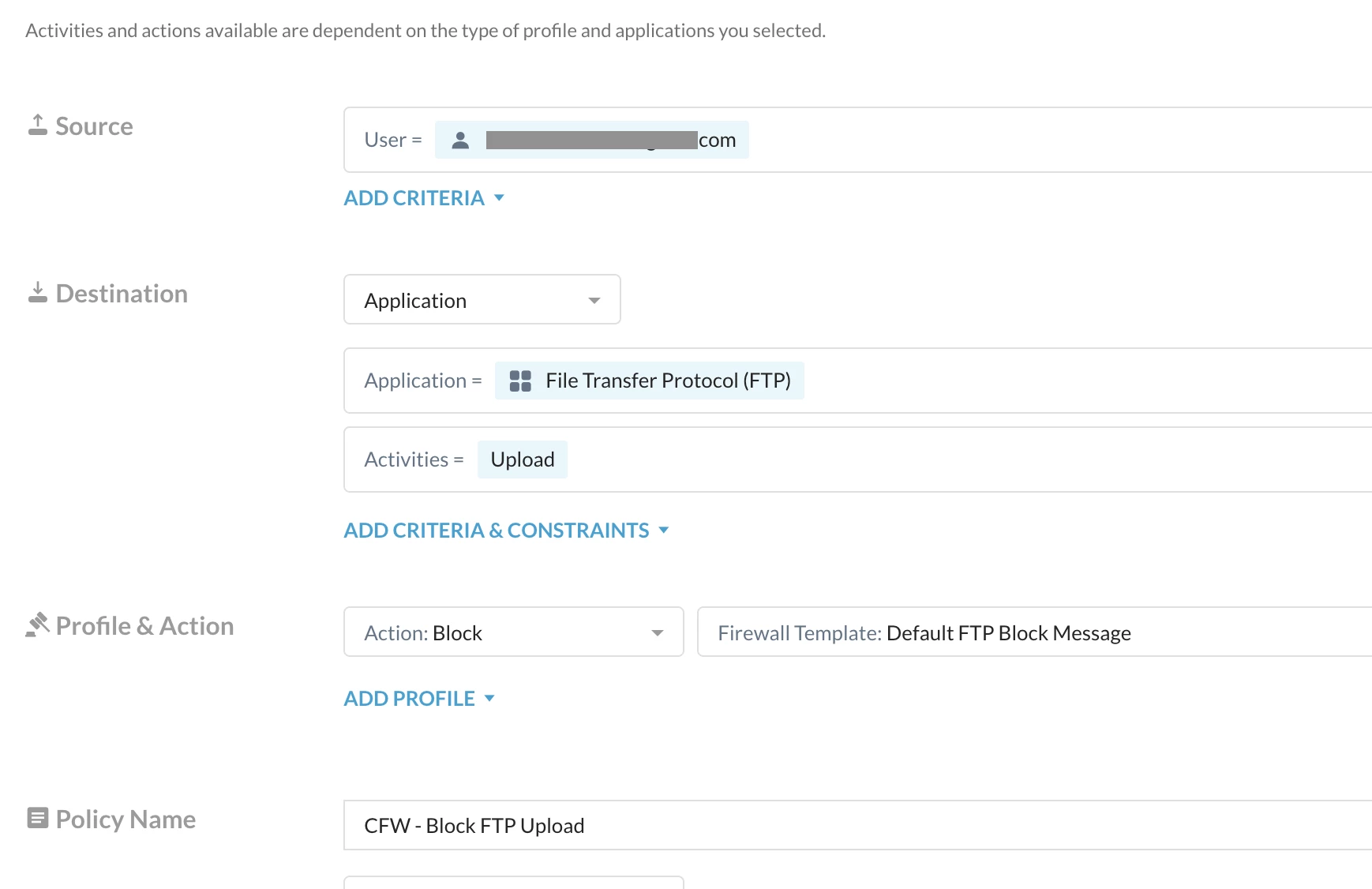

Verification
Try to upload data to FTP Server
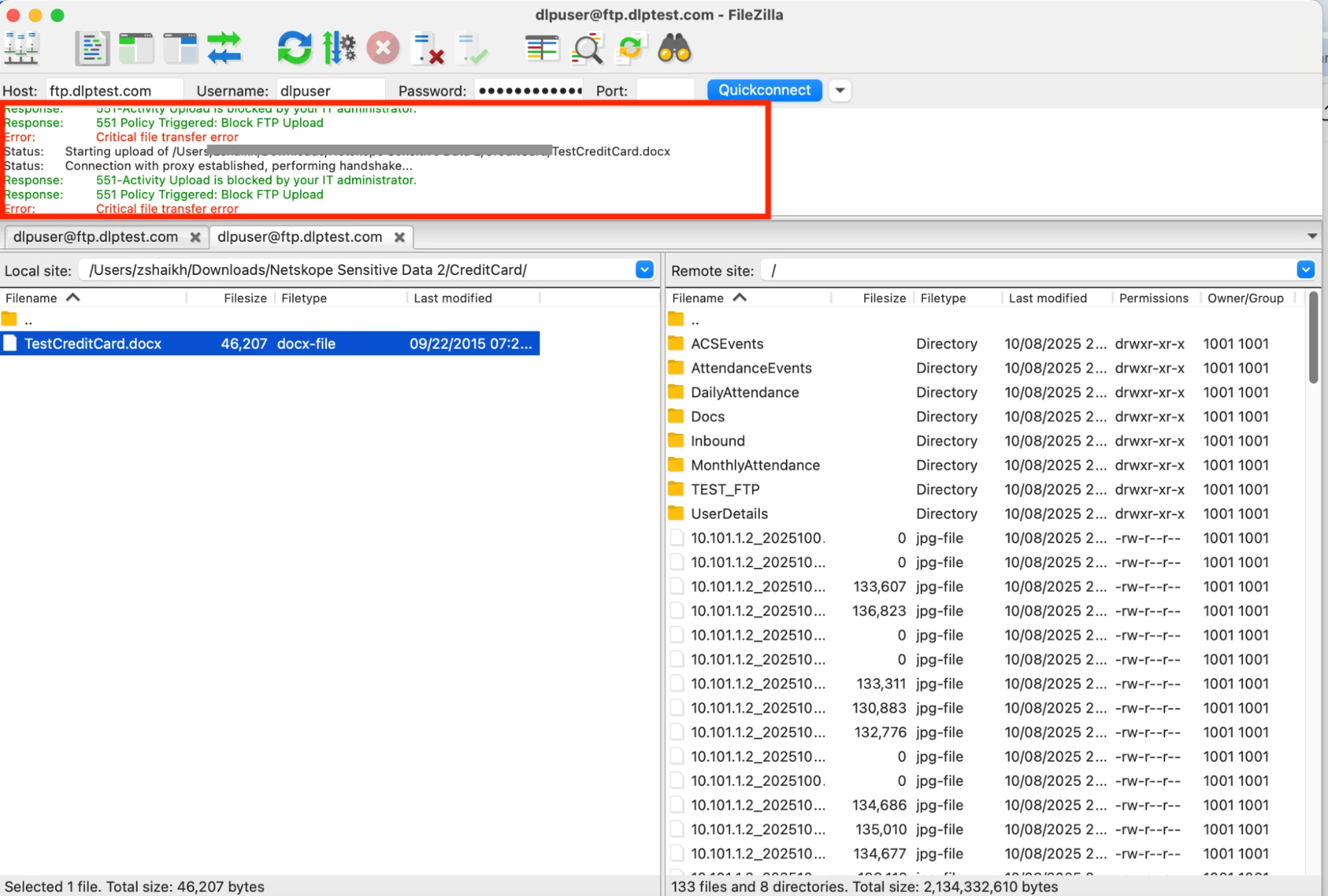

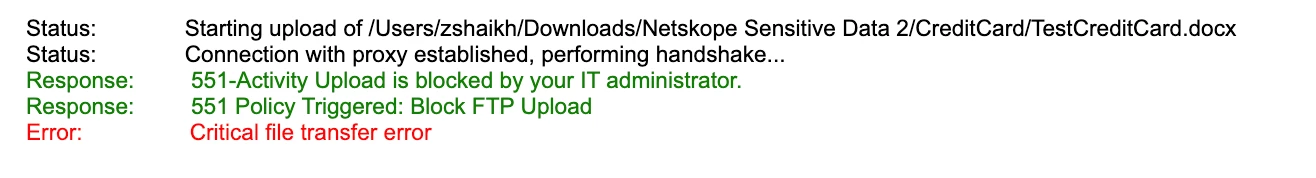
You will see that the upload is blocked through Socks5 Proxy



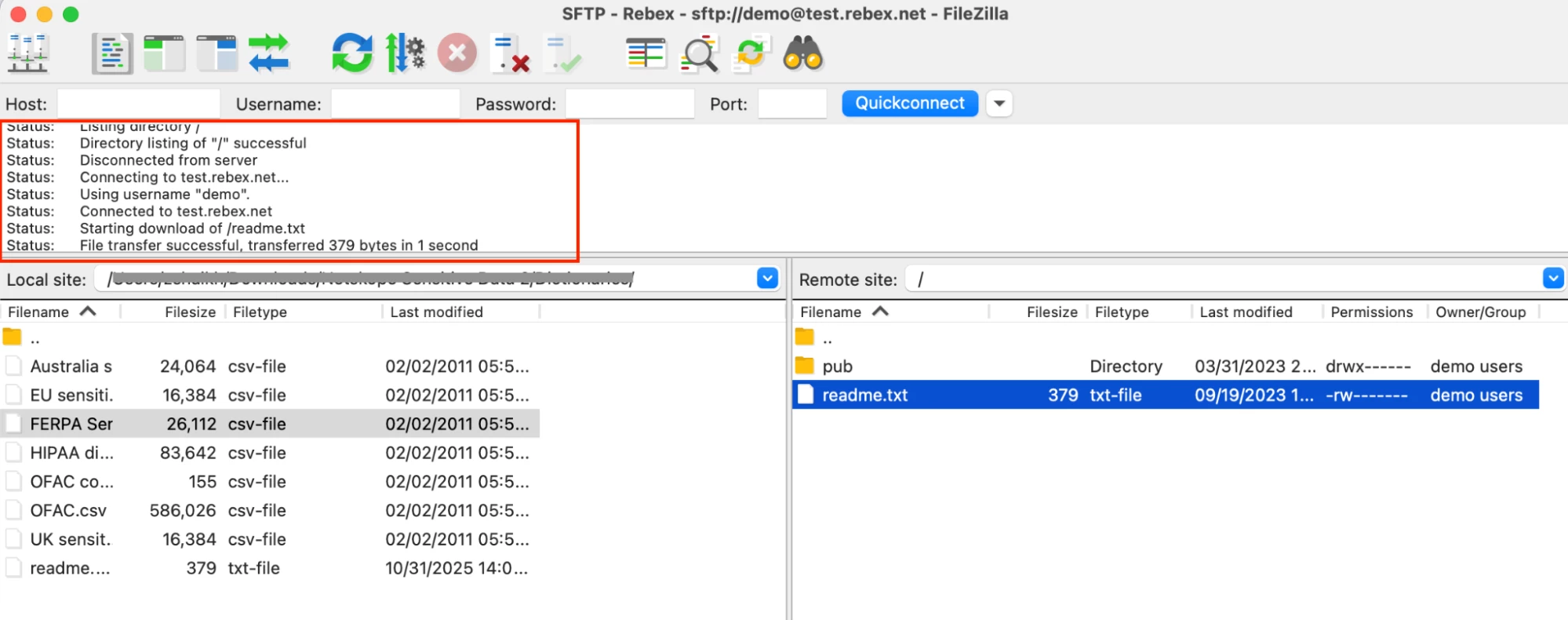
While the download was successful:
Terms and Conditions
- All documented information undergoes testing and verification to ensure accuracy.
- In the future, it is possible that the application's functionality may be altered by the vendor. If any such changes are brought to our attention, we will promptly update the documentation to reflect them.
Notes
- This article is authored by Netskope Global Technical Success (GTS).
- For any further inquiries related to this article, please contact Netskope GTS by submitting a support case with 'Case Type – How To Questions'.






