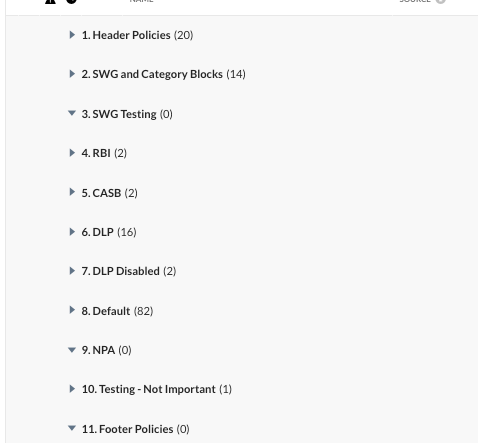
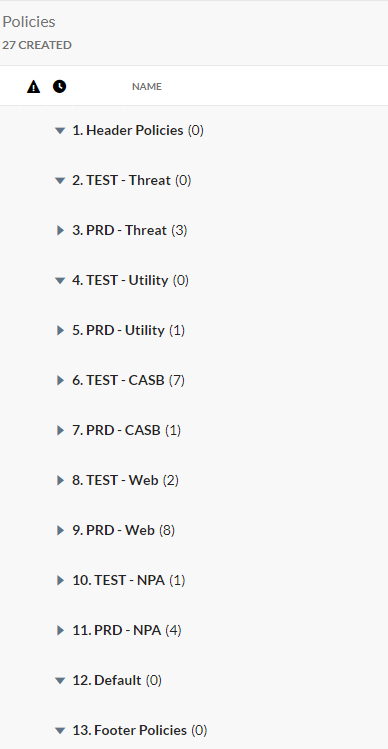
With the updates to RBACv2 within the Netskope console, it adds Policy Groups. As we investigate this feature and how best to utilize it, we are wondering how other Netskope teams are using them especially when you already have a fully developed policy list.
Sign up
Already have an account? Login
Sign in or register securely using Single Sign-On (SSO)
Employee Continue as Customer / Partner (Login or Create Account)Login to the community
Sign in or register securely using Single Sign-On (SSO)
Employee Continue as Customer / Partner (Login or Create Account)Enter your E-mail address. We'll send you an e-mail with instructions to reset your password.