Microsoft’s Azure Active Directory is widely used by thousands of organizations around the globe. It is the largest directory and identity provider in the world with this trend only accelerating as more and more organizations migrate away from on-premises Active Directory. Those tens of thousands of organizational directories present an interesting security challenge to ensure users only access authorized tenants and resources. Microsoft has long provided Tenant Restrictions as a means to restrict logins to authorized tenants.
In April of 2022, Microsoft announced a new, robust method of controlling access to Azure AD directories and applications called Cross-tenant Access policies. Cross-tenant access takes the core concepts of tenant restrictions and provides a number of key enhancements. Cross-tenant Access policies are granular and allow administrators to specify combinations of users, groups, and applications for access control. This includes how your users can interact with external tenants and how external users can interact with your tenant. These are excellent controls that can now natively be managed within Azure AD. Recall though, that Tenant Restrictions were focused on what tenants should be allowed at all, not what users were allowed to do once granted access. Further, Cross-tenant Access policies were not designed to govern the initial login and restrict what tenants can be accessed in the first place. Microsoft still recommends using your enterprise proxy or firewall to enforce Tenant Restrictions. The big difference this time around is that Tenant Restrictions are now optionally a part of Cross-tenant Access Policies. By incorporating tenant restrictions into Cross-tenant Access Policies, Microsoft has simplified the enforcement and administration of access control policies. Further, the original Tenant Restrictions configuration required that you configure two headers:
|
Header name |
Header Value |
|
Restrict-Access-To-Tenants: |
Domains, directory IDs in comma separated list |
|
Restrict-Access-Context, |
Directory ID that set the tenant restrictions |
With Cross-tenant Access Policies, Microsoft has provided the sec-Restrict-Tenant-Access-Policy header which allows your proxy or firewall to provide the Azure AD directoryID and policy GUID to Microsoft’s login domains to enforce this policy on your corporate network and devices. The format of this header is:
|
Header name |
Header Value |
|
sec-Restrict-Tenant-Access-Policy |
<DirectoryId>:<policyGuid> |
Netskope supports this functionality using our Header Insertion functionality. Let’s take a look at this in action. I’ve created a very simple Cross-tenant Access policy that allows collaboration and logins to my personal Azure AD tenant:
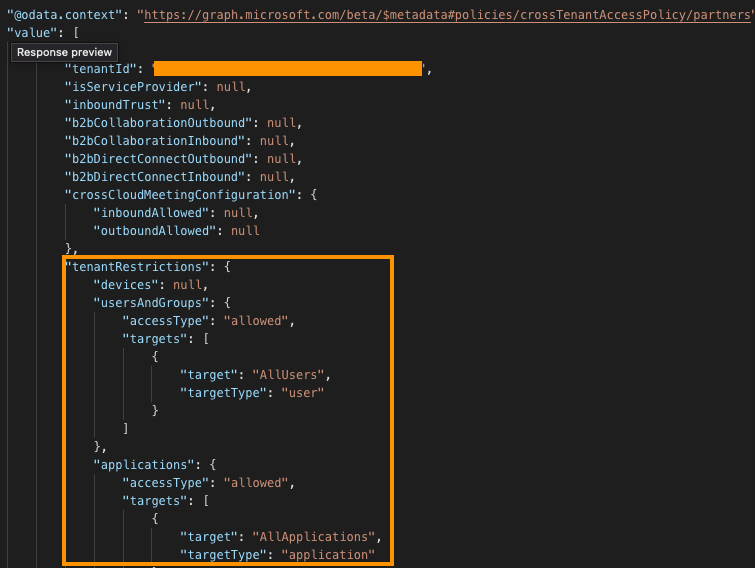
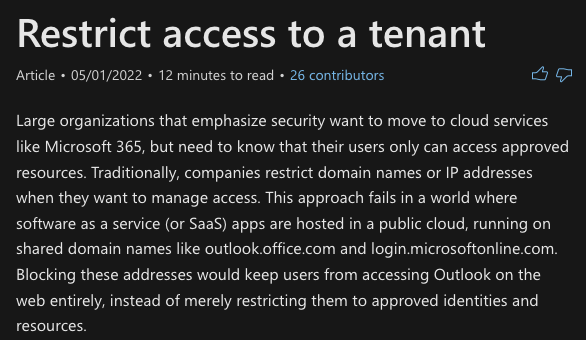
In my Netskope Tenant, I’ve configured this header insertion via the Cross-tenant Access Policy key:
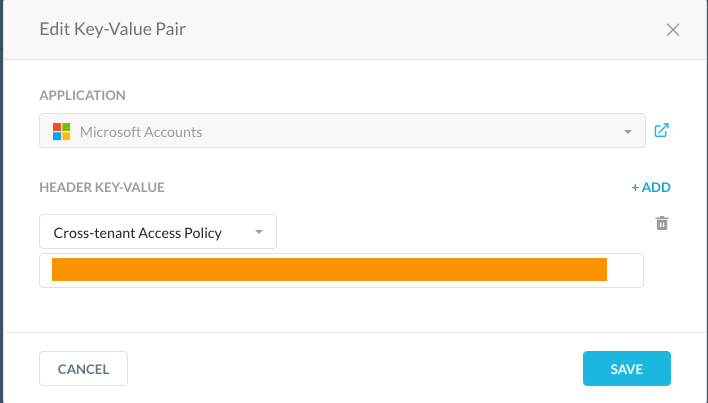
Now when I attempt to login to Office365 using my personal tenant and domain I’m allowed to login as this access was allowed in the policy above:
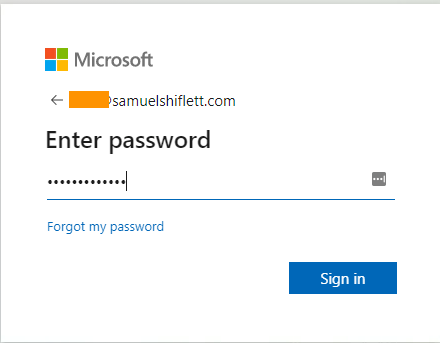
When I try to login to another tenant I’m blocked via a Microsoft generated block message that identifies that a tenant restrictions policy has blocked my access:
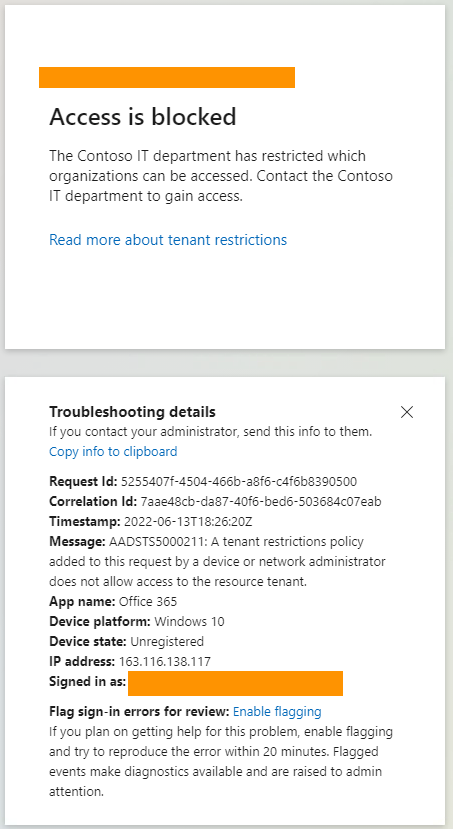
Just by configuring a single parameter in Netskope, I was able to apply the policies I’ve already created in Microsoft. This allows organizations leveraging Microsoft to securely use their enterprise collaboration, storage, email and other tools without recreating policies in Netskope or other third party tools. You can further complement these capabilities with Netskope’s instance awareness, activity awareness, and DLP including integrations with Microsoft Information Protection. This is just one example of Netskope’s continued partnership with Microsoft in addition to the numerous integrations that can be found here. You can also watch the video below to see this integration in action. As a final note, you may notice some differences in the UI in the video and your tenant. Netskope released a broader, generic header insertion feature that allows for generic header insertion for any site. Application Feature Support was integrated into this capability.








