Recently I stumbled upon an interesting campaign carried out by a threat actor dubbed Dark Pink and characterized by the exploitation of a legitimate cloud service, GitHub, to host the malicious payload. GitHub is a well-known service, categorized as "Development Tools" and "Technology" within the Next Gen SWG, and for which a dedicated connector allows to enforce granular security policies in terms of adaptive access control, DLP and threat protection.
However, it is common for threat actors to abuse even less-known cloud services for malicious purposes such as malware distribution, command and control and data exfiltration, and the above campaign is no exception. As a matter of fact in the above mentioned case, the attackers exploited an additional less-known cloud service, textbin[.]net, to deliver the malicious payload.
Netskope customers are protected out-of-the-box from the malicious exploitation of textbin[.]net as this service is already classified as "Security Risk - Compromised/malicious sites" and "Security Risk - Phishing/Fraud", however it can also use as a brilliant example of how easy is to create a custom connector in case a more granular control is needed.
In the specific case (but the same procedure applies to other similar services):
1. Go to "Settings > Security Cloud Platform > App Definition" and select "Cloud & Firewall Apps > New App Definition Rule > Cloud App".
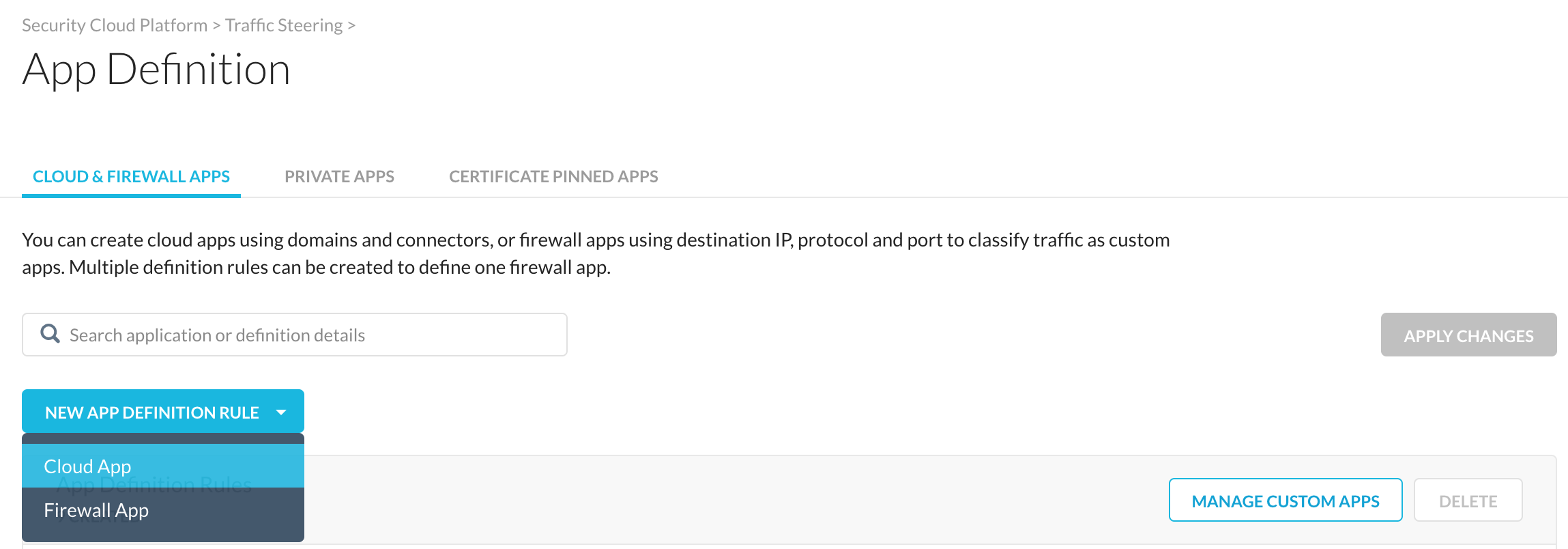
2. Assign a name to the application (in the specific case "textbin", select "Universal Connector" from the "Connector" section, click on "Add New Domain", and insert the specific domain(s) of the application for which the customer connector must be created. In the specific case there is just one single domain called "textbin.net". Click on the "+" button and save the new application.
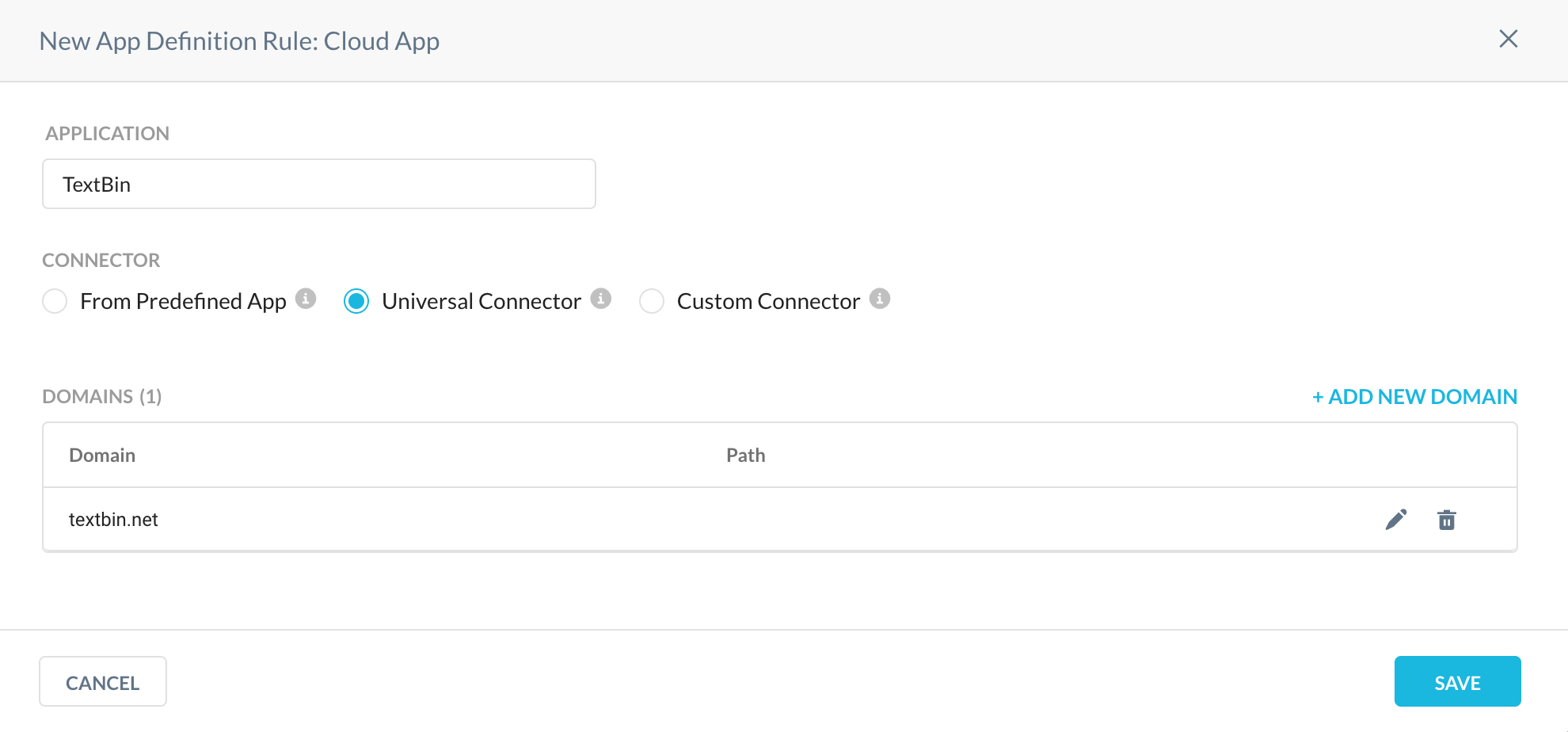
3. A new application is created and ready for a policy! Please note that the names of the custom applications are delimited by square brackets, so the name of the new app will be "[textbin]". Additioally, if the Next Gen SWG is steering all the web traffic you don't need to add the new application to a steering configuration.
4. The new application can be used in a policy. In particular the Universal connector allows to govern the following activities:
- Access Control: "Download", "Login Attempt", "Login Failed", "Login Successful", "Logout", "Upload".
- DLP: "Download", "FormPost", "Upload"
- Threat Protection: "Download", "Upload"
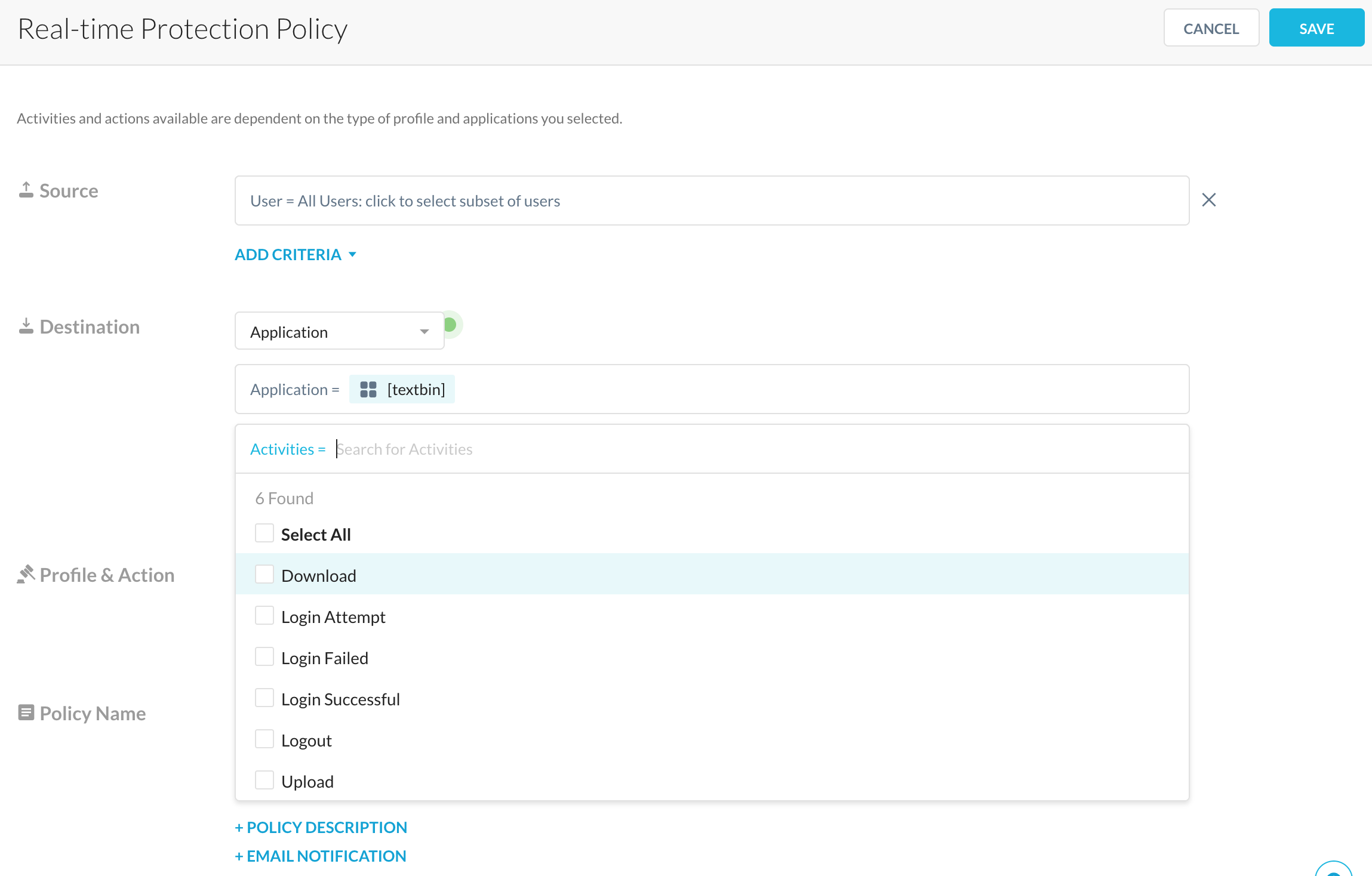
5. From now on, every potentially malicious activity can be governed!
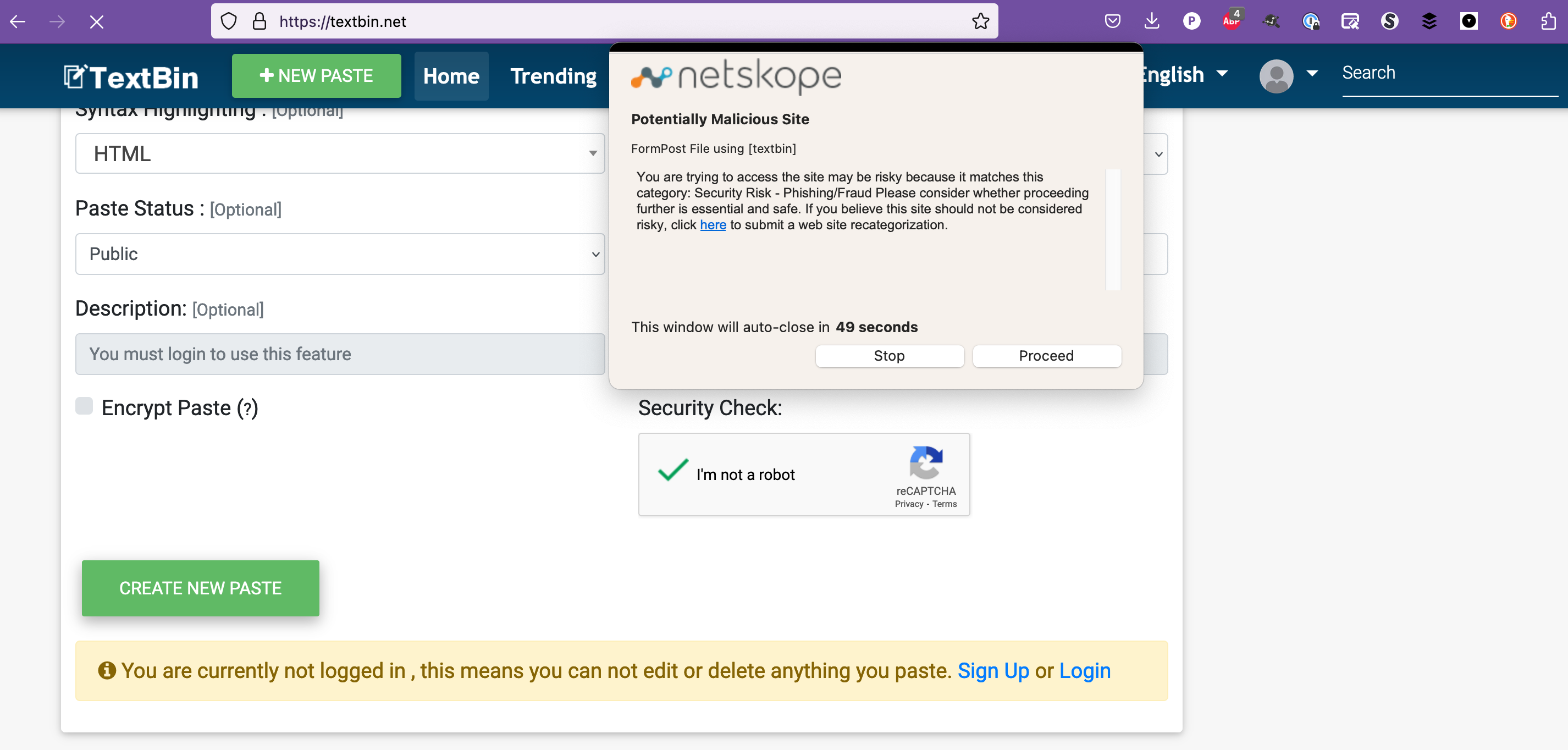
Enjoy a safer web!







