Doubts with NPA Web browser Private Access - SAML Azure AD
Hello community, as always, many thanks for your comments, advice, recommendations and your time.
I have currently configured in our Tenant for user synchronization with SCIM, from Azure AD and I have SSO for Admin console access, using Azure AD, everything work OK.
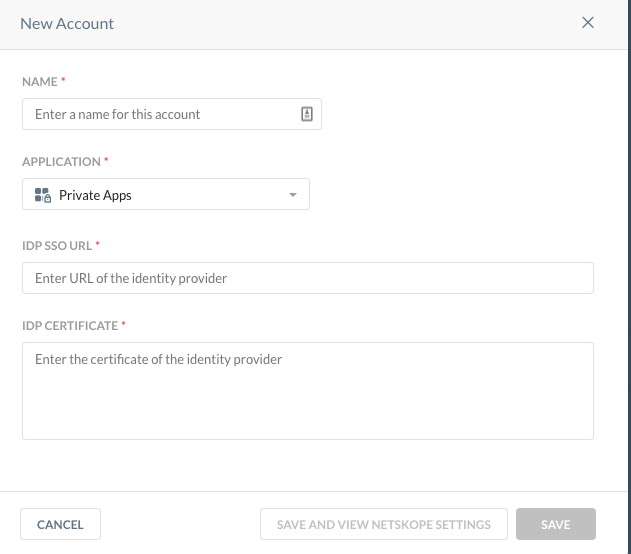
Now I have a huge and big doubt, I understand that for user Private Access via Web i.e. Clientless, a SAML - Reverse Proxy account must be configured.
That's my big doubt: I am looking for documentation that supports this configuration, ie Private Access Web browser access with SAML - Reverse Proxy with Azure AD, but I have not found, I have only found for Okta, among others, but with Azure AD nothing.
Configure Browser Access for Private Apps:
Reverse Proxy: https://docs.netskope.com/en/saml-reverse-proxy.html
So I understand that at this point it is not necessary that I federate with SSO my application, that is if I wanted to add a Private Access Web-Browser access to a URL of a simple example, the Web Interface of a Printer or Web access to the Web-Gui of a Firewall, Switch, router, etc, I should be able to do it without problems, using Web Browser Private Access Clientless. The Private web browser Clientless, Netskope is the gateway, where it redirects to the Azure-AD/Microsoft login, for access without third-party client without cleintes, so that this connection is authenticated with Netskope and in turn with Azure-Ad and then already allows me to enter the Web application ( https/http ) that the Publisher previously already has access and is reached by the publisher.
Now someone can support me clarifying these doubts:
1.- Should I create in Azure Ad a separate Enterprise Application for this SAML Proxy connection ? Can I use the SSO one ?
2 .- I must generate an Azure AD Enterprise application for each Private App that requires or only once and I can use this for all web private apps to generate (ie example the webgui router, firewall, printer, switch, etc ...?
3.- If I generate an Azure enterprise application, for the SSO of the Web-gui of the console, if I know that goes in the field of Identifier, but in the case of Reverse Proxy where do I get that information?
4.- If you can support me with a tutorial, guides, etc, I will be very grateful, because reading the official documentation I still do not reach the goal.
Thank you for your time, your advice and all the comments
@sshiflett @amurugesan @mkoyfman
I remain attentive
Best regards