How the Salesloft Drift breach highlights the urgent need for visibility into SaaS-to-SaaS connections.
The recent Salesloft Drift security incident has impacted hundreds of organizations and serves as a powerful reminder of a growing threat: risk from third-party SaaS-to-SaaS integrations. This attack exploited trusted connections between applications to access sensitive data, bypassing traditional security controls.
The attack chain: How stolen tokens led to data exfiltration
The incident began when a threat actor acquired OAuth and/or refresh tokens connected to Salesloft's Drift application. Drift, an AI chatbot, integrates deeply with platforms like Salesforce to log user interactions, leads, and meeting data.
By using these stolen tokens, the attacker could effectively impersonate the legitimate Drift application. This allowed them to make authorized API calls to their victims' Salesforce instances, exfiltrating sensitive customer accounts and meeting information. The full extent of data loss for each victim depends entirely on how their Salesforce instance was configured.
The security blind spot: Do you know what’s connected to your Salesforce?
This incident exemplifies a critical challenge for security teams. Business-led IT, particularly in go-to-market (GTM) teams, often integrates third-party apps into core platforms like Salesforce without direct security oversight. This creates a hidden web of SaaS-to-SaaS connections, where each integration is a potential attack vector. Without the right tools, security has no way to see, assess, or manage the risk from these applications.
From blind spot to control with Netskope SSPM
Netskope SaaS Security Posture Management (SSPM) eliminates this blind spot by providing immediate and continuous visibility into all third-party applications connected to your corporate SaaS environment.
Proactively report on connected apps
Using Netskope, you can generate automated reports that inventory every application connected to Salesforce. This allows you to differentiate between what is known and expected versus what is unknown and potentially risky. The special-purpose "Salesloft Drift Edition" report helps companies evaluate these connected apps and their security posture against established rules.
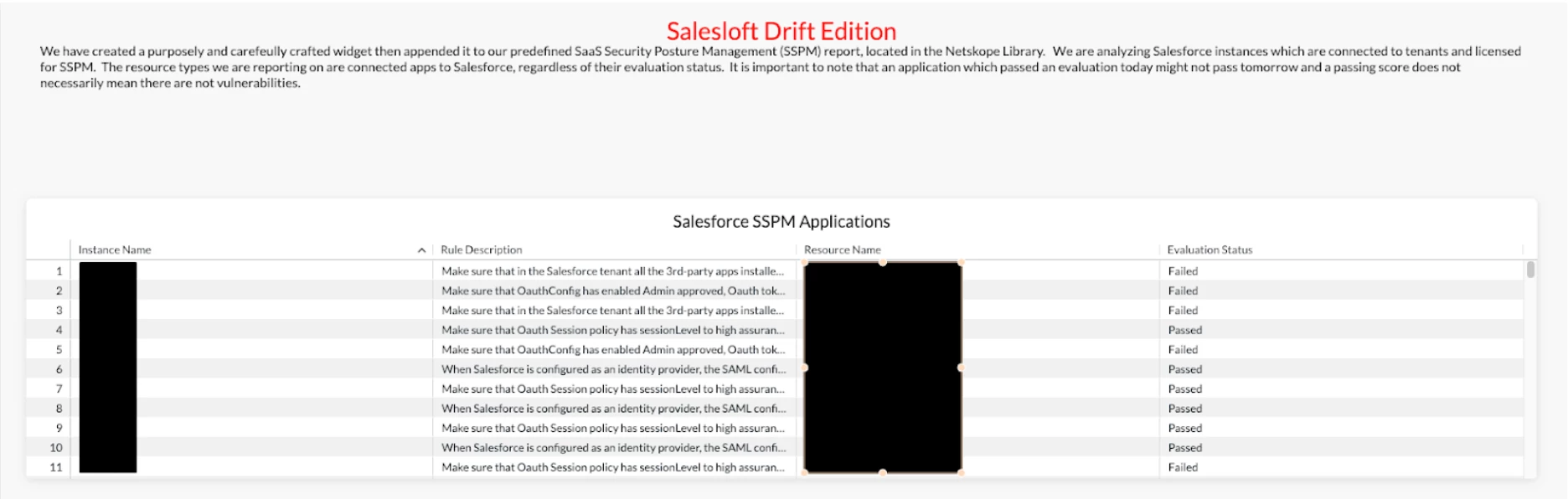
The widgets used to examine 3rd party applications enhances the existing “SaaS Security Posture Management” NAA report which includes the following for all applications utilizing SSP:
- Posture Summary;
- Detailed Findings;
- #Failed Findings by Domain;
- #Failed Findings by MITRE ATT&CK; and,
- Posture Findings, display limitations of 5000 rows.
It is important to note that an application which passed an evaluation today might not pass tomorrow and a passing score does not necessarily mean there are no vulnerabilities.
Triage risk in real time
For immediate analysis, the Netskope SSPM dashboard provides a live dashboard of all connected third-party apps. This allows your team to instantly see every connection, sort by risk level, and begin triage on applications that pose a critical threat.
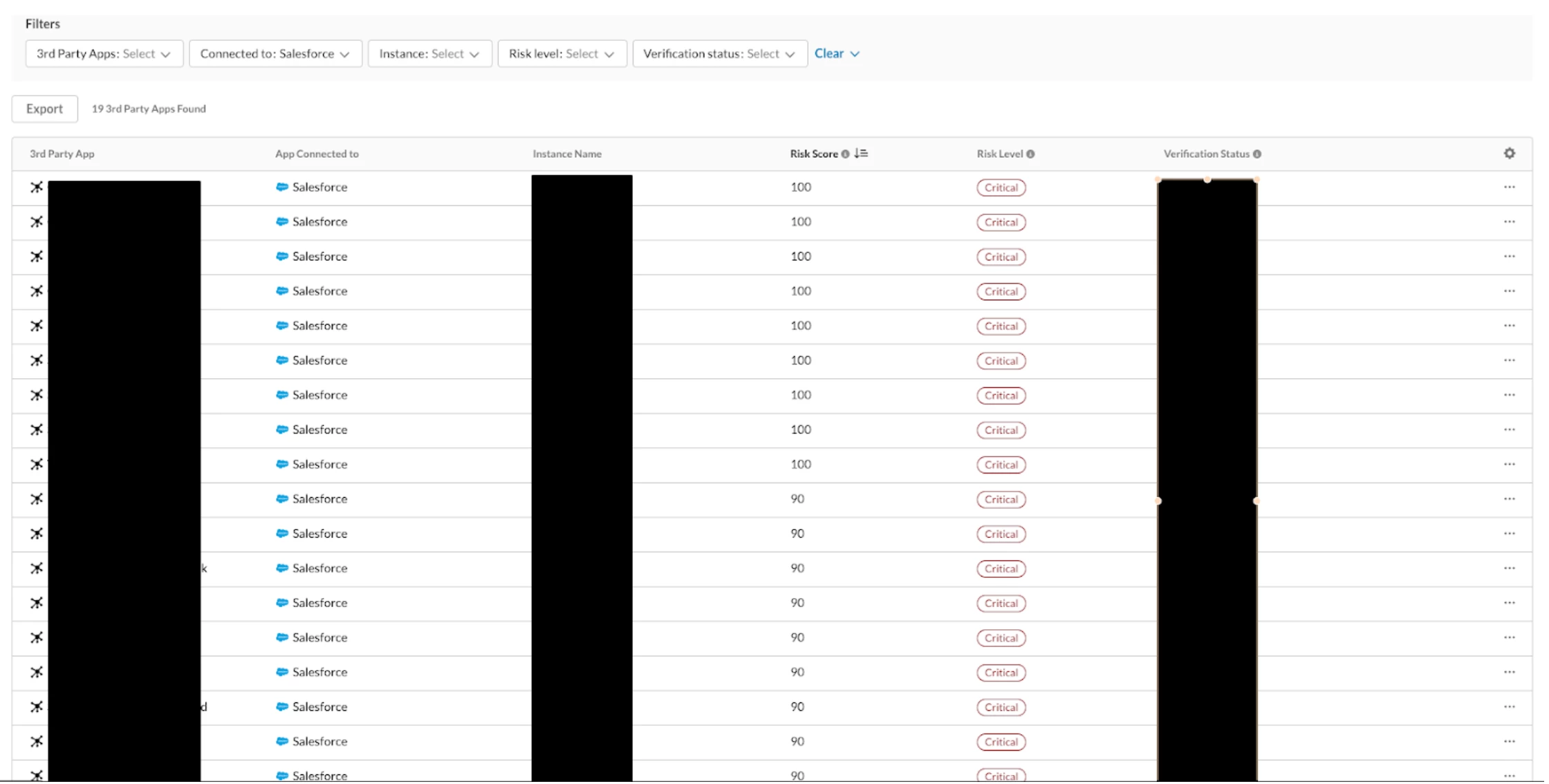
Figure 2: The Netskope SSPM dashboard offers real-time visibility into all connected apps, allowing security teams to sort by risk level and begin immediate triage.
From visibility to action
Discovering a risky connection is the first step. With the visibility Netskope provides, your security team can take decisive action to protect your data:
- Assess risk: Prioritize applications based on their permissions and risk score.
- Revoke credentials: Immediately revoke OAuth tokens for unauthorized or malicious applications directly from your SaaS provider.
- Enforce policy: Implement policies to alert on or block new third-party applications that do not meet your security standards.
Don't wait for the next supply-chain attack to reveal your security gaps. An application that passes an evaluation today might not pass tomorrow, making continuous monitoring essential. Gain the visibility you need to proactively secure your SaaS ecosystem.
References
- https://support.netskope.com/s/article/Salesloft-Drift-Breach
- https://docs.netskope.com
- https://community.netskope.com
- https://www.salesloft.com/platform/drift
- https://help.salesloft.com/s/article/Integrating-Drift-with-Salesforce?language=en_US
- https://cloud.google.com/blog/topics/threat-intelligence/data-theft-salesforce-instances-via-salesloft-drift








